Network-based attacks
The second tip in our series, "How to assess and mitigate information security threats," excerpted from Chapter 3: The Life Cycle of Internet Access Protection Systems of the book The Shortcut Guide to Protecting Business Internet Usage published by Realtimepublishers.
This is tip No. 2 in our series, "How to assess and mitigate information security threats," excerpted from Chapter 3: The Life Cycle of Internet Access Protection Systems of the book The Shortcut Guide to Protecting Business Internet Usage published by Realtimepublishers.
Network-based attacks are threats that are launched and controlled from a device or devices other than those under attack. Denial-of-service (DoS) attacks and distributed-denial-of-service (DDoS) attacks are examples of network-based attacks. These attacks use one or more devices to overwhelm the targeted server with so much network traffic or demands for services that the target cannot respond to legitimate requests. Firewalls and intrusion prevention systems (IPSes) are countermeasures to these types of attacks. They use a few different techniques to detect and inhibit attacks. Some work by detecting patterns in network traffic indicative of an attack. These are analogous to using virus signatures in antivirus software; a large number of TCP connection requests, for example, can indicate an attack known as SYN Flooding, a crude but sometimes effective DoS attack.
IPSes can also use statistical techniques to analyze typical patterns of system use on a server or a network. These patterns are then used as a baseline for comparing with ongoing system use; any significant deviation for the baseline could indicate an attack. Complementing statistical technique are rule-based approaches that use heuristics, or rules of thumb, for detecting anomalies in system activity.
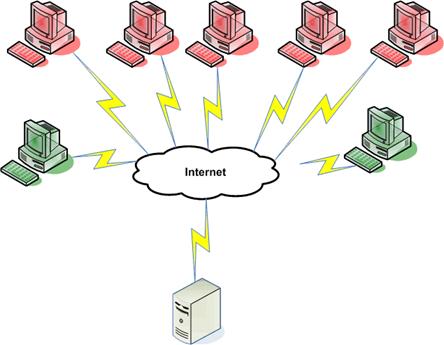
Figure 3.2: In a DDoS attack, multiple devices (red) flood a server with requests, overwhelming the server and blocking legitimate users (green).
How to Assess and Mitigate Information Security Threats
- Introduction
- Malware: The ever-evolving threat
- Network-based attacks
- Information theft and cryptographic attacks
- Attacks targeted to specific applications
- Social engineering
- Threats to physical security
- Balancing the cost and benefits of countermeasures
This chapter excerpt from the free eBook The Shortcut Guide to Protecting Business Internet Usage, by Dan Sullivan, is printed with permission from Realtimepublishers, Copyright 2006.







