honeypot (computing)
What is a honeypot?
A honeypot is a network-attached system set up as a decoy to lure cyber attackers and detect, deflect and study hacking attempts to gain unauthorized access to information systems. The function of a honeypot is to represent itself on the internet as a potential target for attackers -- usually, a server or other high-value asset -- and to gather information and notify defenders of any attempts to access the honeypot by unauthorized users.
Honeypot systems often use hardened operating systems (OSes) where extra security measures have been taken to minimize their exposure to threats. They are usually configured so they appear to offer attackers exploitable vulnerabilities. For example, a honeypot system might appear to respond to Server Message Block (SMB) protocol requests used by the WannaCry ransomware attack and represent itself as an enterprise database server storing consumer information.
Large enterprises and companies involved in cybersecurity research are common users of honeypots to identify and defend against attacks from advanced persistent threat (APT) actors. Honeypots are an important tool that large organizations use to mount an active defense against attackers or for cybersecurity researchers who want to learn more about the tools and techniques attackers use.
The cost of maintaining a honeypot can be high, in part because of the specialized skills required to implement and administer a system that appears to expose an organization's network resources, while still preventing attackers from gaining access to any production systems.
How do honeypots work?
Generally, a honeypot operation consists of a computer, applications and data that simulate the behavior of a real system that would be attractive to attackers, such as a financial system, internet of things (IoT) devices, or a public utility or transportation network. It appears as part of a network but is actually isolated and closely monitored. Because there is no reason for legitimate users to access a honeypot, any attempts to communicate with it are considered hostile.
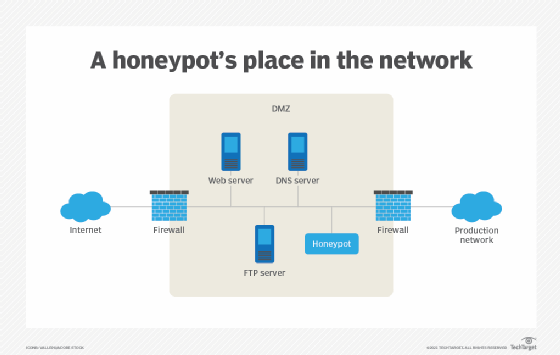
Honeypots are often placed in a demilitarized zone (DMZ) on the network. That approach keeps it isolated from the main production network, while still being a part of it. In the DMZ, a honeypot can be monitored from a distance while attackers access it, minimizing the risk of the main network being breached.
Honeypots may also be put outside the external firewall, facing the internet, to detect attempts to enter the internal network. The exact placement of the honeypot varies depending on how elaborate it is, the traffic it aims to attract and how close it is to sensitive resources inside the corporate network. No matter the placement, it will always have some degree of isolation from the production environment.
Viewing and logging activity in the honeypot provides insight into the level and types of threats a network infrastructure faces while distracting attackers from assets of real value. Cybercriminals can hijack honeypots and use them against the organization deploying them. Cybercriminals have also been known to use honeypots to gather intelligence about researchers or organizations, act as decoys and spread misinformation.
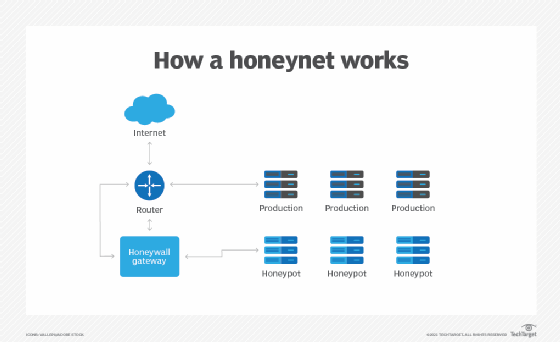
Virtual machines (VMs) are often used to host honeypots. That way, if they are compromised by malware, for example, the honeypot can be quickly restored. Two or more honeypots on a network form a honeynet, while a honey farm is a centralized collection of honeypots and analysis tools.
Both open source and commercial offerings are available to help with deploying and administering honeypots. Products include standalone honeypot systems, as well as honeypots packaged with other security software and marketed as deception technology. GitHub has an extensive list of honeypot software that can help beginners get an idea of how honeypots are used.
What are honeypots used for?
Honeypots are used to capture information from unauthorized intruders that are tricked into accessing them because they appear to be a legitimate part of the network. Security teams deploy these traps as part of their network defense strategy. Honeypots are also used to research the behavior of cyber attackers and the ways they interact with networks.
Spam traps are also similar to honeypots. They are email addresses or other network functions set up to attract spam web traffic. Spam traps are used in Project Honey Pot, which is a web-based network of honeypots embedded in website software. Its purpose is to harvest and collect the Internet Protocol (IP) addresses, email addresses and related information on spammers so web administrators can minimize the amount of spam on their sites. The group's findings are used for research as well and by law enforcement to combat unsolicited bulk mailing offenses.
Honeypots aren't always used as a security measure. Anyone can use them for network reconnaissance, including hackers. For instance, a Wi-Fi Pineapple lets users create a Wi-Fi honeypot. Wi-Fi Pineapples are relatively cheap because consumer devices are used to create a fake Wi-Fi network that mimics a real one in the vicinity. Unsuspecting individuals mistakenly connect to the fake Wi-Fi network, and the honeypot operator can then monitor their traffic. Wi-Fi Pineapples also have legitimate uses, such as for penetration testing (pen testing), where ethical -- or white hat -- hackers are hired to identify vulnerabilities in a network.
