What is PCI DSS (Payment Card Industry Data Security Standard)?
The Payment Card Industry Data Security Standard (PCI DSS) is a widely accepted set of policies and procedures intended to optimize the security of credit, debit and cash card transactions and protect cardholders against misuse of their personal information. PCI DSS was designed to prevent cybersecurity breaches of sensitive data and reduce the risk of fraud for organizations that handle payment card information.
PCI DSS is not a law or legal regulatory requirement. However, it is often part of contractual obligations businesses that process and store credit, debit and other payment card transactions adhere to. Contractually obligated organizations must meet the requirements of PCI DSS to establish and maintain a secure environment for their clients.
PCI DSS was created in 2004 by five major credit card companies: Visa, Mastercard, Discover, JCB and American Express. The Payment Card Industry Security Standards Council (PCI SSC) developed the guidelines for PCI DSS.

What is the purpose of PCI DSS?
The primary goal of PCI DSS is to safeguard and optimize the security of sensitive cardholder data, such as credit card numbers, expiration dates and security codes. The standard's security controls help businesses minimize the risk of data breaches, fraud and identity theft.
Compliance with PCI DSS also ensures that businesses adhere to industry best practices when processing, storing and transmitting credit card data. In turn, PCI DSS compliance fosters trust among customers and stakeholders.
What are the 6 principles of PCI DSS?
The PCI Security Standards Council (PCI SSC) has created six major goals for PCI DSS:
- Build and maintain a secure network and systems. Credit card transactions must be conducted in a secure network. The security infrastructure should include firewalls that are strong and complex enough to be effective without causing inconvenience to cardholders or vendors. Specialized firewalls are available for wireless local area networks, which are highly vulnerable to eavesdropping and malicious attacks. Vendor-provided authentication data, such as personal identification numbers and passwords, should not be used on an ongoing basis.
- Protect cardholder data. Organizations adhering to PCI DSS must protect cardholder information wherever it's stored. Repositories with vital data, such as birthdates, mothers' maiden names, Social Security numbers, phone numbers and mailing addresses, must be secure. The transmission of cardholder data through public networks must be encrypted.
- Maintain a vulnerability management program. Card services organizations must institute risk assessment and vulnerability management programs that protect their systems from the activities of malicious hackers, such as spyware and malware. All applications should be free of bugs and vulnerabilities that might enable exploits in which cardholder data could be stolen or altered. Software and operating systems must be regularly updated and patched.
- Implement strong access control measures. Access to system information and operations should be restricted and controlled. Every person who uses a computer in the system must be assigned a unique and confidential identification name or number. Cardholder data should be protected physically, as well as electronically. Physical protection can include the use of document shredders, limits on document duplication, locks on dumpsters and security measures at the point of sale.
- Regularly monitor and test networks. Networks must be regularly monitored and tested to ensure security measures are in place, functioning properly and up to date. For example, antivirus and antispyware programs should be provided with the latest definitions and signatures. These programs frequently scan all exchanged data, applications, RAM and storage media.
- Maintain an information security policy. A formal information security policy must be defined, maintained and followed by all participating entities. Enforcement measures, such as audits and penalties for noncompliance, might be necessary.
What are the 12 requirements of PCI DSS?
PCI SSC includes specific requirements in each of the six PCI DSS goals. Organizations that want to be PCI DSS-compliant must meet these 12 requirements:
- Install and maintain a firewall to protect cardholder data environments.
- Don't use vendor-supplied default passwords and other security parameters.
- Protect stored cardholder data.
- Encrypt payment card data transmitted across open, public networks.
- Use and regularly update antivirus software.
- Develop and maintain secure systems and applications.
- Restrict access to cardholder data to employees with a business need because their jobs require access.
- Assign a unique ID to each person with data or computer access.
- Restrict who has physical access to cardholder data.
- Track and monitor all access to network resources and cardholder data.
- Regularly test security systems and processes.
- Maintain an information security policy.
