Web application firewall (WAF)
What is a web application firewall (WAF)?
A web application firewall (WAF) is a firewall that monitors, filters and blocks Hypertext Transfer Protocol (HTTP) traffic as it travels to and from a website or web application. A WAF can be network based, host based or cloud based. It is often deployed through a reverse proxy and placed in front of one or more websites or applications. Running as a network appliance, server plugin or cloud service, the WAF inspects each packet and uses a rule base to analyze Layer 7 web application logic and filter out potentially harmful traffic that can facilitate web exploits.
Web application firewalls are a common security control used by enterprises to protect web systems against zero-day exploits, malware infections, impersonation, and other known and unknown threats and vulnerabilities.
Through customized inspections, a WAF can detect and immediately prevent several of the most dangerous web application security flaws, which traditional network firewalls and other intrusion detection systems (IDSes) and intrusion prevention systems (IPSes) might not be capable of doing. WAFs are especially useful for companies that provide products or services over the internet, such as e-commerce shopping, online banking and other interactions between customers or business partners.
How does a WAF work?
A WAF can be software, an appliance or a service. It analyzes HTTP requests and applies a set of rules that define what parts of that conversation are benign and what parts are malicious.
The main parts of HTTP conversations that a WAF analyzes are GET and POST requests. GET requests are used to retrieve data from the server, and POST requests are used to send data to a server to change its state.
A WAF can take one of the following three approaches to analyze and filter the content contained in these HTTP requests:
- Whitelisting. The WAF denies all requests by default and allows only requests that are known to be trusted. It provides a list of the IP addresses that are known to be safe. Whitelisting is less resource-intensive than blacklisting. The downside of whitelisting is that it could unintentionally block benign traffic. While it casts a wide net and can be efficient, it can also be imprecise.
- Blacklisting. Blacklisting uses preset signatures to block malicious web traffic and protect vulnerabilities of websites or web applications. It's a list of rules that indicate malicious packets. Blacklisting is more appropriate for public websites and web apps because they receive a lot of traffic from unfamiliar IP addresses that aren't known to be either malicious or benign. The downside of blacklisting is that it's more resource-intensive and requires more information to filter packets based on specific characteristics, as opposed to defaulting to trusted IP addresses.
- Hybrid security. A hybrid security model uses elements of both blacklisting and whitelisting at the same time.
Regardless of the security model a WAF uses, it analyzes HTTP interactions and reduces or, ideally, eliminates malicious activity or traffic before it reaches a server for processing. To tackle new vulnerabilities, most WAFs require their policies to be updated regularly. However, recent advancements in machine learning have enabled some WAFs to update automatically.
Why is a WAF important?
A WAF is important for the growing number of enterprises that provide products over the internet -- including online banking, social media platform providers and mobile application developers -- because it helps prevent data leakage. A lot of sensitive data, such as credit card information and customer records, is stored in back-end databases that are accessible through web applications. Attackers frequently target these applications to gain access to the associated data.
Banks, for instance, might use a WAF to help them meet the Payment Card Industry Data Security Standard (PCI DSS), which is a set of policies to ensure that cardholder data (CHD) is protected. Installing a firewall is one of the 12 requirements of PCI DSS compliance and applies to any enterprise that handles CHD. Since many companies employ mobile applications and the growing internet of things, an increasing number of transactions take place at the application layer using the web. For this reason, a WAF is an important part of a modern business's security model.
When it comes to an enterprise security model, a WAF is most effective in conjunction with other security components, including IPSes, IDSes, and classic or next-generation firewalls (NGFWs).
Types of web application firewalls
The following are the three most common types of web application firewalls:
Network-based WAFs. These are usually hardware based and can reduce latency because they're installed locally on-premises via a dedicated appliance, as close to the application as possible. Most major network-based WAF vendors enable replication of rules and settings across multiple appliances, thereby making large-scale deployment, configuration and management possible. The biggest drawback of this type of WAF is cost -- there's an upfront capital expenditure as well as ongoing operational costs for maintenance.
Host-based WAFs. These can be fully integrated into the application code itself. The benefits of a host-based WAF include lower cost and increased customization options. But host-based WAFs can be challenging to manage because they require application libraries and depend on local server resources to run effectively. These WAFs might also require more staff resources -- including developers, system analysts, and DevOps or DevSecOps -- to manage.
