Check Point UTM Threat Prevention Appliances: Product review
Check Point UTM Threat Prevention Appliances are recognized by our reviewer as consistent software architectures that are easy to configure.
Editor's note: This article has been updated for accuracy regarding platform support and pricing.
The Check Point Software Next Generation Threat Prevention Appliances are the latest in a long line of security products from the vendor, whose brand is synonymous with firewalls. Check Point has one of the best united threat management, or UTM, approaches, providing solid products -- both for the high and low ends of the market -- with the essential features enterprises look for.
Product specs
Check Point Software Technologies Ltd. sells 17 different models of its rather oddly named Next Generation Threat Prevention Appliances. They have a range of 10 1 gigabit Ethernet (GbE) ports on the smallest unit to 37 1 GbE and 13 10 GbE ports on the largest unit.
The rated firewall throughput of the devices ranges from 750 Mbps to 110 Gbps, which covers a lot of ground. Check Point also sells acceleration modules to push the higher-end rates to faster-rated throughputs.
Additionally, Check Point has a smaller model, called the UTM-1 Edge N Industrial Appliance, which runs the same software, but is designed for industrial Ethernet and SCADA environments. This is the latest version of a long line of Check Point UTM appliances that use the company's "software blade" architecture, which is a fancy way of saying it packages and bundles various features for network protection or Web-filtering appliances.
Understand Check Point software blades
Check Point UTM appliances are offered with two different software packages -- Next Generation Threat Prevention and Next Generation Threat Extraction (NGTX).
