
business impact analysis (BIA)
What is business impact analysis (BIA)?
A business impact analysis (BIA) is a systematic process to determine and evaluate the potential effects of an interruption to critical business operations as a result of a disaster, accident or emergency. An organization will often use the data from a BIA when developing a business continuity plan (BCP) or disaster recovery plan (DRP).
The BIA process results in a report that documents the BIA's findings. The report contains an exploratory component describing potential threats and vulnerabilities specific to the organization being studied. It then provides a planning component that describes strategies for minimizing the impact of unplanned events. The analysis operates under two basic assumptions:
- Every operation of the organization relies on the continued functioning of all the other operations.
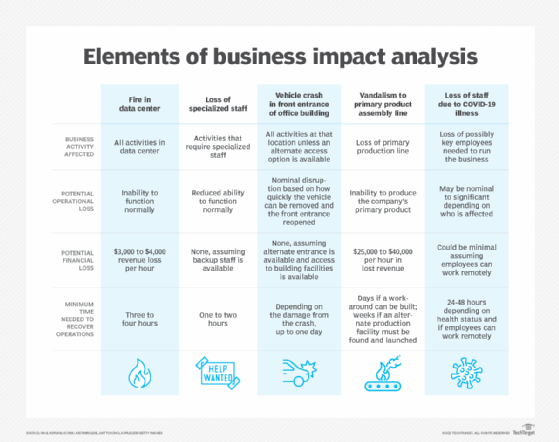
- Some operations are more crucial than others and require a greater allocation of funds and operational resources in the event of a disaster. For example, a business will likely be able to continue more or less normally if the cafeteria needs to close, but it would come to a halt if the information systems and IT infrastructure crash.
How to conduct a BIA
The International Organization for Standardization (ISO) offers guidelines for implementing and maintaining a formal and documented BIA process. The guidelines are published in ISO/TS 22317:2021, Security and resilience -- Business continuity management systems -- Guidelines for business impact analysis. ISO/TS 22317:2021 is a technical specification (TS) available to any type or size organization, which can adapt the guidelines to its own circumstances.
ISO/TS 22317:2021 does not define a uniform process for performing a BIA, so methodologies often vary from one organization to the next. Even so, the process commonly includes the following steps:
- Prepare for the BIA project. A BIA effort should be treated much like any other project. Those who are leading the project planning effort should secure approval for the project from senior management and then prepare a detailed BIA plan. They should also form a team of trained individuals to perform the BIA. The team might be made up of internal personnel, outside consultants or a combination of both. Some organizations conduct an educational session for key personnel with knowledge of the business. This can help prepare them for the BIA process and the information gathering that goes with it. The preparation stage is also a good time to review ISO/TS 22317:2021.
- Gather information relevant to the analysis. There is no one approach to gathering information. The team might send out questionnaires, conduct in-person interviews or review existing documentation. Team members should collect a variety of information, including specific details about mission-critical applications and business processes, the resources required to support those processes and the dependencies among participating entities. This includes internal and external dependencies, as well as relevant inputs and outputs. This information is essential in assessing the potential impact of a disruptive event.
- Evaluate and analyze the gathered data. Team members should review the collected data to ensure that they have everything they need to understand and prioritize business functions. Follow-up interviews or other communications might be necessary. Once team members are confident they have the data they need, they can start analyzing the data to identify critical business processes and the technologies those processes depend on. They should then determine what the impact would be if those processes cannot be performed, using performance metrics, such as recovery time objective (RTO), recovery point objective (RPO) and maximum tolerable downtime (MTD). The analysis process might be manual or computer-assisted.
- Prepare a report to document findings. The report typically includes an executive summary, information on the methodology for data gathering and analysis, detailed findings on the various business units and functional areas, charts and diagrams to illustrate potential losses and recommendations for recovery. The report prioritizes the most important business functions, examines the impact of business interruptions, specifies legal and regulatory requirements, details acceptable levels of downtime and losses, and lists RTOs, RPOs and MTDs. The report might also list the order of activities necessary to restore the business, minimum number of personnel needed to recover operations, approximate funds needed for recovery and whether the recovery will occur at the original location or an alternate site.
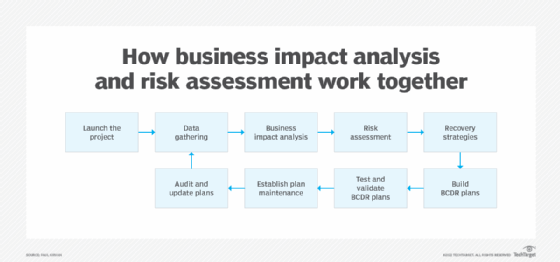
- Present the results to senior management. After the report is completed, the BIA team typically meets with senior managers to discuss their findings. The team might provide the report at this time or send it beforehand to better prepare the participants. The managers review the report and, if approved, use it to develop the BCP and DRP. The BIA report is often used in conjunction with a risk assessment (RA) to help define strategies for recovery and restoration of mission-critical processes.
