Sergey Nivens - Fotolia
What CIOs need to know about hardening IT infrastructure
Infrastructure hardening is an ongoing, proactive way of life for CIOs and their IT teams. Here, we provide guidance to ensure that hardening is planned and implemented successfully.
As organizations continue to deal with the effects of the COVID-19 pandemic, CIOs must invest in activities to harden all, or most, elements of their IT infrastructures -- if they have not done so already.
Hardening IT infrastructure is simply increasing the security posture of virtually all components within the infrastructure, including devices, software, network services and facilities.
Among the infrastructure elements that must be hardened are servers of all kinds, applications, databases and OSes. They can also include network services; devices that connect to networks; equipment that secures network perimeters; facilities, including data centers and equipment rooms that contain servers and network devices; and utilities, such as power, water and sewer.
The following diagram is a basic depiction of how a hardened IT data center looks in the enterprise.
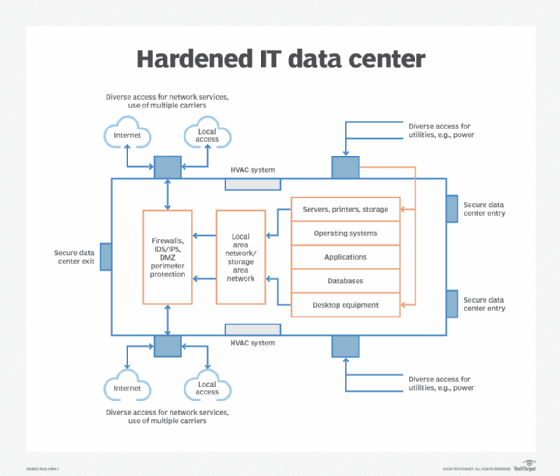
Virtually all elements in the data center have some degree of hardening. As we'll examine here, true IT hardening is more than enhancing security for servers and critical software. It's not only about hardening logical security, but also addressing the physical security as unauthorized access into a data center could result in damage that goes far beyond software damage.
The good news is that infrastructure hardening technologies are readily available and can be added to existing environments, often with minimal disruption to production activities. However, to be extra prudent, it's important to test hardening products in a test environment -- if available -- to protect the integrity of production systems.
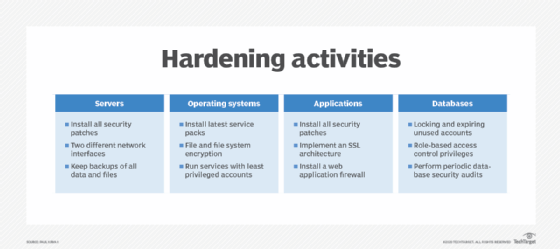
Here are some specific tasks CIOs should lead to harden key areas of their IT environment:
- Install all security patches, maintain two different network interfaces and keep backups of all data and files.
- Install latest service packs and file system encryption, and run services with least privileged accounts.
- Install all security patches, implement an SSL architecture and install a web application firewall.
- Lock all expiring and unused accounts, implement role-based access control and perform periodic database security audits.
Security hardening techniques
In addition to the perimeter hardening technologies noted in Figure 1, CIOs should build security using a defense-in-depth approach by initiating security activities for each layer, in addition to the latest firewall and intrusion detection/prevention systems rules.
While the above are highly proactive for perimeter hardening, there are two additional initiatives that CIOs should consider: vulnerability scanning and penetration testing (pen testing). These techniques thoroughly examine the internal condition of the infrastructure and identify possible anomalies for follow-up.
Software such as virus detection, distributed denial of service (DDoS) attack analysis, ransomware analysis and phishing attack analysis provide yet another layer of defense. A strategy of continuous security posture assessment and hardening helps reduce the likelihood of cyber attacks, especially considering the sophistication of today's cybercriminals.
Infrastructure hardening management
In addition to the hardware and software tools that act as active frontline defense methods to hardening IT infrastructures, CIOs should consider establishing policies and procedures for infrastructure hardening. It may be that hardening activities are part of day-to-day IT operations, but it also makes sense to document these activities, especially if an IT audit is being planned.
IT general controls (ITGCs) include numerous controls and metrics examined by IT auditors. Activities and initiatives mentioned above are among the ITGCs being audited. Key ITGCs include organization and management, communications, logical access security, physical and environmental security, change management, risk management, monitoring of controls, system operations, system availability, backup and recovery, incident management, and policies and procedures.
Hardening activities are included as part of the control matrix in several categories -- i.e., physical and logical security, environmental security, change management, system operations and availability, and backup and recovery.
Tips for hardening IT infrastructure
Based on the above discussions, we've provided the following guidelines to ensure success when implementing hardening activities:
- Implement the most current versions of software, such as service packs.
- Install the most current patches that impact security.
- Create an environment where infrastructure security is regularly monitored and the posture is analyzed.
- Analyze any variances to the security posture, and implement remedies to mitigate potential security vulnerabilities.
- Create and/or update policies that govern hardening activities.
- Create and/or update procedures that govern hardening activities.
- Validate hardening status during disaster recovery plan testing.
- Schedule and conduct periodic vulnerability scans and pen tests.
- Ensure that network perimeter tools have the most current rules for examining data traffic.
- Include infrastructure hardening in the change management process.