Cloud-hosted WAFs. These offer a low-cost option for organizations that want a turnkey product that requires minimal resources for management. Cloud WAFs are easy to deploy, are available on a subscription basis, and often require only a simple domain name system (DNS) or proxy change to redirect application traffic. Although it can be challenging to place responsibility for filtering an organization's web application traffic with a third-party provider, this strategy lets applications be protected across a broad spectrum of hosting locations and use similar policies to protect against application layer attacks. Additionally, these third parties have the most current threat intelligence and can help identify and block the latest application security threats.
A WAF has an advantage over traditional firewalls because it offers greater visibility into sensitive application data that's communicated using the HTTP application layer.
Typically, WAFs offer the following features and protection against common attacks:
- Protection against web application attacks. WAFs can detect and mitigate common web application attacks such as SQL injection, cross-site scripting and buffer overflows by blocking or rate-limiting seemingly malicious incoming traffic.
- Monitoring and logging. Most WAFs offer detailed monitoring and logging capabilities, which are crucial in the investigation of potential security attacks. For example, Amazon Web Services offers various monitoring and logging options for its WAF resources, including AWS CloudWatch Alarms, AWS CloudTrail logs and AWS WAF web access control list traffic logging.
- AI-powered traffic pattern analysis. Certain WAFs are equipped to perform AI-based algorithms. They use behavioral baselines to detect malicious patterns and anomalies that signal a potential attack.
- Application profiling. WAFs can identify and deny potentially malicious requests through application profiling, which entails looking into an application's structure, including common queries, URLs, values and permitted data types.
- Content delivery networks (CDNs). Because WAFs are configured at the network edge, a cloud-hosted WAF can offer a CDN to cache the website and reduce load times. The WAF deploys the CDN over several internationally dispersed points of presence, serving site visitors from the closet site and reducing latency.
- Customization. Security rules can be applied to application traffic through a web application firewall. This lets organizations tailor the behavior of the WAF to their specific requirements and avoid blocking genuine traffic.
- Scalability and flexibility. Most WAFs are scalable and can tackle high-traffic websites and applications. They also provide a level of flexibility, as they can be deployed in a variety of configurations, including on premises or within cloud-based environments.
- Improved compliance. A WAF can help with compliance by adding an extra layer of defense against web application assaults that could reveal sensitive user data.
- Defense without access to source code. A WAF can defend web-based applications without accessing the source code of the application. While a host-based WAF can be integrated into application code, a cloud-hosted WAF can defend the application without having access. In addition, a cloud WAF is easy to deploy and manage, and it provides quick virtual patching options that let users rapidly customize their settings to adapt to newly detected threats.
WAF deployment methods
The following are the three most widely used WAF deployment techniques:
- Network-based WAF. Hardware is typically the foundation of a network-based WAF. Although these WAFs are the most expensive choice and necessitate the storage and upkeep of physical equipment, they minimize latency because they're installed locally.
- Host-based WAF. A host-based WAF is typically integrated into an application's software. It's less expensive than a network-based WAF and offers more customizability. However, it does come with a few drawbacks, such as the use of local server resources, administration difficulty and maintenance costs.
- Cloud-based WAF. The turnkey installation of cloud-based WAFs is as easy as making a change in the DNS to reroute traffic. Users of cloud-based WAFs incur few up-front expenses because they pay for security as a service on a monthly or annual basis. Cloud-based WAFs also offer a service that's continuously updated to protect against the most recent threats without requiring any further work by the customer. Because clients give up control to a third party when using a cloud-based WAF, they might not be aware of all of its features.
WAF examples
There are commercial and open-source WAF options. Given that commercial WAFs can be pricey, open-source WAFs can be useful if an organization is looking for a cost-effective way to secure their website.
Popular commercial vendors include the following:
- Barracuda. The Barracuda WAF guards against data leakage, application-layer denial of service (DoS) attacks and the top 10 web application security risks listed by the Open Web Application Security Project (OWASP). This WAF also defends APIs and mobile backends.
- Cloudflare. Cloudflare protects against critical web application attacks such as SQL injections, cross-scripting and zero-day attacks. Because it's a cloud-based WAF, it doesn't require any hardware or software installation for deployment.