Both packages include a firewall, VPN, intrusion prevention system (IPS), application control, antivirus, antibot, URL filtering, antispam and email security, advanced networking and clustering, identity awareness, mobile access, network policy management, and logging and status features. NGTX also includes threat emulation, or sandboxing, and threat extraction. Using threat extraction, exploitable content such as some embedded objects and active content is removed from infected documents, leaving a safe -- yet somewhat altered -- document.
Special features
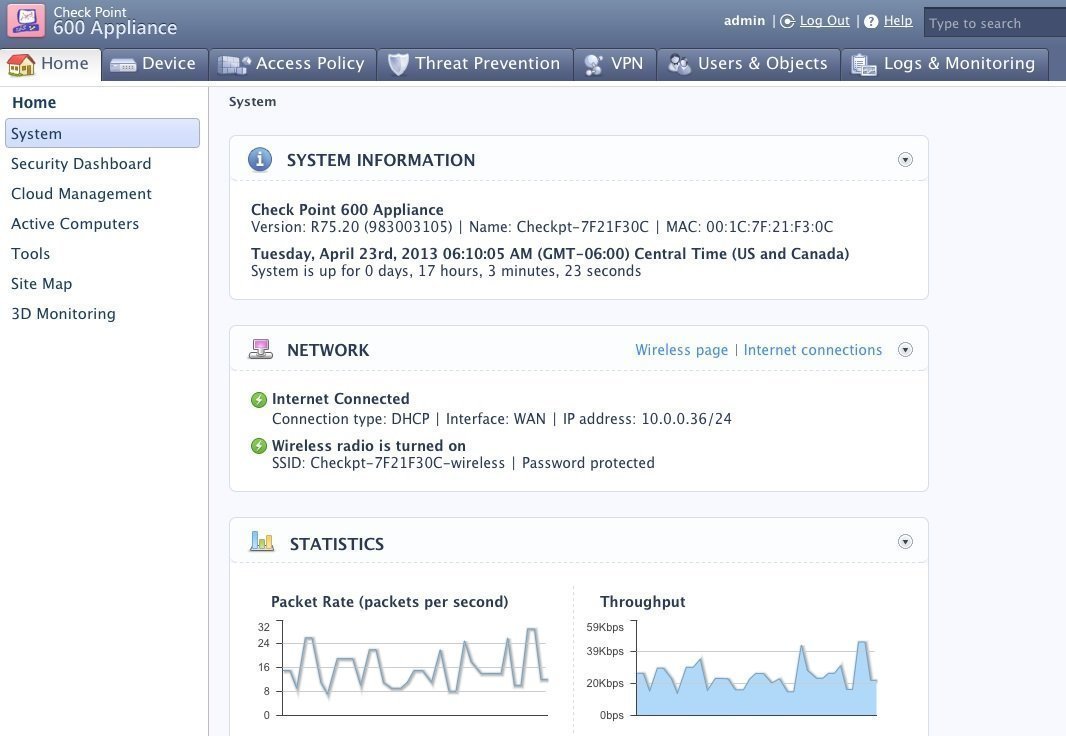
One of the things I like about Check Point UTM products is that the software architecture is the same whether an organization buys a high-end box or a small office box. That consistency not only eases management, but also allows an organization to put more faith in the product as a whole. It also offers a leading-edge user interface that is clean, easy to understand, and has the best-looking and clearest menus of any of the boxes I have used. Its policy-creation tools are also straightforward, and it's easy to understand the inherent workflow -- unlike the tools on Juniper's SRX or Dell's SonicWall. It also works well with mixed Mac and Windows networks.
By default, Check Point's appliance enables all of its ports on a single LAN switch, and you can define any port to be part of any network via its configuration software; so, it is quite flexible. For the smaller boxes that have an integrated wireless access port, organizations can set up multiple SSIDs for the wireless interface with just a single policy selection. This is the easiest wireless configuration of any of the boxes I have tested. Check Point seems to have tried to cover all of the bases in terms of features and functionality for a wide range of network sizes and use cases.
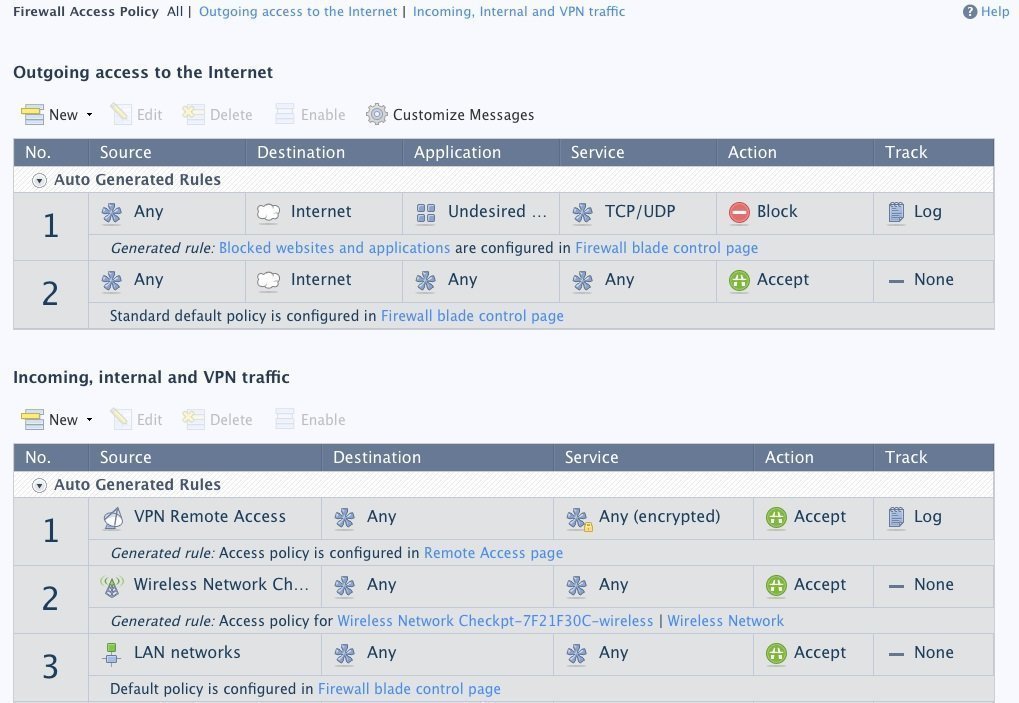
Unlike Juniper, Check Point doesn't hide its advanced settings in a command-line interface. Instead, everything is accessible from its Web interface. If an enterprise needs extra features, such as setting up a failover link or changing the priority of a particular security policy, it isn't too hard to find the right menu option to accomplish the task.
