Certified Information Systems Security Professional (CISSP)
What is Certified Information Systems Security Professional (CISSP)?
Certified Information Systems Security Professional (CISSP) is an information security certification developed by the International Information Systems Security Certification Consortium, also known as (ISC)². The CISSP designation is a globally recognized, vendor-neutral standard attesting to an IT security professional's technical skills and hands-on experience implementing and managing a security program.
CISSP certification is highly sought after by IT professionals. Hiring organizations often look for candidates who have passed the CISSP exam because candidates with the CISSP credential must be sufficiently knowledgeable about cybersecurity to be able to pass the certification exam, and have hands-on experience and, potentially, formal CISSP training.
How to become CISSP-certified
Becoming CISSP-certified requires more than passing the Certified Information Systems Security Professional certification exam. Candidates are required to have a minimum of five years of full-time, hands-on experience in at least two of the eight CISSP domains.
(ISC)² advises the following four-step pathway to certification:
- Ensure CISSP is right for you.
- Register and prepare for the exam.
- Get certified.
- Become an (ISC)2
(ISC)² recommends CISSP certification for experienced cybersecurity practitioners. Candidate roles include chief information security officer (CISO), chief information officer (CIO), director of security, IT manager, security systems engineer, security analyst, security manager, security auditor, security architect, security consultant and network architect.
Preparation can be achieved through self-study and using CISSP practice books and study guides, as well as online practice exams. Many candidates also enroll in CISSP training courses to prepare for the exam.
CISSP requirements
To earn the CISSP credential, the candidate must pass the certification exam, as well as complete the CISSP exam agreement, subscribe to the (ISC)² code of ethics, answer background qualification questions and receive an endorsement from an active (ISC)²-certified professional.
To maintain the CISSP certification, candidates are required to earn at least 120 Continuing Professional Education (CPE) credits every three years and pay an annual maintenance fee of $125.
CISSP exam
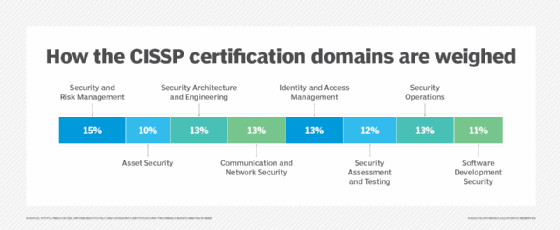
The CISSP exam is six hours long and consists of 250 multiple-choice questions and advanced innovative questions testing the candidate's knowledge and understanding of the eight domains of the (ISC)² Common Body of Knowledge (CBK). The CBK domains are the following:
- Security and Risk Management (15% of exam)
- Asset Security (10%)
- Security Architecture and Engineering (13%)
- Communication and Network Security (13%)
- Identity and Access Management (13%)
- Security Assessment and Testing (12%)
- Security Operations (13%)
- Software Development Security (11%)
The results are calculated on a scaled score, with a score of 700 or higher out of a 1,000 point maximum required to pass.
The CISSP exam is offered in English, German, Spanish, Japanese, simplified Chinese, Korean and a format for the visually impaired. The certification exam is administered by Pearson VUE and conducted at Pearson VUE test centers.
Cost of the CISSP exam
As of this writing, the exam costs $749, though exact pricing and taxes vary based on the location of the exam. Attendance at the certification exam can be rescheduled for a $50 fee; there is a $100 fee to cancel the exam. CISSP training is an additional cost.
The CISSP credential is valid for three years after the successful completion of the requirements. After three years, CISSP credential holders can recertify as long as they have paid the annual maintenance fee and submitted their 120 hours of CPE credits every three years. Maintaining 40 CPE credits per year is recommended.
CISSP training
Several CISSP trainings are available, including official self-paced and instructor-led training from (ISC)2, which is available online or in person.
Because the CISSP certification exam is targeted to working cybersecurity professionals who have extensive hands-on experience in the field, candidates should not rely on formal CISSP training to gain the skills and knowledge they need to pass the certification exam.
CISSP training should focus on reviewing the CBK -- the comprehensive framework for organizing the areas of expertise expected from cybersecurity professionals. It should also validate that the candidate is familiar with the test material and identify blind spots in the candidate's experience and knowledge.
CISSP concentrations
Professionals who currently hold the CISSP credential can also qualify by adding one of three CISSP concentrations:
- Architecture (CISSP-ISSAP)
- Engineering (CISSP-ISSEP)
- Management (CISSP-ISSMP)
In addition to already having the CISSP certification, the candidate must have at least two years of work experience in one or more of the concentration's domains.
ISSAP domains are the following:
- Domain 1. Architect for Governance, Compliance and Risk Management
- Domain 2. Security Architecture Modeling
- Domain 3. Infrastructure Security Architecture
- Domain 4. Identity and Access Management (IAM) Architecture
- Domain 5. Architect for Application Security
- Domain 6. Security Operations Architecture
ISSEP domains are the following:
- Domain 1. Systems Security Engineering Foundations
- Domain 2. Risk Management
- Domain 3. Security Planning and Design
- Domain 4. Systems Implementation, Verification and Validation
- Domain 5. Secure Operations, Change Management and Disposal
ISSMP domains are the following:
- Domain 1. Leadership and Business Management
- Domain 2. Systems Lifecycle Management
- Domain 3. Risk Management
- Domain 4. Threat Intelligence and Incident Management
- Domain 5. Contingency Management
- Domain 6. Law, Ethics, and Security Compliance Management
CISSP concentration exams are three hours long, are offered in English only and consist of 125 multiple-choice questions. The exam fees are all $599.
After passing their chosen exam by earning at least 700 points out of 1,000, candidates must go through a similar endorsement process as with CISSP. Candidates must also earn 20 CPE credits each year, which may also be applied to CISSP CPE requirements.
Editor's note: This article was updated to include updated pricing and exam information.






