gateway
A gateway is a network node used in telecommunications that connects two networks with different transmission protocols together. Gateways serve as an entry and exit point for a network as all data must pass through or communicate with the gateway prior to being routed. In most IP-based networks, the only traffic that does not go through at least one gateway is traffic flowing among nodes on the same local area network (LAN) segment. The term default gateway or network gateway may also be used to describe the same concept.
The primary advantage of using a gateway in personal or enterprise scenarios is simplifying internet connectivity into one device. In the enterprise, a gateway node can also act as a proxy server and a firewall. Gateways can be purchased through popular technology retailers, such as Best Buy, or rented through an internet service provider.
How gateways work
All networks have a boundary that limits communication to devices that are directly connected to it. Due to this, if a network wants to communicate with devices, nodes or networks outside of that boundary, they require the functionality of a gateway. A gateway is often characterized as being the combination of a router and a modem.
The gateway is implemented at the edge of a network and manages all data that is directed internally or externally from that network. When one network wants to communicate with another, the data packet is passed to the gateway and then routed to the destination through the most efficient path. In addition to routing data, a gateway will also store information about the host network’s internal paths and the paths of any additional networks that are encountered.
Gateways are basically protocol converters, facilitating compatibility between two protocols and operating on any layer of the open systems interconnection (OSI) model.
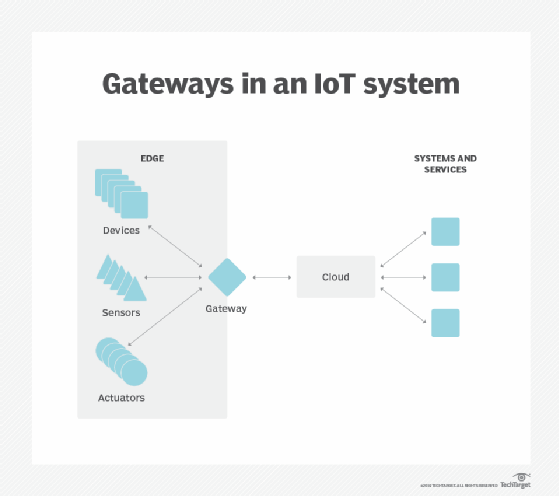
Types of gateways
Gateways can take several forms and perform a variety of tasks. Examples of this include:
- Web application firewalls- This type filters traffic to and from a web server and looks at application-layer data.
- Cloud storage gateways- This type translates storage requests with various cloud storage service API calls. It allows organizations to integrate storage from a private cloud into applications without migrating into a public cloud.
- API, SOA or XML gateways – This type manages traffic flowing into and out of a service, microservices-oriented architecture or XML-based web service.
- IoT gateways-This type aggregates sensor data from devices in an IoT environment, translates between sensor protocols and processes sensor data before sending it onward.
- media gateways- This type converts data from the format required for one type of network to the format required for another.
- Email security gateways- This type prevents the transmission of emails that break company policy or will transfer information with malicious intent.
- VoIP trunk gateways- This type facilitates the use of plain old telephone service equipment, such as landline phones and fax machines, with a voice over IP (VoIP) network.
Additionally, a service provider may develop their own personal gateways that can be used by customers. For instance, Amazon Web Services (AWS) has an Amazon API Gateway that allows a developer to connect non-AWS applications to AWS back end resources.
Difference between a gateway and a router
Gateways and routers are similar in that they both can be used to regulate traffic between two or more separate networks. However, a router is used to join two similar types of networks and a gateway is used to join two dissimilar networks. Dissimilar could be used to describe networks that use different primary protocols.
Due to this logic, a router may be considered a gateway, but a gateway is not always considered a router. Routers are the most common gateway, used to connect a home or enterprise network to the internet.





