Hacking Web Intelligence
In this excerpt from chapter 8 of Hacking Web Intelligence, authors Sudhanshu Chauhan and Nutan Panda discuss how to be anonymous on the internet using proxy.

The following is an excerpt from Hacking Web Intelligence: Open Source Intelligence and Web Reconnaissance Concepts and Techniques by authors Sudhanshu Chauhan and Nutan Panda and published by Syngress. This section from chapter 8 explores anonymity with a proxy.
There are many ways to be anonymous and there are many aspects of being anonymous. Some might focus on the personal details to be hidden such as in social networking sites by using aliases, generic information or fake information, generic e-mail id, and other details. Some might want to be anonymous while browsing so that nobody can track what resource they are looking into. Some might want to hide their virtual identity address such as IP address etc.
There are different ways to achieve the above conditions. But the major and popular solutions available are either proxy or virtual private network (VPN). Though there are other methods to be anonymous but still these two are widely used and we will focus on these majorly in this chapter.
PROXY
Proxy is a word generally used for doing stuffs on behalf of someone or something. Similarly in technology, proxy can be treated as an intermediate solution that forwards the request sent by the source to the destination and collects response from the destination and sends it to the source again.
It is one of the widely used solutions used for anonymity. The only reason to use proxy is to hide the IP address. There are different proxy solutions available such as web proxy, proxy software etc. Basically all the solutions work on a basic principle to redirect traffic to the destination from some other IP address. The process might differ from solution to solution but the bottom line remains the same.
Though proxy can be used for many other purposes just apart from being anonymous, we will focus only the anonymity as the chapter demands the same.
Before focusing into the very deep technical aspects of proxy let's look into some work around to be anonymous. As in earlier chapters we learned how to use search engines efficiently and power searching. Now it's time to look into how a search engine can be used as a proxy to provide anonymity.
As Google is a popular search engine it can also be used as proxy with its feature called as Google Translate. Google provides its services in many countries apart from the English speaking ones and it also supports multiple languages. The Google Translate option allows a user to read web content in any other language a user wants. For a generic example, a non-English content can be translated to English and vice versa. So this feature allows a user to use Google server to forward the request and collect the response on his/her behalf, which is the basic fundamental of a proxy.
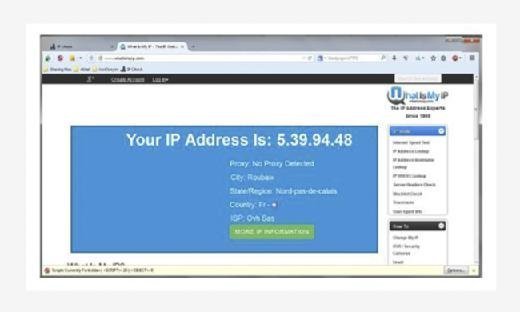
Now for testing the same, first we will look into our own IP address using a site called http://whatismyipaddress.com/ and later use Google translator to check the same site. The work of this site is to tell the IP address used to send the request to the site. If for the normal browsing and browsing through Google Translate the IP address differs, it means we achieved anonymity using Google Translate.
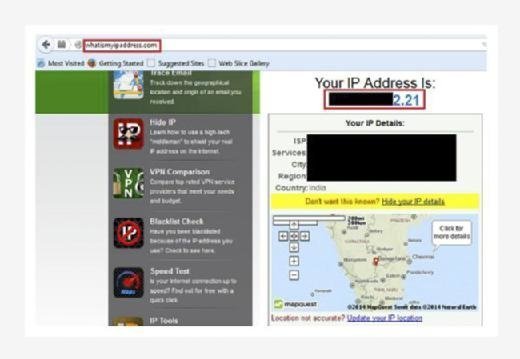
Now visit translate.google.com. Select any language in source and any other language in destination to translate this web page as shown in below image.
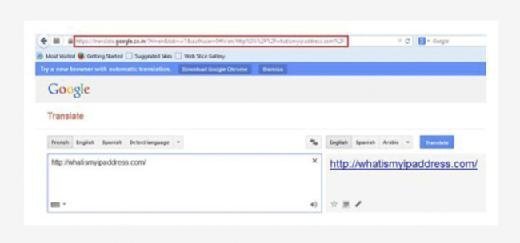
Now click on Translate to check the whether the IP address matches with the IP address disclosed in above image for direct browsing or not.
