multifactor authentication
What is multifactor authentication?
Multifactor authentication (MFA) is an account login process that requires multiple methods of authentication from independent categories of credentials to verify a user's identity for a login or other transaction. Multifactor authentication combines two or more independent credentials -- what the user knows, such as a password; what the user has, such as a security token; and what the user is, by using biometric verification methods.
The goal of MFA is to create a layered defense that makes it more difficult for an unauthorized person to access a target, such as a physical location, computing device, network or database. If one factor is compromised or broken, the attacker still has at least one or more barriers to breach before successfully breaking into the target.
In the past, MFA systems typically relied on two-factor authentication (2FA). Increasingly, vendors are using the label multifactor to describe any authentication scheme that requires two or more identity credentials to decrease the possibility of a cyber attack. Multifactor authentication is a core component of an identity and access management framework.
Why is multifactor authentication important?
One of the biggest shortcomings of traditional user ID and password logins is that passwords can be easily compromised, potentially costing organizations millions of dollars. Brute-force attacks are also a real threat, as bad actors can use automated tools to guess various combinations of usernames and passwords until they find the right sequence.
Although locking an account after a certain number of incorrect login attempts can help protect an organization, hackers have numerous other methods for system access and carrying out cyber attacks. This is why a multifactor authentication process is so important, as it can help reduce security risks.
MFA authentication methods
An authentication factor is a category of credential used for identity verification. For MFA, each additional factor is intended to increase the assurance that an entity involved in some kind of communication or requesting access to a system is who -- or what -- it says it is. The use of multiple forms of authentication can help make a hacker's job more difficult.
The three most common categories, or authentication factors, are often described as something you know, or the knowledge factor; something you have, or the possession factor; and something you are, or the inherence factor. MFA works by combining two or more factors from these categories.
Knowledge factor
Knowledge-based authentication typically requires the user to answer a personal security question. Knowledge factor technologies generally include passwords, four-digit personal identification numbers (PINs) and one-time passwords (OTPs). Typical user scenarios include the following:
- Swiping a debit card and entering a PIN at the grocery checkout.
- Downloading a virtual private network client with a valid digital certificate and logging into the VPN before gaining access to a network.
- Providing answers to personal security questions -- such as mother's maiden name or previous address -- to gain system access.
Possession factor
Users must have something specific in their possession to log in, such as a badge, token, key fob or a mobile phone subscriber identity module (SIM) card. For mobile authentication, a smartphone often provides the possession factor in conjunction with an OTP app.
Possession factor technologies include the following:
- Security tokens, which are small hardware devices that store a user's personal information and are used to authenticate that person's identity electronically. The device may be a smart card or an embedded chip in an object such as a Universal Serial Bus (USB) drive or wireless tag.
- Software tokens, which are software-based security applications that generate a single-use login PIN. Software tokens are often used for mobile multifactor authentication, in which the device itself -- such as a smartphone -- provides the possession factor authentication.
Typical possession factor user scenarios include the following:
- Mobile authentication, where end users receive a code on their smartphone to gain or grant access -- variations include text messages and phone calls sent to a user as an out-of-band method, smartphone OTP apps, SIM cards and smart cards with stored authentication data.
- Attaching a USB hardware token to a desktop that generates an OTP and using it to log in to a VPN client.
Inherence factor
Any biological traits the user has that are confirmed for login. Inherence factor technologies include the following biometric verification methods:
- Retina or iris scan.
- Fingerprint scan.
- Voice authentication.
- Hand geometry.
- Digital signature scanners.
- Facial recognition.
- Earlobe geometry.

Biometric device components include a reader, a database and software to convert the scanned biometric data into a standardized digital format and to compare match points of the observed data with stored data.
Typical inherence factor scenarios include the following:
- Using a fingerprint or facial recognition to access a smartphone.
- Providing a digital signature at a retail checkout.
- Identifying a criminal using earlobe geometry.
User location is often suggested as a fourth factor for authentication. Again, the ubiquity of smartphones can help ease the authentication burden: Users typically carry their phones, and all basic smartphones have Global Positioning System tracking, providing credible confirmation of the login location.
Time-based authentication is also used to prove a person's identity by detecting presence at a specific time of day and granting access to a certain system or location. For example, bank customers cannot physically use their ATM card in the U.S. and then in Russia 15 minutes later. These types of logical locks can be used to help prevent many cases of online bank fraud.
What are the pros and cons of MFA?
