
Getty Images/iStockphoto
How to select a security analytics platform, plus vendor options
Security analytics platforms aren't traditional SIEM systems, but rather separate platforms or a SIEM add-on. Learn more about these powerful and important tools.
IT security pros use a variety of tools to gather timely and actionable information about threat actors that enables them to proactively combat an ever-growing variety and frequency of cyber attacks.
One key tool that can help security teams handle this task is a security analytics platform. Let's examine these tools, why they're important, what they do and how to evaluate them, as well as a list of products to consider.
What is a security analytics platform?
Basic cybersecurity threat analytics uses system log analyzers and network traffic monitoring tools that connect to network elements using pipelines. These technologies examine network traffic passing through access devices, gather traffic data and compare that traffic data to rules and other parameters stored in the system. If suspicious data packets are identified, the tools flag the anomalies via alarms and system dashboard messages.
The next level of cybersecurity analysis is SIEM, which uses powerful algorithms and other tools to provide additional assessments on suspicious traffic. SIEM systems offer recommendations based on preprogrammed messages that are presented with the traffic analysis.
The highest level of cybersecurity threat assessment tools is a security analytics platform. Using advanced programming with AI and machine learning, security analytics tools perform further capabilities, such as user entity and behavior analytics (UEBA), to give security analysts greater insights on threat sources and threat behavior, as well as what a threat may do next. Security analytics platforms also offer recommendations based on the behavior analysis, including preemptive actions to reduce the attack surface and how to mitigate event severity if an attack occurs.
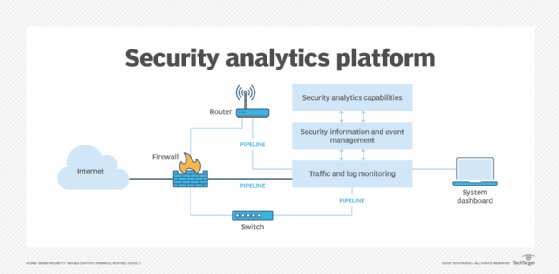
Cybersecurity analysis tools can connect to almost any networking device. In Figure 1, they are connected to a firewall, router and network switch. These tools can be programmed to monitor traffic and identify and flag anomalies based on their internal database of threat vectors. As more data and incident management processes are needed, a SIEM system can be layered onto the base system.
If the frequency and severity of attacks increase, a security analytics platform can be added. The security analytics tool collects information from the other two levels and performs more sophisticated analyses using AI to examine the data and generate more detailed insights and recommendations.
Many products on the market today offer combinations of the three levels of security analysis.
Why are security analytics tools important?
Cybersecurity management is an ongoing cat-and-mouse game. Security software developers constantly work to identify new threat actors and malicious code and then develop mitigation and remediation for them. Simultaneously, threat actors constantly develop new malware techniques and malicious code to bypass firewalls and other network defenses to cause damage to internal networks, systems and data.
Protecting valuable business-critical company data, as well as personally identifiable information and personal health information, is critical. Investing in a powerful cybersecurity analytics platform is one of the most important budget items for IT departments in 2023 and beyond. While the costs of a security analytics tool may be prohibitive for smaller businesses, large IT departments should not exist today without one.
Applications for security analytics platforms
Security analytics tools are built to prevent cyber attacks. They examine network security data in great detail using specialized analytical engines based on AI. One of the tool's main functions is behavior analysis, which examines event data in various contexts to look for the following:
- specific patterns in how the attacks were prosecuted;
- what resources were attacked and how; and
- what post-event trails exist that could provide additional insights on the perpetrator.
Security analytics platforms use AI to also provide recommendations for fixing vulnerable devices and systems and preventing future attacks.
Additional activities that can be performed by security analytics platforms include the following:
- vulnerability scanning and assessments
- penetration tests and threat hunting
- cyber incident response activities
- compliance assessments
- endpoint detection and response
How to select an effective security analytics platform
Most established organizations have cybersecurity prevention, detection and mitigation technologies in use. Organizations with basic security analysis tools may want to upgrade to a more powerful option based on the number and severity of cyber attacks faced.