Types of honeypots
Based on design and deployment, there are two main types of honeypots: production and research.
- Research honeypots perform close analysis of hacker activity and aim to discover how hackers develop and progress in order to learn how to better protect systems against them. Data placed in a honeypot with unique identifying properties can also help analysts track stolen data and identify connections between different participants in an attack.
- Production honeypots are usually deployed inside production networks alongside production servers; the honeypot acts as a decoy, drawing intruders away from the production network as part of the intrusion detection system (IDS). A production honeypot is designed to appear as a real part of the production network and contains information to attract and occupy hackers to tie up their time and resources. This approach ultimately gives administrators time to assess the threat level and mitigate any vulnerabilities in their actual production systems.
Honeypots can be classified as pure, high-interaction or low-interaction:
- Pure honeypots are full-fledged production systems that monitor a honeypot's link to the network. They are the most complex and difficult to maintain, but they also appear most realistic to attackers, complete with mock confidential files and user information.
- High-interaction honeypots imitate the activities of the production systems, hosting a variety of services and capturing extensive information. The goal of a high-interaction honeypot is to entice an attacker to gain root -- or administrator-level -- access to the server and then monitor the attacker's activity.
- Low-interaction honeypots simulate the most common attack vectors on the network: the ones services attackers frequently request. Therefore, they are less risky and easier to maintain. They do not point malicious users to the root system. The downside of this type of honeypot is that it is more likely to look fake to an attacker. Low-interaction honeypots are good for detecting attacks from bots and malware. Honeyd is an open source virtual low-interaction honeypot.
Honeypots can be used to mimic several types of networks and technologies. A few examples are the following:
- enterprise databases;
- industrial and other control systems; and
- malware attack vectors and replication vectors, such as Universal Serial Bus (USB) drives.
There are several types of specialized honeypot technologies, such as the following:
- Malware honeypots. These are honeypots that mimic malware attack vectors -- places that malware attacks and replicates.
- Spam honeypots. These can detect the methods of spammers, monitor their activity and block spam.
- Database honeypots. These create decoy databases to mislead attackers using methods that are sometimes missed by firewalls, like Structured Query Language (SQL) injections.
- Client honeypots. These actively seek out malicious servers behind client attacks instead of passively waiting for connections. They use virtualization to establish themselves on the server and watch for suspicious modifications to the honeypot.
More on deception technology
Honeypots and other deception technology are used in a variety of ways. Find out about the full array of incident response tools that are available, how a honeypot can be deployed in the cloud and how one pharmaceutical company is using deception tools.
Top incident response tools to boost network protection
Learn where your environment is at risk with an AWS honeypot
Benefits and risks of honeypots
Honeypots provide significant benefits, but they also come with disadvantages and risks.
Benefits
- Real data collection. Honeypots collect data from actual attacks and other unauthorized activities, providing analysts with a rich source of useful information.
- Fewer false positives. Ordinary cybersecurity detection technologies generate alerts that can include a significant volume of false positives, but a honeypot reduces the number of false positives because there is no reason for legitimate users to access the honeypot.
- Cost-effectiveness. Honeypots can be good investments because they only interact with malicious activities and do not require high-performance resources to process large volumes of network traffic looking for attacks.
- Encryption circumvention. Honeypots capture malicious activity, even if an attacker is using encryption.
Disadvantages
- Limited data. Honeypots only collect information when an attack occurs. Zero attempts to access the honeypot means there is no data to analyze.
- Isolated network. Malicious traffic that has been captured is only collected when an attack targets the honeypot network; if attackers suspect a network is a honeypot, they will avoid it.
- Distinguishable. Honeypots are often distinguishable from legitimate production systems, which means experienced hackers can often differentiate a production system from a honeypot system using system fingerprinting techniques.
- Put production systems at risk. Although they are isolated from the real network, they do eventually connect in some way to enable administrators to collect the information they contain. A high-interaction honeypot is generally considered riskier than a low-interaction one because it aims to entice hackers to gain root access.
Overall, honeypots help researchers understand threats in network systems, but production honeypots should not be a replacement for a standard IDS. If a honeypot is not configured correctly, it can be used to gain access to real production systems or as a launchpad for attacks against other target systems.
Honeynet
A honeynet consists of two or more honeypots on a network. Having an interconnected network of honeypots can be useful. It enables organizations to track how an attacker interacts with one resource or network point, and it also monitors how an intruder moves among points on the network and interacts with multiple points at one time. The goal is to get hackers to believe that they have successfully breached the network, so having more fake network destinations makes the setup more convincing.
The term deception technology has been used to describe the more complex implementations of honeypots and honeynets, often packaged with other technology, such as next-generation firewalls (NGFWs), IDSes and secure web gateways. Deception technology includes automated features that let a honeypot respond in real time to potential attackers.
Cyber threats continue to evolve, and honeypots can help organizations keep up with the ever-changing threat landscape. Even though it's impossible to predict and prevent every attack, honeypots provide useful information to ensure an organization is prepared and are perhaps the best way to catch an attacker in the act. They are a good place for cybersecurity professionals to gather information as well.
Learn more about responding to cyber threats in our ultimate guide to cybersecurity incident response.