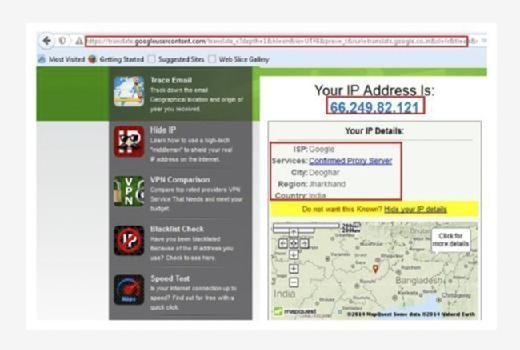
We can see from the above image that the IP addresses of direct browsing and of browsing using Google Translate are different. Thus it is proved that we can use Google Translate as proxy server to serve our purpose. In many cases it will work fine. Though it's just a work around it's very simple and effective. In terms of full anonymity it might not be helpful but still we may use this method where we need a quick anonymity solution.
PROXY IN TERMS OF ANONYMITY
As we came across one example where we can use search engine feature as proxy. But the point to be considered is anonymity. There are different levels of anonymity based on different proxy solutions. Some proxies just hide our details but keeping the same in their logs, and sometime some proxies can be detected as proxy by the server and some might not. That's not the best solution if you want full anonymity. There are some solutions available which cannot be detected as proxy by the destination server and also delete all the user details the time user ends the session. Those are the best solutions for full anonymity. It all depends on our requirement to choose what service or what kind of proxy we want to use because fully anonymous proxy might charge the user some amount to use the solution.
TYPES OF PROXY SOLUTIONS
Now there are different types of proxy solutions available some are based on anonymity and also based on its type such as whether application-based or web-based. So let's start exploring some of the available options in application-based proxy.
APPLICATION-BASED PROXY
Application-based proxy is just a software or tool which can be installed in our operating system to use it as proxy solution.
Ultrasurf
It is an application-based proxy solution which can be found at http://ultrasurf.us/. This is now available as Chrome plugin also. Though this is in beta stage if we are lazy to download and install it in our system and then use, we might use the Chrome plugin that will serve our purpose. The plugin can be found at https://chrome.google.com/webstore/detail/ultrasurf/mjnbclmflcpookeapghfhapeffmpodij?hl=en.
Let's first explore its plugin version then we will go deep in to the application version. The best part of this plugin is that it's simple to use and it supports many languages such as English, French, Portuguese, and Roman etc. Once the chrome plugin gets added in the browser, we will see its icon on the right top addon bar just in the right side of the address bar. When we have to use that just click on the icon, a small window will open then click on the switch available in that window to ON. Then the addon will connect to its server. Once it is connected to the server only then we can browse anonymous. In case of we forgot to switch on the addon or the addon is trying to connect to the server or the addon is unable to connect the server then all the thing we browse will be as normal browsing. So put it in mind to switch on and let it connect to the server before browsing or else all the anonymity process will go to vain.
The application version can be downloaded quite easily from the link http://ultrasurf.us/download/u.zip.
It's just a compressed file, extracting the file we can get the application. The best part of this process is that we need not to install the application. We can simply double click on that and that will configure the required settings in our system and let us browse anonymously. The default settings allow to open the Internet Explorer by double clicking the application. We can change the application settings using its options tab.
Though the tool was earlier developed for anticensorship protest in china, now it's used widely as a proxy solution. It not only just helps user to hide the details but also allows a user to communicate using encryption mechanism. This can be used in many different areas but the most general use can be while browsing using free Wi-Fi hotspot. Because in that case, there is a chance of rogue access point collecting all the information about us.
The main advantage of using this tool is connection speed. Generally when we use any kind of proxy solution as it redirects the traffic through that server the connection speed reduces drastically and user can feel that; but in this case it's very fast as compared to other proxy solutions. Apart from that we can see the connection speed in the tool itself and it provides three connection options, user can switch to any one of them any moment to avoid speed drop. To distinguish between normal browsing and browsing using Ultrasurf, this tool provides a cool lock symbol in the right corner of the browser to make sure that user is browsing anonymously.
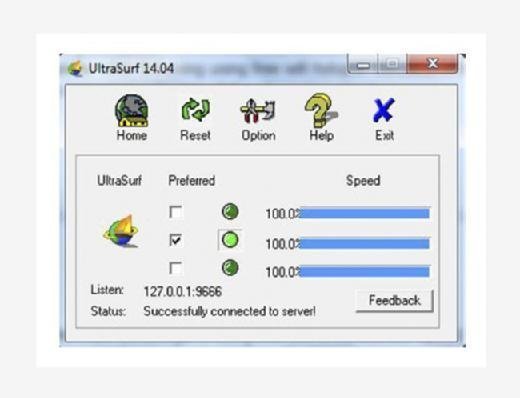
A small drawback about this tool is that this tool supports only Windows. And another drawback is that the IP-checking solutions detect it as proxy server. But as we discussed earlier, this can be used in different other conditions based on our requirements and it's easy to use. Just download, run, and browse anonymously.
