single sign-on (SSO)
What is single sign-on (SSO)?
Single sign-on (SSO) is a session and user authentication service that permits a user to use one set of login credentials -- for example, a username and password -- to access multiple applications. SSO is used by organizations of all sizes and individuals to ease the management of multiple credentials.
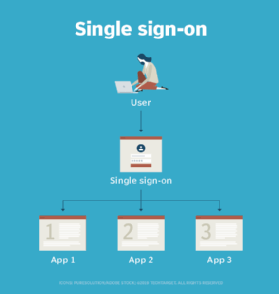
How does single sign-on work?
Single sign-on is a federated identity management arrangement. The use of such a system is sometimes called identity federation. Open Authorization (OAuth) is the framework that enables an end user's account information to be used by third-party services, such as Facebook, without exposing the user's password.
OAuth acts as an intermediary on behalf of the end user by providing the service with an access token that authorizes specific account information to be shared. When a user attempts to access an application from the service provider, the service provider sends a request to the identity provider for authentication. The service provider then verifies the authentication and logs the user in.
In a basic web SSO service, an agent module on the application server retrieves the specific authentication credentials for an individual user from a dedicated SSO policy server, while authenticating the user against a user repository, such as a Lightweight Directory Access Protocol directory. The service authenticates the end user for all the applications the user has been given rights to and eliminates future password prompts for individual applications during the same session.
Types of SSO configurations
Some SSO services use protocols, such as Kerberos or Security Assertion Markup Language (SAML):
- In a Kerberos-based setup, once user credentials are provided, a ticket-granting ticket (TGT) is issued. The TGT fetches service tickets for other applications the user wants to access, without asking the user to reenter credentials.
- SAML is an Extensible Markup Language standard that facilitates the exchange of user authentication and authorization data across secure domains. SAML-based SSO services involve communications among the user, an identity provider that maintains a user directory and a service provider.
- Smart card-based SSO asks an end user to use a card holding the sign-in credentials for the first login. Once the card is used, the user does not have to reenter usernames or passwords. SSO smart cards store either certificates or passwords.
Social SSO
Google, LinkedIn, Apple, Twitter and Facebook offer popular SSO services that enable end users to log in to third-party applications with their social media authentication credentials.
Many security professionals recommend end users refrain from using social SSO services because, once attackers gain control of a user's SSO credentials, they can access all other applications that use the same credentials.
Enterprise SSO
Enterprise single sign-on (eSSO) software and services are password managers with client and server components that log a user on to target applications by replaying user credentials. These credentials are almost always a username and password. Target applications do not need to be modified to work with the eSSO system.
SSO security risks
Although single sign-on is a convenience to users, it presents risks to enterprise security. An attacker who gains control over a user's SSO credentials is granted access to every application the user has rights to, increasing the amount of potential damage.
To avoid malicious access, SSO should be coupled with identity governance. Organizations can also use two-factor authentication (2FA) or multifactor authentication with SSO to improve security.
SSO advantages and disadvantages
Advantages of SSO include the following:
- Users need to remember and manage fewer passwords and usernames for each application.
- The process of authenticating with applications is streamlined -- no need to reenter passwords.
- Successful phishing attacks are reduced.
- IT help desks see fewer complaints or tickets regarding passwords.
Disadvantages of SSO include the following:
- It does not address certain levels of security each application sign-on might need.
- If availability is lost to apps that only allow SSO, users become locked out.
- If unauthorized users gain access, they could access more than one application.
SSO vendors
Multiple vendors offer SSO products, services and features. SSO vendors include the following:
- Rippling enables users to sign in to cloud applications from multiple devices.
- Avatier Identity Anywhere is SSO for Docker container-based platforms.
- OneLogin by One Identity is a cloud-based identity and access management platform that supports SSO.
- Okta is an enterprise tool with SSO functionality.
Editor's note: This article was written by Taina Teravainen in 2020. TechTarget editors revised it in 2024 to improve the reader experience.








