spear phishing
What is spear phishing?
Spear phishing is a malicious email spoofing attack that targets a specific organization or individual, seeking unauthorized access to sensitive information. Spear phishing attempts are not typically initiated by random hackers, but are more likely to be conducted by perpetrators out for financial gain, trade secrets or military information.
Similar to emails sent in regular phishing attacks, spear phishing messages also appear to come from a trusted source. Phishing messages usually appear to come from a large and well-known company or website with a broad user base, such as Google or PayPal. In the case of spear phishing, however, the source of the email is likely to be an individual within the recipient's own company, generally, someone in a position of authority or someone the target knows personally.
Many enterprise employees are taught to be suspicious of unexpected requests for confidential information. They are also instructed not to divulge personal data in response to emails or click on links in messages unless they are confident about the source. The success of spear phishing depends upon the following three things:
- the source appears to be known and trusted;
- the information within the message supports its validity; and
- the request the individual makes seems to have a logical basis.
How does spear phishing work?
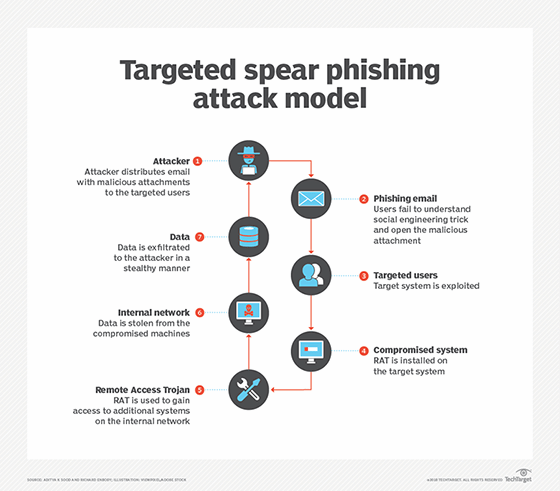
Familiarity is what makes spear phishing attacks successful. Attackers collect information over the internet and from social networks and social media sources about potential targets, including their personal and professional relationships and other personal details. The attacker uses this information to craft a personalized message that appears authentic to convince the target to respond to the sender's request. The sender may request a direct email response from the user, or the message may be a scam or include a malicious link or attachment that installs malware on the target's device. Clicking on the link or attachment directs the target to a malicious website designed to trick them into sharing sensitive information, like passwords, account information or credit card information.
Social media is fertile ground for spear phishers. Hundreds of thousands of users routinely share personal information, making it an ideal place to gather information about potential targets. But not every user is a target for spear phishers. Instead, bad actors look for information about individuals of high value. Typically, this sensitive information includes Social Security numbers, passwords to bank accounts and other elements of identity theft that provide information the spear phisher needs to access the target's accounts or commit crimes by using their stolen credentials.
To identify high-value individuals on social media, spear phishers use sophisticated machine learning algorithms that study patterns of text and other details available on social media sites. The technology narrows down the funnel of spear phishing targets to a subset of individuals who most closely match the type of target that the spear phisher is after.
Once the subset of high-value targets is isolated, the spear phisher sends an email that is convincing enough to get the target to open an attachment containing embedded malware that captures personal information.
How do you identify a spear phishing attack?
Spear phishing techniques can be more difficult to identify than phishing attacks due to the personal details in the messages that give them an air of validity. However, some of the characteristics that are common to phishing emails are also common to spear phishing emails, for example:
- The sender's email address is spoofed.The email address looks like it is from a trusted individual or domain, but closer inspection reveals a typographical error or the exchange of one alphanumeric character for another that closely resembles it, such as the letter I replaced with the numeral 1.
- There's a sense of urgency, particularly as it relates to performing a task that goes against company policy. Attackers evoke a sense of urgency to exploit the recipient's desire to do good or be helpful. For example, posing as the target's direct supervisor, an attacker may request the username and password for an internal application in order to fulfill an urgent request from upper management in a timely manner, rather than wait for the information technology (IT) team to reset their password.