JonDo
JonDo previously known as JAP is a proxy tool available at https://anonymous-proxy-servers.net/en/jondo.html.
It is available for wide range of operating systems such as Windows, Mac, for different flavors of Linux, and also for Android mobile. The full-fledged documentation of how to install and use makes it very essential as a proxy solution. Different proxy solutions come up with different types. It also provides one of its type for Firefox anonymous browsing known as JonDoFox.
Before exploring JonDo let's first look into the Firefox anonymous browsing solution i.e., JonDoFox. It can be found at https://anonymous-proxy-servers.net/en/jondofox.html.
Hacking Web Intelligence
Authors: Sudhanshu Chauhan and Nutan Panda
Learn more about Hacking Web Intelligence from publisher Syngress
At checkout, use discount code PBTY25 for 25% off this and other Elsevier titles
As JonDo, JonDoFox is also available for different operating systems such as Windows, Mac, and Linux. User can download as per his/her operating system from the above URL. The documentation of how to install is also available just next to the download link. But let's download and install while we discuss more about the same.
Windows users will get JonDoFox.paf after downloading. After installing the same it will create a Firefox profile in name of JonDoFox. If user selects the same, the profile consists of many Firefox addons such as cookie manager, adblocker, etc., which will come to act. But to use it for full anonymity user needs to install certain dependent softwares such as Tor etc.
It's good to use JonDoFox but user has to install all the dependent softwares once after installing the same. Some might not love to do so but still this is a great solution to browse anonymously.
Like JonDoFox, JonDo can also be downloaded from the above URL. It will give you the installer. Windows user will get an exe file "JonDoSetuup.paf" after downloading. The installation can be done for the operating system we are using and also for the portable version that can be taken away using the USB drive. User needs to choose according to his/her requirements. The only dependency of this software is JAVA. But as earlier we discussed how to install the same we are not going to touch that here again and by the way while installing this software it also installs JAVA, if it won't find the compatible version available in the operating system. Once JonDo is installed, we can double click on its desktop icon to open the same. By default after installation it creates a desktop icon and enables it to start in Windows startup.
JonDo only provides full anonymity and fast connection to premium users. But we still can use the same. But first time we need to activate it with its free code. Test coupon can be found at https://shop.anonymous-proxy-servers.net/bin/testcoupon?lang=en but we need to provide our e-mail address to get it.
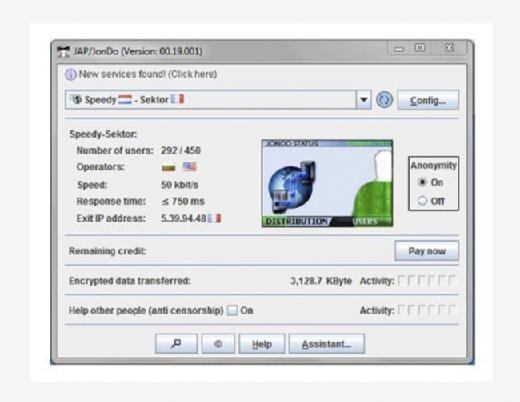
After providing the e-mail address we will get a link in our e-mail id. Visit the link to get the free code. Once we get the free code, put it in the software to complete the installation process.
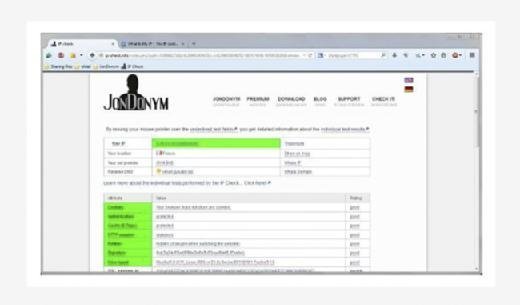
If you want to use JonDo you need to install JonDoFox also; as we already covered JonDoFox, we can assume that it is already present in the system. When both the softwares are installed in a system, if we want to use just JonDoFox then we can simply use that by opening Firefox with JonDoFox profile. To test whether we are browsing anonymously, we just need to check the IP address using whatismyipaddress.com.