- F5. This WAF protects web applications running on premises and in the cloud as well as virtualized and hybrid IT settings. Its browser-based interface supports network device configuration, centralized security policy management and straightforward audit results. In addition, it checks to ensure adherence to important legal requirements, such as the Health Insurance Portability and Accountability Act, PCI DSS and the Health Information Trust Alliance. It offers protection from both known and unknown vulnerabilities.
Popular open-source vendors include the following:
- ModSecurity. This WAF is offered by TrustWave and supports Apache, Nginx and Microsoft Internet Information Services (IIS). The free rules offered by ModSecurity are helpful against certain attacks, including cross-site scripting, trojans, SQL injection and information leakage.
- Naxsi. Nginx Anti XSS and SQL Injection is a WAF primarily for Nginx servers; it mitigates cross-scripting and SQL injection attacks.
- WebKnight. This WAF offered by Aqtronix supports Microsoft IIS and works as an OWASP Enterprise Security API filter that secures web servers by blocking bad requests. It's also useful against SQL injections, zero-day attacks, buffer overflows, hotlinking, and brute force and character encoding attacks.
WAF vs. IPS vs. NGFW vs. RASP: What are the differences?
Security technologies -- including WAFs, IPSes, NGFWs and Runtime Application Self Protection (RASP) -- are used to safeguard systems and networks. However, their approaches to security and the type of threats they mitigate, are different.
The following highlights the main differences among these technologies:
- WAF. This is specifically designed to safeguard web applications and ensure the integrity, confidentiality and availability of web services. It protects against web application attacks such as SQL injections and cross-site scripting attacks. It is typically placed between the internet and a web application to filter out malicious traffic.
- IPS. This monitors network traffic and responds to potential threats by taking measures to prevent attacks from happening. It uses techniques such as signature-based detection, machine learning and behavioral analysis to identify and mitigate port scanning, DoS attacks and malware infections. An IPS is typically placed at the edge of the network.
- NGFW. This integrates multiple security functions, including firewalls, virtual private networks and intrusion prevention. It offers granular control over network traffic and can recognize and stop a variety of threats, including malware, phishing scams and data exfiltration. An NGFW is also equipped with features such as Secure Sockets Layer decryption, application control, deep packet inspection and intrusion prevention.
- RASP. This is a security technology that's typically embedded within an application, designed to protect against attacks that target the application's runtime environment. It can identify and stop attacks in real time without the need for outside security tools. RASP can defend against a variety of threats, including buffer overflows, SQL injection and cross-site scripting.
WAF vs. firewall
Firewall is a broad term for firmware that defends a computer network by filtering incoming data packets. Within that broad definition, there are several categories that are differentiated by what kind of protection they provide and how they provide it. Some of those designations include packet filtering, stateful inspection, proxy and NGFW.
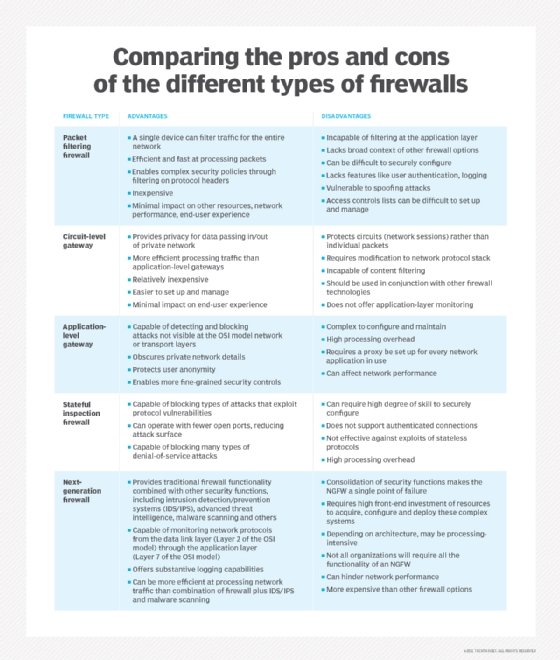
A WAF is another category of firewall, differentiated by how it specifically filters data packets. The WAF is unique because it focuses solely on web-based hackers at the application layer, whereas other types of firewalls -- such as packet filtering and stateful inspection -- might not be able to defend against these attacks. A WAF is similar to a proxy firewall but with a specific focus on Layer 7 application logic.
The threat to mobile security is growing as remote work becomes more widespread. Find out what a mobile firewall is and how it can defend against certain threat vectors.








