Security.com
Steps in the information security program life cycle
By Shon Harris
This is the third article in the Information Security Governance Guide.
A information security program is the set of controls that an organization must govern. It is important to understand that a security program has a continuous life cycle that should be constantly evaluated and improved upon otherwise inconsistent efforts open the organization to increased risk.
There are different ways of describing a life cycle of any process. We will use the following steps:
- Plan and organize
- Implement
- Operate and maintain
- Monitor and evaluate
Many organizations do not follow a life cycle approach in developing, implementing and maintaining their information security management program. This is because they don't know how or feel as though this approach is cumbersome and a waste of time. The result of not following a life cycle structure usually results in:
- Written policies and procedures that are not mapped to and supported by security activities
- Severe disconnect and confusion between the different individuals throughout the organization attempting to protect company assets
- No way of assessing progress and ROI of spending and resource allocation
- No way of fully understanding the security program deficiencies and having a standardized way of improving upon the deficiencies
- No assurance of compliance to regulations, laws or policies
- Relying fully on technology as all security solutions
- Patchwork of point solutions and no holistic enterprise solution
More on security governance
- In this tip, Michael Cobb explains how to keep a network security strategy aligned with its business goals.
- Visit our resource center for news, tips and expert advice on information security governance.
Without applying a life cycle approach to a information security program and the security management that maintains the program, an organization is doomed to treating security as a project. Anything that is treated as a project has a start and stop date, and at the stop date everyone disperses to other projects. Many organizations have good intentions in their security program kickoffs, but do not implement the proper structure to ensure that security management is an on-going and continually improving process. The result is a lot of starts and stops, and repetitive work that costs more than it should with diminishing results.
The main components of each phase are outlined below:
- Plan and organize
- Establish management commitment
- Establish oversight committee
- Assess business drivers
- Carry out a threat profile on the organization
- Carry out a risk assessment
- Develop security architectures at an organizational, application, network and component level
- Identify solutions per architecture level
- Obtain management approval to move forward
- Implement
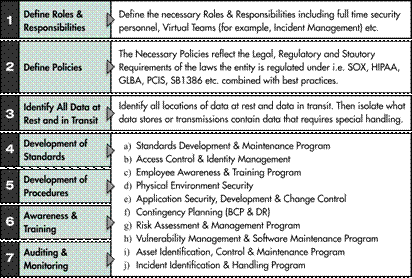
- Assign roles and responsibilities
- Develop and implement security policies, procedures, standards, baselines and guidelines
- Identify sensitive data at rest and in transit
- Implement programs
- Asset identification and management
- Risk management
- Vulnerability management
- Compliance
- Identity management and access control
- Change control
- Software development life cycle
- Business continuity planning
- Awareness and training
- Physical security
- Incident response
- Implement solutions per program
- Develop auditing and monitoring solutions per program
- Establish goals and metrics per program
- Operate and Maintain
- Follow procedures to ensure that all baselines are met in each implemented program
- Carry out internal and external audits
- Carry out tasks outlined per program
- Manage service level agreements per program
- Monitor and evaluate
- Review logs, audit results, collected metric values and SLAs per program
- Assess goal accomplishments per program
- Carry out quarterly meetings with steering committee
- Develop improvement steps and integrate into the plan and organize phase
![]()
![]() Information Security Governance Guide
Information Security Governance Guide
![]() What is information security governance?
What is information security governance?
![]() Key elements when building an information security program
Key elements when building an information security program
![]() Steps in the information security program life cycle
Steps in the information security program life cycle
![]() Developing an information security program using SABSA, ISO 17799
Developing an information security program using SABSA, ISO 17799
About the author:
Shon Harris is a CISSP, MCSE and President of Logical Security, a firm specializing in security educational and training tools. Shon is a former engineer in the Air Force's Information Warfare unit, a security consultant and an author. She has authored two best selling CISSP books, including CISSP All-in-One Exam Guide, and was a contributing author to the book Hacker's Challenge. Shon is also the co-author of Gray Hat Hacking: The Ethical Hacker's Handbook.
25 Oct 2006