SecureAuth IdP: An overview of its multifactor authentication ability
Expert David Strom looks at how SecureAuth IdP uniquely combines multifactor authentication and single sign-on login capabilities in a single product.
Unlike most of the other multifactor authentication products that have been profiled in this series, SecureAuth IdP can be used for both multifactor authentication and single sign-on purposes. SecureAuth came to multifactor authentication from the single sign-on space, where the company got its start.
As a multifactor authentication (MFA) tool, SecureAuth IdP (currently on version 9.0), like other similar MFA products in this series, adds additional security measures to standard username/password logins to a variety of servers and services. This prevents unauthorized logins, even when passwords have been compromised and shared among many different services.
As a single sign-on (SSO) tool, SecureAuth IdP connects to a directory service, such as Active Directory (AD), during the sign-in process. Users sign in to a web-based portal and use that as the basis for the authentication of the SSO app portfolio, where the multifactor elements are applied. This means users don't have to remember -- or, in some cases, even need to know -- what their Google or Box passwords are to gain access to these apps.
The cloud-based authentication service is an appropriate technology for midsize to large enterprises. It is especially suitable for those that make use of a variety of external software as a service (SaaS)-based services and want to greatly improve security.
SecureAuth IdP management and administration
As with Okta Verify, SecureAuth IdP comes from the SSO world and, as such, reflects a very strong federation and Security Assertion Markup Language (SAML) story. This means the MFA product is easily integrated into a wide variety of applications, and under an assortment of circumstances, especially as SAML gains credence and popularity among SaaS applications.
Besides SAML, SecureAuth IdP can leverage a number of other MFA integration methods. These include, for example, specific agents that customers can add to Microsoft Internet Information Services, Apache Tomcat and JBoss web servers to enable those technologies to accept the authentication federation. It also supports virtually all VPNs currently on the market, any application that supports federation and any application where the customer controls the login page itself. All of this makes SecureAuth IdP a very flexible, strong authentication tool.
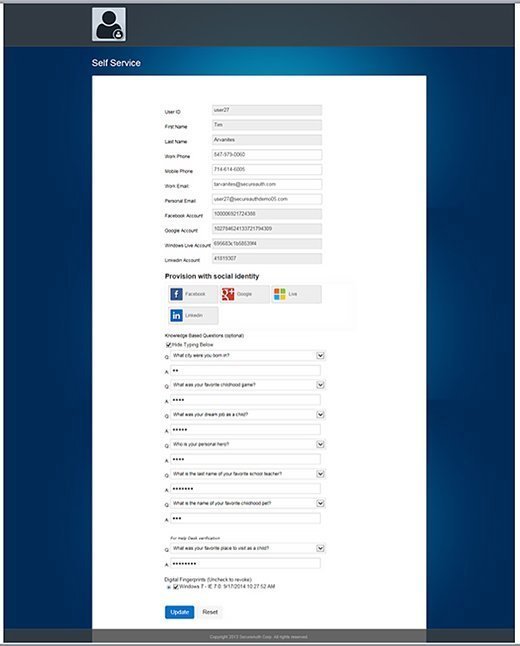
End users get a self-service, web-based portal where they can update their second-factor connections or even reset their AD password without any IT involvement. This reduces the amount of administration time required to maintain user logins, which is a plus for many IT employees. Administrators, meanwhile, can set up a separate help desk web app where they or the end user can easily revoke any certificates or disable any authentication tokens that have gone awry.
Also, unlike some of the other MFA products we've looked at, there is no additional software to download or agents to install. This greatly simplifies the configuration process as compared to products such as Symantec's Validation and ID Protection Service or EMC RSA's Authentication Manager and SecurID platform, for example.
One of the more interesting aspects of SecureAuth IdP is that, unlike most other multifactor authentication solutions, it supports multiple authentications that can be issued in a sequence, depending on the level of security required. That way, IT managers can move a password (usually the first factor) to the last entry in a workflow. This means very flexible workflows can be created with step-up authentication inserted at any point in the login process. For example, IT can have a user enter his or her social network ID upfront, and then strengthen the login afterwards with additional authentication hurdles. Version 9.0 now includes behavior biometrics in its platform.
One drawback to SecureAuth IdP is that the reports are not as simple to set up as with some of its competitors, and it will require some customization on its web portal. Once reports are created, they are easily exported into a CSV format, however.
Conclusion
SecureAuth IdP is both a solid SSO and multifactor authentication tool that combines the best of both worlds. If an enterprise is using numerous SaaS-based apps and wants to solve the issue of needing stronger passwords that are unique across a wide variety of services, this product should receive serious consideration.