If we want to use JonDo then we need to configure the same in the browser. In case of Mozilla go to Tools → Options → Advanced → Network → Connection Settings→ select Manual proxy configuration and use 127.0.0.1:4001 as the default port used by JonDo is 4001.
Once it's done, open Firefox with JonDoFox profile, we will see a JonDo icon in the top left corner. Click there and it will open a tab. Select "Test Anonymity" to check the IP address.
JonDo provides us with a set of proxy servers that can be changed quite easily from the dropdown box. So it is also known as JonDo the IP changer proxy solution.
As we already discussed about how to use JonDo and its paid solution for full anonymity. This tool has variety of features but the major one is its compatibility with different operating systems. This makes JonDo unique in proxy solutions.
WEB-BASED PROXY
Web-based proxy solutions are the simple and efficient way of getting anonymity. The best thing is that we can use them anywhere. No setup needed. No dependencies. Best to use when using a shared computer or in public computers for browsing and sometime when using open Wi-Fi connections. The simple user interface makes it very popular to use. Just open the browser and open the proxy, and you are good to go.
Read an excerpt
Download the PDF of chapter 8 in full to learn more!
There are many web-based proxy solutions. Some are just used for browsing and other may have more features like sending e-mails anonymously or reading news feeds. It's just depending upon our requirement and the anonymity level provided to choose a particular web-based proxy solution.
anonymouse.org
If user just wanted to browse anonymously there are different live anonymous browsing options available. One of such is anonymouse.org.
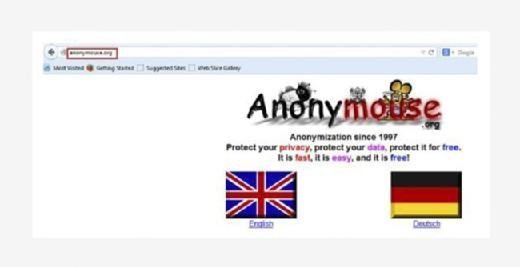
It is a free site which provides its users to browse anonymously with two different languages, English and Dutch. Visit the site, choose the language in which you want to browse then type the site name in the Surf anonymously field and click on Surf anonymously to browse the site.
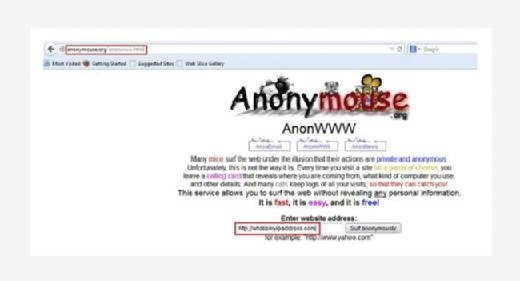
The only disadvantage of this site is it only supports http protocol not https. But apart from that it provides better anonymity as we can see from the below image, it's not detected as proxy server. And the IP address is also from a different location.
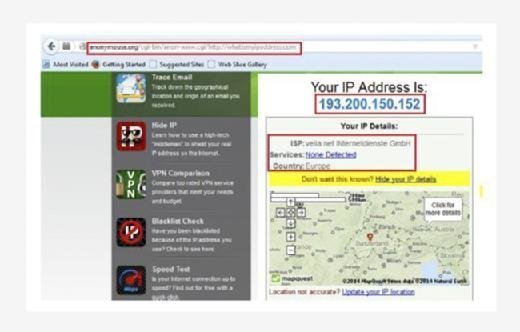
As we discussed the pros and cons of this service still it's very good proxy solution for anonymous browsing and there are some other features like send e-mail and check e-news available. But as we are more focused on hiding our details on browsing, right now we will conclude this here itself.
Zend2
It is also a web-based proxy solution unlike anonymouse.org, which only supports http protocol. So users cannot use anonymouse.org to browse popular sites such as Facebook and YouTube as these sites force to use https connection.
https://www.zend2.com/ has no restrictions on https-enabled sites or technically SSL-enabled sites. It allows user to surf both http and https sites. So user can use the same to check his/her e-mails also.
Apart from that for two popular web resources such as Facebook and YouTube, it also provides special GUI to use. For Facebook: https://zend2.com/facebook-proxy/. For YouTube: https://zend2.com/youtube-proxy/. The YouTube proxy page contains instructions how to unblock YouTube if it's blocked in your school, college, office, or by the ISP while the Facebook proxy page contains general information how this web proxy works.