The BIA team, managers or other designated individuals should review and update the BIA data at least annually, as well as whenever a significant change in business operations occurs.
What is the objective of the BIA?
A business impact analysis serves many purposes. It identifies the business functions, systems, staff and technology resources most crucial for operations to run optimally. It also describes the effects or consequences of an interruption to critical business functions, and it attempts to quantify the financial and nonfinancial costs associated with the disaster. In addition, a BIA estimates how long it should take to recover each business function to avoid any significant impacts on operations.
Each BIA is unique to its specific circumstances. For example, a BIA for an IT department might start by identifying the applications supporting essential business functions. It will then describe the interdependencies between existing systems, possible single points of failure and the costs associated with system outages. The BIA examines IT-related risks and prioritizes uptime requirements, using metrics such as RTO, RPO and MTD.
Conducting a BIA is not without its challenges. For example, it can sometimes be difficult to determine the full revenue impact of a business disruption or quantify the long-term consequences of losses in market share, business reputation or customers. A business disruption might impact an organization in a variety of ways, including the following:
- Delayed sales or income.
- Increased labor expenses.
- Regulatory fines.
- Contractual penalties.
- Customer dissatisfaction.
Despite these challenges, a BIA can still be a valuable tool for a wide range of organizations, especially as they prepare their BCPs and DRPs. However, BIA reports must be comprehensive and highly accurate, which is why many organizations turn to resources to help with the process, such as:
- Consultants. Third-party consultants who specialize in BIA can be very useful to organizations that lack in-house expertise. When hiring a consulting firm, however, the organization should verify that the firm's team members have demonstrable experience performing BIAs.
- BIA software. The proper application can streamline and simplify the BIA process, while helping to ensure accuracy and consistency. BIA capabilities are often provided as a module within a larger, more comprehensive application.
- Business continuity as a service. BCaaS offers many of the advantages typical of cloud-based platforms. They eliminate the need to deploy software in-house, make it quicker and easier to get started, and can be accessed from just about anywhere at any time. Such services often include a BIA component that simplifies the analytics process.
The role of the BIA in disaster recovery planning
A disaster recovery plan is a structured document that describes how an organization can quickly resume work after an unplanned incident disrupts normal operations. The DRP typically incorporates data from a BIA, including the costs associated with operational disruptions. The costs can reflect situations such as loss of cash flow, equipment replacement or salaries paid to catch up with work backlogs. They might also include loss of profits, staff or data.
The BIA data used in the DRP quantifies the importance of business components and suggests appropriate fund allocations for protecting them and the technology supporting them. Possible disruptions are often assessed in terms of their effects on specific business concerns, such as safety, finances, marketing, reputation, legal compliance or quality assurance.
Where possible, impact and recovery are expressed monetarily for purposes of comparison. For example, a business might budget three times the normal amount for marketing to rebuild customer confidence after a disaster. The BIA should assess a disaster's impact over time and establish recovery strategies, priorities and requirements for resources and time. All of that information can then be used in the DRP.
The role of the BIA in business continuity planning
An organization often conducts a BIA to provide data for both a DRP and a BCP. A business continuity plan is a document that contains the critical information an organization needs to continue operating during an unplanned event. It identifies business functions, which systems and processes must be maintained, and how to go about maintaining them.
The BCP often uses data from a BIA. The data identifies the organization's critical business processes, the technologies needed to support them, the personnel necessary to recover the business and the facilities required to support the business -- information that is essential to developing a comprehensive BCP. Ideally, the BC and DR plans should complement each other, unless, for example, management wishes to focus on protecting the technology, with less concern about business processes.
BIA vs. risk assessment
A risk assessment is sometimes confused with a BIA, but the two are fundamentally different. An RA identifies inherent business risks and how to reduce the impact of these risks on business operations.
Risks can include natural disasters (such as hurricanes or earthquakes), fires, supply chain failures, power or other utility outages, cyberattacks and much more. The RA describes the key areas of vulnerability and points of weakness.
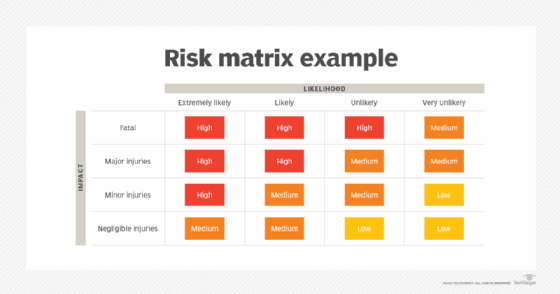
In contrast, a BIA focuses on the organization's critical business processes and the resources needed to support them. Both the RA and BIA are essential to developing comprehensive and accurate BC and DR plans.

Some organizations perform the BIA before the RA, while others prefer to carry out the RA first. In either case, they both precede the BCP and DRP. Together, the BIA and RA serve as a starting point for the larger BC and DR efforts. They can be instrumental in analyzing the impact of RTOs and RPOs and identifying the resources and materials needed for business recovery and resumption.
Learn more about risk assessments, and get a free, downloadable risk assessment template.