Look for a platform that starts at a basic level and has the capability to add more powerful modules. Switching vendors may necessitate a learning curve to get up to speed. As with any IT investment, follow these steps:
- Determine the situation -- for example, an existing system needs to be upgraded.
- Advise management of the need for a cybersecurity analytics tool. Secure management approval and funding.
- Research the market and vendors for available products and services. Decide on a deployment model -- on-premises, cloud-based or managed service.
- Take advantage of free trials.
- Identify prospective candidates with flexibility among their products, compliance with standards and ability to integrate into existing infrastructures.
- Examine pricing options. Note that most products have a flexible pricing structure based on the number of gigabytes of data analyzed per month. Some products have an upfront cost plus back-end usage and maintenance costs.
- Examine candidate system capabilities based on current and projected needs.
- Determine the learning curve employees may be facing with a new vendor's system. Ask the vendor if training is available.
- Examine the amount of data and reporting displayed in a candidate's dashboard.
- Consider the levels of analytics performed by the product, the kinds of reports generated and any additional added-value deliverables.
- Determine how much user interaction is possible with systems, especially those that are cloud-based.
- Examine additional services offered by the vendor, such as vulnerability and pen testing, incident response support and cybersecurity plan development assistance.
- Look at services that address compliance testing and validation of compliance with cybersecurity standards.
- Utilize the systems development lifecycle during the planning and implementation phases.
- Review the training and documentation provided, along with system implementation and acceptance testing support.
10 security analytics platforms to consider
Organizations that want to maximize their event detection and remediation capabilities to address a broad spectrum of potential cyber attacks can benefit from a security analytics tool. Many tools combine log management and SIEM functions into a single security platform, while others offer add-on security analytics capabilities.
Security analytics tools provide strong analysis and reporting capabilities, but they come at a price. The right tool provides greater visibility into network operations, while minimizing wasted time chasing false alarms.
The following are 10 cybersecurity tools and platforms that offer security analytics capabilities -- check with the vendor for pricing:
- Splunk Enterprise Security is a SIEM platform with many advanced features. It is offered as a value-add to Splunk Cloud Platform and Splunk Enterprise.
- Pros: Powerful system; many features and dashboards.
- Cons: Learning curve.
- SolarWinds Security Event Manager is SIEM software.
- Pros: Efficient data collection; dashboards; compliance reporting.
- Cons: Learning curve.
- IBM Security Guardium is a data protection platform designed for large corporate network requirements.
- Pros: Security analytics features; dashboards; compliance features.
- Cons: Learning curve.
- LogRhythm SIEM is a SIEM platform that offers a security analytics layer.
- Pros: Advanced security analytics capabilities; dashboards.
- Cons: Learning curve; upgrade process.
- Securonix Next-Gen SIEM has advanced features, including security analytics capabilities.
- Pros: Security analytics support; dashboard; reporting.
- Cons: None identified.
- Exabeam Fusion is a SIEM platform with advanced features, including security analytics.
- Pros: Security analytics capabilities; available for on-site and cloud-based installations.
- Cons: None identified.
- Microsoft Azure Advanced Threat Protection (ATP) superseded Advanced Threat Analytics and is an enterprise-level on-premises and cloud platform with advanced security analytics features that provide end-to-end security anomaly investigation and analysis.
- Pros: Security analytics capabilities; enterprise applications; on-premises and cloud deployment; addresses endpoint issues by linking with Windows Defender ATP.
- Cons: Learning curve; upgrade process; additional cost.
- Sumo Logic Platform with Cloud SIEM and Cloud SOAR is a cloud-based platform with SIEM and security orchestration, automation and response features.
- Pros: Security analytics capabilities; scalability; reporting.
- Cons: None identified.
- Forcepoint Behavioral Analytics is a platform that features UEBA capabilities.
- Pros: Advanced security analytics capabilities.
- Cons: None identified.
- Rapid7 InsightIDR is a cloud-based SIEM platform with UEBA capabilities.
- Pros: Security analytics capabilities; dashboards; reporting.
- Cons: None identified.