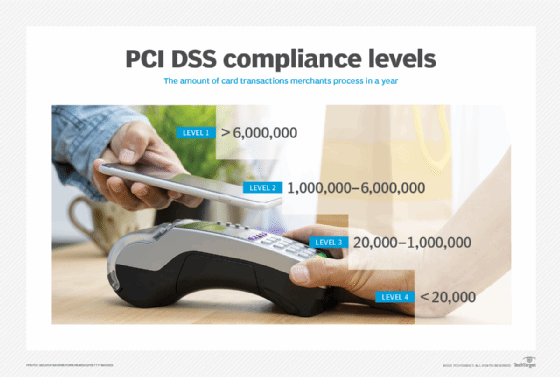
PCI DSS compliance levels
PCI DSS compliance requirements are divided into four merchant levels, based on the annual volume of credit or debit card transactions processed by a business for both e-commerce and brick-and-mortar transactions. The following are the four validation levels:
- Level 1 includes organizations that handle more than 6 million card transactions a year. These businesses must pass a Qualified Security Assessor (QSA) assessment each year and have an Approved Scanning Vendor (ASV) do a quarterly network visibility scan.
- Level 2 includes organizations that handle from 1 million annual card transactions up to 6 million. They must complete an annual Self-Assessment Questionnaire (SAQ) and might be required to submit quarterly ASV network vulnerability scans.
- Level 3 includes organizations that handle more than 20,000 annual card transactions up to 1 million. Like level 2 businesses, level 3 businesses must complete an annual SAQ and might have to submit a quarterly network vulnerability scan.
- Level 4 includes organizations that handle fewer than 20,000 annual card transactions. Like levels 2 and 3, these businesses must complete an annual SAQ and might have to submit a quarterly network vulnerability scan.
Benefits and challenges of PCI DSS compliance
PCI DSS compliance comes with several benefits and challenges.
PCI DSS benefits
Complying with PCI DSS offers several advantages for businesses in terms of protecting data and enhancing their reputation as security-conscious organizations. These benefits include the following:
- Enhanced customer trust. PCI DSS ensures the security of cardholder data, helping businesses build and maintain trust with customers. This can lead to repeat business, as well as increased customer and brand loyalty.
- Reduced risk of data breaches. PCI DSS' security controls and data protection procedures minimize the risk of data breaches and the associated costs, such as fines, legal fees and reputational damage.
- Fraud protection. PCI DSS requirements prevent and detect fraud, reducing the risk of financial loss connected to fraud.
- Compliance with industry standards. PCI DSS compliance demonstrates a commitment to industry best practices that improve a business's standing with partners, stakeholders and regulators.
PCI DSS challenges
PCI DSS compliance also poses challenges for businesses, such as the following:
- Complexity. PCI DSS' requirements cover a range of security controls that are often difficult for businesses to understand and implement, particularly for smaller companies with limited resources.
- Cost. It can be expensive to maintain and comply with PCI DSS security systems, processes, competencies and personnel, especially for smaller businesses.
- Ongoing effort. Compliance with PCI DSS requires ongoing monitoring, testing and updating of security measures to ensure continued adherence. This ongoing process requires time and resources.
- Changing environment. The payment card industry and cybersecurity landscape are constantly adapting to emerging threats and changing compliance requirements. Complying with these changing standards can be demanding for businesses.
PCI DSS compliance best practices
There are several best practices that can help businesses comply with PCI DSS and maintain a secure environment for the transmission of cardholder data. PCI SSC suggests several best practices in "Best Practices for Maintaining PCI DSS Compliance," such as the following:
- Only store cardholder data and other information that is critical to business functions.
- Develop a compliance program that includes strategic objectives and roles; policies such as strong password requirements; and procedures for completing compliance tasks.
- Develop strong performance metrics to evaluate compliance.
- Assign responsibilities and roles for compliance to knowledgeable, qualified and capable employees.
- Develop additional security requirements beyond PCI DSS specific to an organization and its industry.
- Regularly monitor and test the security systems, processes and controls to detect and address potential vulnerabilities and threats.
- Detect and address security failures; have processes in place to address breaches and failures.
- Teach and maintain security awareness to prevent breaches based on social engineering techniques, such as phishing and scareware.
- Monitor the compliance of vendor service providers.
- Dedicate resources to monitor and adapt compliance programs to changes in the cybersecurity threats.
PCI SSC suggests companies develop their own requirements and best practices outside those they recommend. These recommendations generally include self-monitoring best practices. Companies should implement risk-based approaches that prioritize security controls that address the most significant risks to cardholder data in a specific environment.
Organizations should regularly review and update their policies and procedures, while also educating employees about the importance of PCI DSS compliance and their role in protecting cardholder data. Businesses consult with QSAs, ASVs and other experts to help assess, implement and maintain PCI DSS compliance.
Find out more about best practices and tips for PCI DSS compliance.







