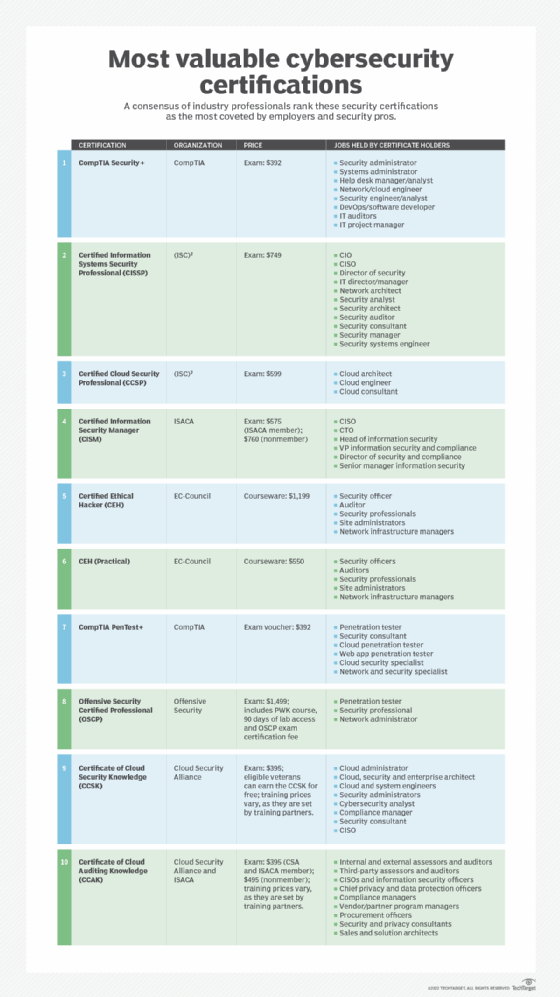
Certified Information Security Manager (CISM)
What is Certified Information Security Manager (CISM)?
Certified Information Security Manager (CISM) is an advanced certification that indicates that an individual possesses the knowledge and experience required to develop and manage an enterprise information security (infosec) program.
CISM is offered by ISACA, a nonprofit, independent association that advocates for professionals involved in infosec, assurance, risk management and governance.
The CISM certification is intended for infosec managers, aspiring managers or IT consultants who support infosec program management. It is accredited by the American National Standards Institute under ISO/IEC 17024:2003.
How to become a CISM
The CISM certification process includes a 150-question, multiple-choice exam that is scored using a 200-800 scaled scoring method; 450 is a passing score, indicating the individual meets a minimum consistent standard of knowledge set by the ISACA Certification Committee.
The exam covers the following four content areas:
- Information Security Governance.
- Information Risk Management.
- Information Security Program Development and Management.
- Information Security Incident Management.
CISM prerequisites
To qualify for the exam, applicants must have five years of verified experience in the infosec field, with a minimum of three years of infosec management experience in three or more of the CISM content areas.
Experience must be gained within a 10-year period preceding the application date or within five years from the date of passing the exam.
Maintaining CISM certification
To maintain CISM certification, individuals must sustain an adequate level of knowledge and proficiency in the field of information systems security management, complete 20 continuing professional education hours annually and follow ISACA's Code of Professional Ethics.







