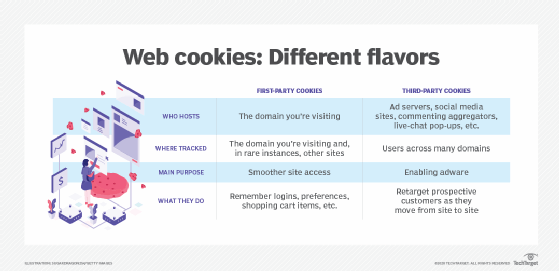
cookie poisoning
What is cookie poisoning?
Cookie poisoning is a type of cyber attack in which a bad actor hijacks, forges, alters or manipulates a cookie to gain unauthorized access to a user's account, open a new account in the user's name or steal the user's information for purposes such as identity theft. Cookie poisoning is also known as session hijacking.
To grasp the concept of cookie poisoning, it is essential to understand the fundamentals of cookies and how they work.
A cookie is a piece of information that gets added to a user's hard disk when they visit a website. It records their preferences as they use the website and is retrieved later by websites and web servers to do the following:
- authenticate the user's identity;
- speed up transactions -- for example, on banking or e-commerce websites;
- monitor user behavior;
- auto fill personal information on web forms;
- track items in shopping carts; and
- streamline user experiences.
There are two common types of cookies:
- Session, or nonpersistent, cookies last only as long as the user's website session and expire when the user leaves the website.
- Persistent cookies last beyond the life of a single session. They are created to recognize users when they return to a website and to deliver a personalized user experience with every visit.
How do cookies work?
As mentioned earlier, the data stored in the cookie lets the web server know the history of the website's interaction with a particular user. This enables the website to display the correct information for that user.
Let's visualize a scenario to understand the role of cookies:
- A user enters login credentials on a website.
- The site's server verifies the credentials and authenticates the login.
- Subsequently, the server logs the session in a database, and a cookie containing the session ID is returned to the browser.
- The process of verifying the session ID in the cookie data with the database continues on every subsequent request until the user logs out.
- Once the user logs out, the session is automatically destroyed on the client and server
- However, the cookie data continues to remain on the user's hard disk -- meaning the cookie persists -- if they have checked the Remember me or Keep me logged in options.
How cookie poisoning works
Cookie poisoning happens when unauthorized persons (attackers) can manipulate cookies due to the poor security infrastructure of a website. By editing or manipulating the cookie, the attacker can gain access to the user data stored in the cookie.
Cookie poisoning attacks are dangerous because they enable attackers to use the data stored inside cookies to gain unauthorized access to users' accounts or to steal their identities.
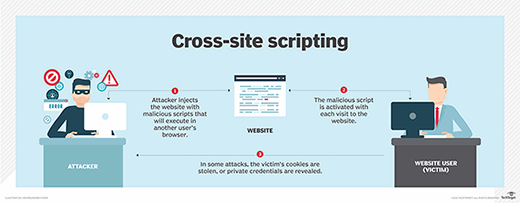
Cookie poisoning through cross-site scripting (XSS)
Cross-site scripting, commonly known as XSS, is one of the most popular ways to access and manipulate cookie data. Usually, attackers find a page that is vulnerable to XSS injection. By inserting a malicious script into the page, they can get the page to send them the session cookies of everyone who views the page. This way, they can gain access to the data of all these users.
Since the stolen cookie enables the attacker to mimic its real owner, attackers can stay logged in to their victims' accounts without the victims realizing it. Moreover, attackers don't need to enter a password to access victim accounts. This is why XSS is so widely used in cookie poisoning attacks and why it is such an effective attack vector.
Session hijacking, session spoofing and session fixation
Cookie poisoning attacks usually target user session cookies. Cookie-based attacks against sessions aim to fool the web server into thinking that the attacker is the legitimate user.
Examples of such attacks include the following:
- Session hijacking. When a legitimate user is logged in to a website, attackers use their knowledge of the current session cookie to take over the user's session.
- Session spoofing. Attackers use stolen or forged session tokens to start a new session and impersonate the legitimate user. This type of attack requires no user interaction and can be initiated even when the user is not logged in to the website.
- Session fixation. Attackers send a known session identifier via a phishing email or other means and fool a legitimate user into using this identifier to log in to a vulnerable or malicious site. The attacker then hijacks the user session.
Types of cookie poisoning attacks
Apart from XSS, cookie poisoning attacks can also be perpetrated through other methods, such as the following:
- Client-side cookie poisoning. This type of attack is initiated by someone who can manipulate the cookie data before the cookie reaches the server.
- Man-in-the-middle cookie hijacking. Here, the attacker acts as a middleman between the client-end web browser and the web server, gains access to the cookie information being transmitted, and then steals or modifies it for malicious benefit.
- Buffer overflow attack. If a web server is running insecure software, the user is vulnerable to buffer overflow attacks. In such attacks, the attacker can read the memory of the server, which often contains cookie information. Buffer overflows are now fairly rare, as most modern-day programming languages, like PHP, Java and JavaScript, used to create web applications are immune to buffer overflow errors.
How to prevent cookie poisoning
Unless security measures are in place, an attacker can examine a cookie to determine its purpose and edit it to get user information from the website that sent the cookie. To avoid cookie poisoning, maintaining proper cookie hygiene is vital.
Here's how users can prevent -- or at least minimize -- cookie poisoning attacks:
- Using unique and secure session cookies. It's important to ensure that session identifiers are inaccessible to attackers once the session is closed. They should also be randomly generated and hard to crack by using brute force or other means.
- Limiting multipurpose cookies. Multipurpose cookies create a lot of security risks, so it is important to restrict each cookie for a single task.
- Using Hypertext Transfer Protocol Secure (HTTPS) communication. It is vital to use HTTPS communication to establish secure information flow and reduce the chances of attackers eavesdropping on cookie content.
- Having comprehensive session management. Ensuring strict and synchronous session management can increase cookie security and prevent poisoning attacks.
- Performing vulnerability scans. By regularly scanning web applications using a vulnerability scanner, security vulnerabilities that may lead to cookie poisoning can be proactively identified and eliminated.
Websites that use cookies should also protect them via encryption before they are sent to a user's computer. A digital signature should be created to validate the content in all future communications between the user and the web server. If the content is tampered with, the signature will no longer match the content, and access by the server will be denied.
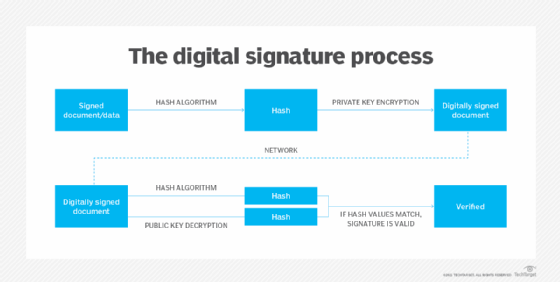
See how to use a public key and private key in digital signatures and what the loss of third-party cookies means for IT departments.