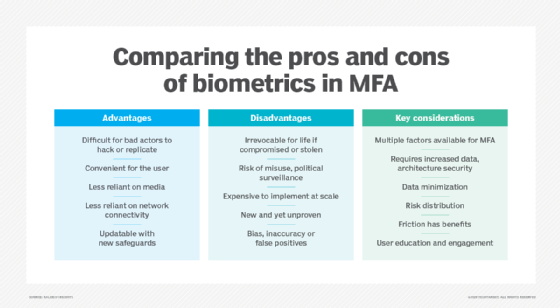
Multifactor authentication was introduced to harden security access to systems and applications through hardware and software. The goal was to authenticate the identity of users and to assure the integrity of their digital transactions. The downside to MFA is that users often forget the answers to the personal questions that verify their identity, and some users share personal ID tokens and passwords. MFA has other benefits and disadvantages.
Pros
- Adds layers of security at the hardware, software and personal ID levels.
- Can use OTPs sent to phones that are randomly generated in real time and are difficult for hackers to break.
- Can reduce security breaches by up to 99.9% over passwords alone.
- Can be easily set up by users.
- Enables businesses to opt to restrict access for time of day or location.
- Has a scalable cost, as there are expensive and highly sophisticated MFA tools but also more affordable ones for small businesses.
- Improves security measures and response for companies, as they can set up a multifactor authentication system to actively generate an alert whenever questionable login attempts are detected.
- Provides adaptive authentication, which helps with changing workplaces as more and more employees work remotely.
- Helps with meeting Health Insurance Portability and Accountability Act and compliance requirements, which require only authorized and restricted access to sensitive information, such as personal medical records.
Cons
- Requires a phone to get a text message code.
- Hardware tokens can get lost or stolen.
- Phones can get lost or stolen.
- The biometric data calculated by MFA algorithms for personal IDs, such as thumbprints, aren't always accurate and can create false positives or negatives.
- MFA verification can fail if there's a network or internet outage.
- MFA techniques must constantly be upgraded to protect against cybercriminals who work incessantly to break them.
Multifactor authentication vs. two-factor authentication
When authentication strategies were first introduced, the intent was to enforce security but to also keep it as simple as possible. Users were asked to supply only two forms of security keys that would inform a system that they were authentic and authorized users. Common forms of 2FA were user ID and password or automated teller machine (ATM) bank card and PIN.
Unfortunately, hackers quickly discovered ways to buy or break passwords or skim debit cards at ATMs. This prompted companies and cybersecurity vendors to look for more hardened forms of user authentication that used additional security factors for verification.
While MFA requires at least two authentication factors, if not more, 2FA only requires two. Therefore, all 2FA is MFA, but not the other way around.
What is adaptive multifactor authentication?
Adaptive multifactor authentication is a security approach that chooses which authentication factors to apply to a user's login attempt based on business rules and contextual information. It's also referred to as adaptive MFA or risk-based authentication.
Traditional MFA uses set credentials and a second factor, but adaptive MFA is a bit more advanced, as it automatically adapts authentication by considering several variables such as user location, device being used, number of failed login attempts, user behavior and environment. This strategy makes it harder for hackers to gain unauthorized access, since authentication is coordinated with the degree of risk.
Addressing the challenges of multifactor authentication
Users might be reluctant to adopt MFA, since it presents certain usability challenges such as remembering several passwords to log in. Along with user resistance, there could be other obstacles with MFA, including integration problems. Consequently, the goal of MFA is to simplify authentication for users.
The following four approaches are being used to simplify MFA:
- Adaptive MFA. As described above, this approach applies knowledge, business rules or policies to user-based factors, such as device or location. For example, a corporate VPN knows that it's OK for a user to sign on from home because it sees the user's location and can determine the risk of misuse or compromise. But an employee who accesses the VPN from a coffee shop will trigger the system and be required to enter MFA credentials.
- Single sign-on (SSO). This one-stop authentication method enables users to maintain one account that automatically logs them into multiple applications or websites with a single ID and password. SSO works by establishing the user's identity and then sharing this information with each application or system that requires it.
- Push authentication. This is an automated mobile device authentication technique where the security system automatically issues a third, single-use identification passcode or push notification to the user's mobile device. For example, users who want to access a secured system enter their user ID and password and a security system automatically issues a third, single-use identification code to their mobile device. Users enter that code into the system to gain access. Push authentication simplifies MFA by providing users with a third code, eliminating the need to remember it.
- Passwordless authentication. Passwordless authentication forgoes the use of conventional passwords in favor of additional authentication factors such as hardware tokens or biometrics, including fingerprints and face recognition. Remembering passwords is hard, so this makes it easier for users to authenticate as well as improves the security posture of an organization, as most phishing attacks target password vulnerabilities for unauthorized access.
While multifactor authentication enhances the security of usernames and passwords, its level of protection can vary depending on the chosen method. Discover five strategies to mitigate vulnerabilities in MFA.