- Poor grammar, typographical errors or unlikely language appear within the body of the message. The message content does not sound like other messages from the supposed sender. The tone is too informal, or the jargon is incorrect for the recipient's geographic location or industry.
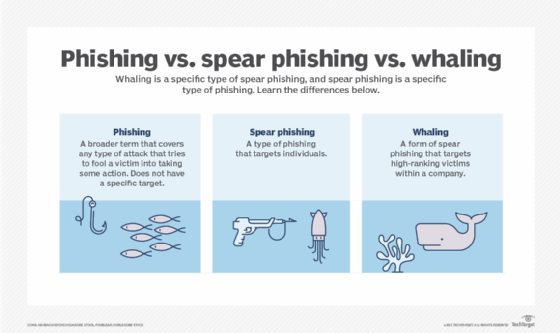
Spear phishing vs. phishing vs. whaling
Spear phishing and phishing have the same goal, but spear phishing attacks are more targeted. While phishing emails are sent to a large group of people, spear phishing emails are sent to a select group or an individual. By limiting the targets, it is easier for the spear phisher to include personal information -- like the target's first name or job title -- and make the malicious emails seem trustworthy.
The same personalized technique is used in whaling attacks. A whaling attack is a spear phishing attack directed at high-profile targets, like C-level executives, politicians and celebrities. Whaling attacks are also customized to the target and use the same social engineering, email spoofing and content spoofing methods to access sensitive data.
What are examples of successful spear phishing attacks?
A bad actor identifies the company website or webpages of the target organization that include contact information for the company. Using available details to make the message seem authentic, the perpetrator drafts an email to an employee on the company contact page that appears to come from an individual who might reasonably request confidential information, such as a network administrator. The email asks the employee to log in to a bogus page that requests the employee's username and password or click on a link that will download spyware or other malicious programming. If a single employee falls for the spear phisher's ploy, the attacker can masquerade as that individual and use social engineering techniques to gain further access to sensitive data.
In December 2020, Elara Caring, a U.S. healthcare provider, was hit with an unauthorized computer intrusion that targeted two employees. The spear phisher gained access to these employees' email accounts and obtained names, birthdates, financial and bank information, Social Security numbers, driver's license numbers and insurance information from over 100,000 elderly patients.
In 2021, Tessian, an email security company, reported that 75% of the organizations it had surveyed had experienced a spear phishing attack and 96% reported that the attacks came through email.
How to defend against spear phishing attacks
Businesses and their employees can make it more difficult for spear phishers to execute a successful attack by doing the following:
- Limit the amount of personal information shared on social media and other websites.
- Do not click on links in emails. Identify suspicious links by hovering the cursor over the link to see that the URL matches the link's anchor text and the email's stated destination.
- Contact the sender of the message using a separate communications channel to confirm the request.
- Use analytics to assess at least 12 months of company inbound email history. Analytics software inspects email content, tracks suspicious email traffic to specific users or user areas, and also assesses user behavior with emails. By looking at historical data, companies can determine how to improve security.
- Security awareness training for employees and executives can help reduce the likelihood of a user falling for spear phishing emails. This training typically educates employees on how to spot phishing emails based on suspicious email domains, links enclosed in the message, the wording of the messages and the information requested in the email. All company employees are also made aware of the process for reporting suspicious emails to the IT security team.
- Security teams can create and present their own training materials or purchase training materials from vendors. The most effective security awareness training includes simulated spear phishing attacks that enable users to practice their threat detection skills in the normal course of a workday. Security teams measure the effectiveness of training based on the results of these tests.
- An outside audit is also helpful, and most audit firms now offer social engineering audits that assess how internal employees behave with critical information and IT assets. Because of the widespread use of spear phishing and other types of malicious activity, it is advisable for IT or the security team to budget for a corporate-wide social engineering audit from an independent audit firm at least biannually. An outside audit will expose any holes in corporate security and employee security behavior so that vulnerabilities can be remedied.
- Enterprises should ensure that their security software, such as spam filters, antivirus software, and other advanced threat protection and security software, is kept up to date.
Learn which techniques and detection tips can help employees avoid phishing attacks.