Though we can use all these three user interfaces to visit any site, as the bottom line of all, we want it to work as intermediary between user and the server. Apart from just surfing it also provides user some options to choose such as:
- Encrypt URL
- Encrypt Page
- Allow Cookies
- Remove Scripts
- Remove Objects
- User can check whatever he/she wants as per the requirement.
FilterBypass.me
Similar to zend2 it also allows users to surf anonymously with some more options such as Encrypt URL, Allow cookie etc. The only drawback of the proxy solution is that it fails to resolve some of the e-mail-providing sites but apart from that its user interface contains some popular site links that can be visited directly using this such as Facebook, YouTube, DailyMotion, Twitter etc.
Boomproxy.com
It is quite similar to anonymouse.org as it only supports http sites to browse but the only extra feature available here is that it contains options such as Encrypt URL,
Remove Objects etc.
Some more proxy solutions:
- http://www.internetcloak.com/
- http://www.crownproxy.com/
- http://www.hidesurf.us/
- http://www.webevade.com/
- http://www.proxyemails.com/
- http://www.proxytopsite.us/
- http://www.proxysites.net/
- http://www.everyproxy.com/
- http://www.ip-hide.com/
- http://www.greatproxies.com/
- http://proxy.org/
- http://www.proxyservers.info/
- http://thehiddenguide.com
HOW TO SET UP PROXY MANUALLY IN A BROWSER
There are many sites that provide proxy addresses in terms of IP and port but it's not that easy to get the genuine site. It's because the list might not be updated for some time and in the meanwhile the proxy server might not be working anymore. Though we can get still a good amount of sites, a good one is http://proxylist.hidemyass.com/.
The major benefit that user will get using this is it provides user a updated list with latest proxy IP addresses and port number along with that the expected speed, anonymity level, and country name where that IP belongs.
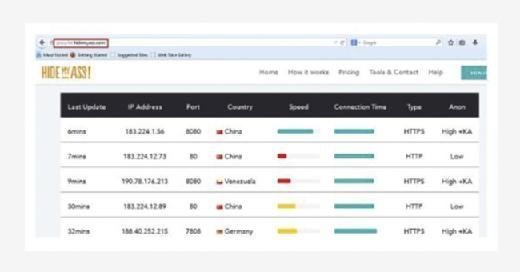
Apart from that it also allows user to filter the requirements based on country, protocol supported, connection speed, anonymity level, and many more. So this is one of the finest sources in terms of using the proxy IP and port.
Though most of the case the IP and port will work but before using it, it's better to test whether the IP is alive or not.
So simply choose an IP address and associated port based upon the requirement such as based on speed, protocol, anonymity level, and country. Try to choose the latest one which is updated in the list recently. Then open command prompt in case of Windows and terminal in case of Mac and Linux. In case of Windows, type "ipconfig" and the chosen IP address to check whether the IP is alive or not and in case of Mac and Linux the command is "ifconfig" with the chosen IP address.
Once we see the IP is alive, configure the same in browser. In case of Mozilla Firefox we did it earlier but let's revise the process.
Go to Tools → Options → Advanced → Network → Connection Settings → select Manual proxy configuration and use the chosen IP address and port number in respective fields.
In case of Chrome go to Settings → Show advanced settings → under Network tab click on Change proxy settings → click on LAN settings → check Use a proxy server for LAN then use the chosen IP address and port number in respective fields.
This is how proxy can be configured manually.
About the author: Sudhanshu Chauhan is an information security professional and OSINT specialist. He has worked in the information security industry, previously as Senior security analyst at iViZ and currently as Director and Principal Consultant at Octogence Tech Solutions, a penetration testing consultancy. He previously worked at the National Informatics Center in New Delhi developing web applications to prevent threats. He has a B.Tech (CSE) from Amity School of Engineering and Diploma in Cyber Security. He has been listed in various Halls of Fame such as Adobe, eBay, Yandex, and Freelancer. Sudhanshu has also written various articles on a wide range of topics including Cyber Threats, Vulnerability Assessment, Honeypots, and Metadata.
Nutan Panda is an Information Security professional with expertise in the field of Application and Network Security. He has completed his B.Tech (IT) and has also earned various prestigious Certifications in his domain such as CEH, CCNA etc. Apart from performing security assessments he has also been involved in conducting / imparting information security training. He has been listed in various prestigious Halls of Fame such as Google, Microsoft, Yandex etc. and has also written various articles / technical papers.







