nonrepudiation
What is nonrepudiation?
Nonrepudiation ensures that no party can deny that it sent or received a message via encryption and/or digital signatures or approved some information. It also cannot deny the authenticity of its signature on a document.
Although it originated as a legal concept, nonrepudiation is also widely used in computing, information security and communications.
Information assurance and nonrepudiation
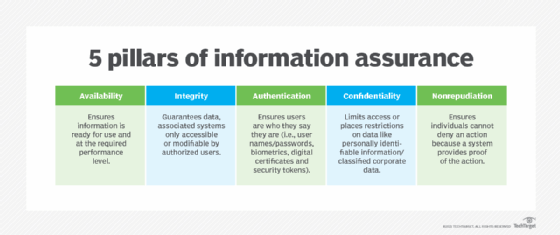
Nonrepudiation is one of the five pillars of information assurance (IA), which is the practice of managing information-related risks and protecting information systems, like computers, servers and enterprise networks. The other four pillars are the following:
- integrity
- availability
- authentication
- confidentiality
Nonrepudiation provides proof of the origin, authenticity and integrity of data. It provides assurance to the sender that its message was delivered, as well as proof of the sender's identity to the recipient. This way, neither party can deny that a message was sent, received and processed.
Nonrepudiation is like authentication, particularly with respect to implementation. For instance, a public key signature can be a nonrepudiation device if only one party can produce signatures.
In general, nonrepudiation combines both authentication and integrity.
Nonrepudiation, message authentication code and digital signatures
Nonrepudiation is achieved through cryptography, like digital signatures, and includes other services for authentication, auditing and logging.
In online transactions, digital signatures ensure that a party cannot later deny sending information or deny the authenticity of its signature. A digital signature is created using the private key of an asymmetric key pair, which is public key cryptography, and verified with a corresponding public key.
Only the private key holder can access this key and create this signature, proving that a document was electronically signed by that holder. This ensures that a person cannot later deny that they furnished the signature, providing nonrepudiation.
In cryptography, a message authentication code (MAC), also known as a tag, is used to authenticate a message or confirm that the message came from the stated sender and was not changed along the way. Unlike digital signatures, MAC values are generated and verified using the same secret key, which the sender and recipient must agree on before initiating communications.
A MAC can protect against message forgery by anyone who doesn't know the shared secret key, providing both integrity and authentication. However, MAC algorithms, like cipher-based MAC and hash-based MAC, cannot provide nonrepudiation.
In addition to digital signatures, nonrepudiation is also used in digital contracts and email. Email nonrepudiation involves methods such as email tracking.
Drawbacks of nonrepudiation with digital signatures
Since no security technology is foolproof, some experts warn that a digital signature alone may not always guarantee nonrepudiation. Some suggest using multiple approaches to ensure nonrepudiation. One such practice is to capture biometric information and other data about the sender or signer that collectively would be difficult to repudiate.
It's also important to know that the current definitions of nonrepudiation in the digital space consider only the validity of the signature itself. They do not allow for the possibility that the signer was manipulated, forced or tricked into signing. It's also feasible that a virus, worm or other type of malware can compromise a sender's private key, possibly stealing or forging its digital signature and jeopardizing nonrepudiation.

To avoid such issues and to ensure that a digital signature is valid -- and, therefore, the appropriate choice for nonrepudiation -- it must be established through a secure and fully trusted document handling and signature mechanism.
Another concern is the possibility that a digital signature remains the same, even if it's been faked by someone who has the private key. The U.S. Department of Defense addressed this problem with the common access card (CAC), a type of smart card for active duty defense personnel.
The CAC proves the holder's identity and enables physical access to controlled spaces and defense computer systems. It satisfies the requirements for digital signatures, as well as three IA pillars: nonrepudiation, integrity and authentication.







