fiber optics (optical fiber)
What is fiber optics?
Fiber optics, or optical fiber, refers to the technology that transmits information as light pulses along a glass or plastic fiber.
A fiber optic cable can contain a varying number of glass fibers, from a few up to a couple hundred. Another glass layer called cladding surrounds the glass fiber core. The buffer tube layer protects the cladding, and a jacket layer acts as the final protective layer for the individual strand.
Fiber optic cables are commonly used because of their advantages over copper cables. Some of those benefits include higher bandwidth and transmit speeds.
Fiber optics is used for long-distance and high-performance data networking. It is also commonly used in telecommunication services, such as internet, television and telephones. For example, Verizon and Google use fiber optics in their Verizon Fios and Google Fiber services, respectively, providing Gigabit internet speeds to users.
How fiber optics works
Fiber optics transmits data in the form of light particles, or photons, that pulse through a fiber optic cable. The glass fiber core and the cladding each have a different refractive index that bends incoming light at a certain angle.
When light signals are sent through the fiber optic cable, they reflect off the core and cladding in a series of zig-zag bounces, following a process called total internal reflection. The light signals do not travel at the speed of light because of the denser glass layers, instead traveling about 30% slower than the speed of light.
To renew, or boost, the signal throughout its journey, fiber optics transmission sometimes requires repeaters at distant intervals. These repeaters regenerate the optical signal by converting it to an electrical signal, processing that electrical signal and retransmitting the optical signal.
Fiber optic cables are now able to support up to 10 Gbps signals. Typically, as the bandwidth capacity of a fiber optic cable increases, the more expensive it becomes.
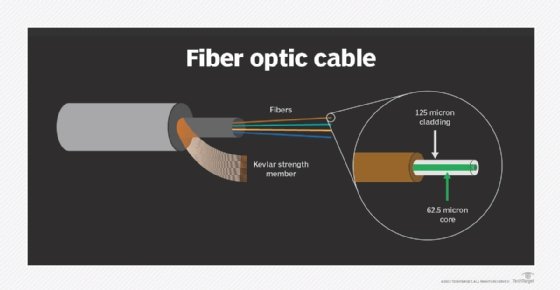
Types of fiber optic cables
Multimode fiber and single-mode fiber are the two primary types of fiber optic cable.
Single-mode fiber
Single-mode fiber is used for longer distances due to the smaller diameter of the glass fiber core. This smaller diameter lessens the possibility for attenuation, which is a reduction in signal strength. The smaller opening isolates the light into a single beam, offering a more direct route and enabling the signal to travel a longer distance.
Single-mode fiber also has a considerably higher bandwidth than multimode fiber. The light source used for single-mode fiber is typically a laser. Single-mode fiber is usually more expensive as it requires precise calculations to produce the laser light in a smaller opening.
Multimode fiber
Multimode fiber is used for shorter distances because the larger core opening lets light signals bounce and reflect more along the way. The larger diameter permits multiple light pulses to be sent through the cable at one time, which results in more data transmission. This also means more possibility for signal loss, reduction or interference. Multimode fiber optics typically uses an LED to create the light pulse.
Fiber optics vs. copper cables
Copper wire cables were the traditional choice for telecommunication, networking and cable connections for years. Over time, however, fiber optics became a common alternative. Most telephone company long-distance lines are now made of fiber optic cables.
Optical fiber carries more information than conventional copper wire due to its higher bandwidth and faster speeds. Because glass does not conduct electricity, fiber optics is not subject to electromagnetic interference, which minimizes signal losses.
Advantages and disadvantages of fiber optics
Fiber optic cables are used mainly for their advantages over copper cables. Advantages include the following:
- They support higher bandwidth capacities.
- Light can travel further without needing as much of a signal boost.
- They are less susceptible to interference, such as electromagnetic interference.
- They can be submerged in water.
- Fiber optic cables are stronger, thinner and lighter than copper wire cables.
- They do not need to be maintained or replaced as frequently.
However, it is important to note that fiber optics do have disadvantages. These disadvantages include the following:
- Fiber optics is often more expensive than copper wire.
- Glass fiber requires more protection within an outer cable than copper.
- Installing new cabling is labor intensive.
- Fiber optic cables are often more fragile. For example, the fibers can be broken, or a signal can be lost if the cable is bent or curved around a radius of a few centimeters.
Fiber optics uses
A range of industries use fiber optic cables for reliable and fast connectivity.
Computer networking and broadcasting
Computer networking is a common fiber optics use case due to optical fiber's ability to transmit data and provide high bandwidth. Similarly, fiber optics is frequently used in broadcasting and electronics to provide better connections and performance.
Internet and cable television
Internet and cable television are two of the more common use cases for fiber optics. Fiber optics can be installed to support long-distance connections between computer networks in different locations.
Undersea environments
Fiber optic cables are used in more at-risk environments, like undersea cables, as they can be submerged in water and don't need to be frequently replaced.
Military and space
Military and space industries also make use of optical fiber as a means of communication and signal transfer in addition to its ability to provide temperature sensing. Fiber optic cables can be beneficial due to their lighter weight and smaller size.
Medical
Fiber optics is frequently used in a variety of medical instruments to provide precise illumination. It also increasingly enables biomedical sensors that aid in minimally invasive medical procedures. Because optical fiber is not subject to electromagnetic interference, it is ideal for various tests like MRI scans. Other medical applications for fiber optics include X-ray imaging, endoscopy, light therapy and surgical microscopy.
Editor's note: This definition was updated to improve the reader experience.