Check Point also includes a connection to its Threat Cloud online reputation service-monitoring tool, allowing organizations to screen traffic for near real-time malware detection.
Performance
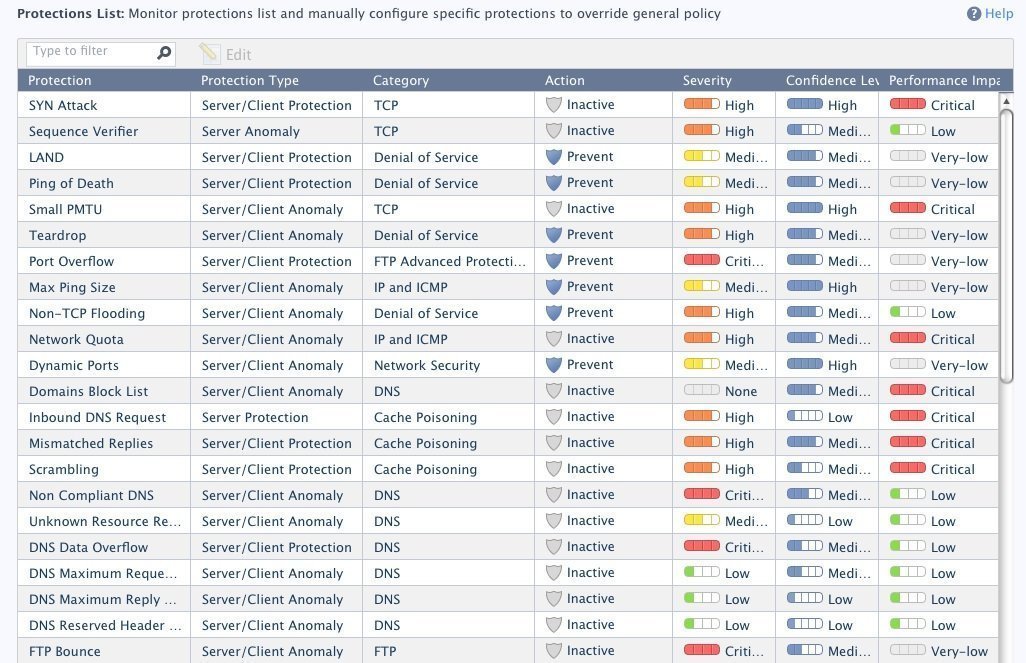
Based on my previous testing of various Check Point UTM appliances, they deliver both the protection features, as well as the ease of configuration and use that enterprises would expect from a leading-edge UTM vendor.
But also note
The biggest issue for Check Point is its sheer number of different products. If you don't need every UTM security feature under the sun, you might be better off purchasing a more focused product that has fewer key features, such as a combination firewall and IPS. Equally complex is its support pricing. While its menus are clearly presented, there are some context changes on the left-hand menu when choosing top menu tabs that can be somewhat annoying at first.
Pricing
The price of the CheckPoint UTM-1 unit ranges from $1,175 to $3,150, depending on the number of users, and is sold as a bundle -- appliance and software, plus a one-year support contract. Pricing on all other units starts at $11,300 for the appliance and basic software modules, and can top $200,000 for the larger units. There are five different support packages, which include next business day or four-hour on-site response, along with next-day air shipments of replacement parts and other options. If an organization has a customer account with Check Point already, it can configure its appliance with the right collection of software and support services. Adding high-availability service will up the price tag significantly, too.
|








