ethical hacker
What is an ethical hacker?
An ethical hacker, also referred to as a white hat hacker, is an information security (infosec) expert who penetrates a computer system, network, application or other computing resource on behalf of its owners -- and with their authorization. Organizations call on ethical hackers to uncover potential security vulnerabilities that malicious hackers could exploit.
The purpose of ethical hacking is to evaluate the security of and identify vulnerabilities in target systems, networks or system infrastructure. The process entails finding and then attempting to exploit vulnerabilities to determine whether unauthorized access or other malicious activities are possible.
Origins of ethical hacking
Former IBM executive John Patrick is often credited with creating the ethical hacking term in the 1990s, although the concept and its applied practice occurred much earlier.
The term hacking first started to appear in the 1960s in connection with activities at the Massachusetts Institute of Technology and referred to applying creative engineering techniques to "hack" machinery and make it operate more efficiently. At the time, hacking was considered to be a compliment for those with exceptional skills in computer programming.
Malicious hacking became more frequent in later decades, in parallel with the commercialization of consumer-oriented computer technologies. Hackers realized computer programming languages could be used to manipulate telecommunications systems and complete long-distance calls for free, a practice dubbed phreaking.
The 1983 film War Games, in which a student inadvertently cracks into a war-game supercomputer run by the U.S. military, helped to highlight the vulnerabilities of large computing systems. In the 2000s, compliance regulations, such as the Health Insurance Portability and Accountability Act, that govern the storage and security of digitized medical and business data have elevated the role of ethical hackers within the realm of cybersecurity.
The commercialization of hacking skills, known as hacking as a service (HaaS), has made cybersecurity more complex. On the positive side, cybersecurity firms and information technology (IT) security vendors have started to offer optional ethical HaaS via contract to corporate clients. However, an underground market is flourishing on the dark web, including online marketplaces for aspiring hackers, often in the pursuit of illegal activities.
The coronavirus pandemic created new avenues of pursuit for cybercriminals. In "The Hidden Costs of Cybercrime," published in July 2020 by the Center for Strategic and International Studies and security software company McAfee, monetary losses from cybercrime in 2020 are estimated to top $945 billion. In addition, the report estimated that organizations will spend $145 billion on cybersecurity services and technologies.
What is ethical hacking?
An ethical hacker needs deep technical expertise in infosec to recognize potential attack vectors that threaten business and operational data. People employed as ethical hackers typically demonstrate applied knowledge gained through recognized industry certifications or university computer science degree programs and through practical experience working with security systems.
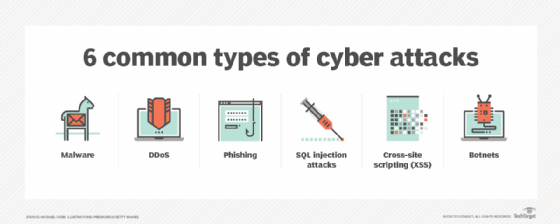
Ethical hackers generally find security exposures in insecure system configurations, known and unknown hardware or software vulnerabilities, and operational weaknesses in process or technical countermeasures. Potential security threats of malicious hacking include distributed denial-of-service attacks in which multiple computer systems are compromised and redirected to attack a specific target, which can include any resource on the computing network.
An ethical hacker is given wide latitude by an organization to legitimately and repeatedly attempt to breach its computing infrastructure. This involves exploiting known attack vectors to test the resiliency of an organization's infosec posture.
Ethical hackers use many of the same methods and techniques to test IT security measures, as do their unethical counterparts, or black hat hackers. However, rather than taking advantage of vulnerabilities for personal gain, ethical hackers document threat intelligence to help organizations remediate network security through stronger infosec policies, procedures and technologies.
Any organization that has a network connected to the internet or that provides an online service should consider subjecting its operating environment to penetration testing (pen testing) conducted by ethical hackers.
What do ethical hackers do?
Ethical hackers can help organizations in a number of ways, including the following:
- Finding vulnerabilities. Ethical hackers help companies determine which of their IT security measures are effective, which need updating and which contain vulnerabilities that can be exploited. When ethical hackers finish evaluating an organization's systems, they report back to company leaders about those vulnerable areas, which may include a lack of sufficient password encryption, insecure applications or exposed systems running unpatched software. Organizations can use the data from these tests to make informed decisions about where and how to improve their security posture to prevent cyber attacks.
- Demonstrating methods used by cybercriminals. These demonstrations show executives the hacking techniques that malicious actors could use to attack their systems and wreak havoc on their businesses. Companies that have in-depth knowledge of the methods the attackers use to break into their systems are better able to prevent those incursions.
- Helping to prepare for a cyber attack. Cyber attacks can cripple or destroy a business -- especially a smaller business -- but most companies are still unprepared for cyber attacks. Ethical hackers understand how threat actors operate, and they know how these bad actors will use new information and techniques to attack systems. Security professionals who work with ethical hackers are better able to prepare for future attacks because they can better react to the constantly changing nature of online threats.
Ethical hacking vs. penetration testing
Pen testing and ethical hacking are often used as interchangeable terms, but there is some nuance that distinguishes the two roles. Many organizations will use both ethical hackers and pen testers to bolster IT security.
Ethical hackers routinely test IT systems looking for flaws and to stay abreast of ransomware or emerging computer viruses. Their work often entails pen tests as part of an overall IT security assessment.
Pen testers seeks to accomplish many of the same goals, but their work is often conducted on a defined schedule. Pen testing is also more narrowly focused on specific aspects of a network, rather than on ongoing overall security.
For example, the person performing the pen testing may have limited access only to the systems that are subject to testing and only for the duration of the testing.
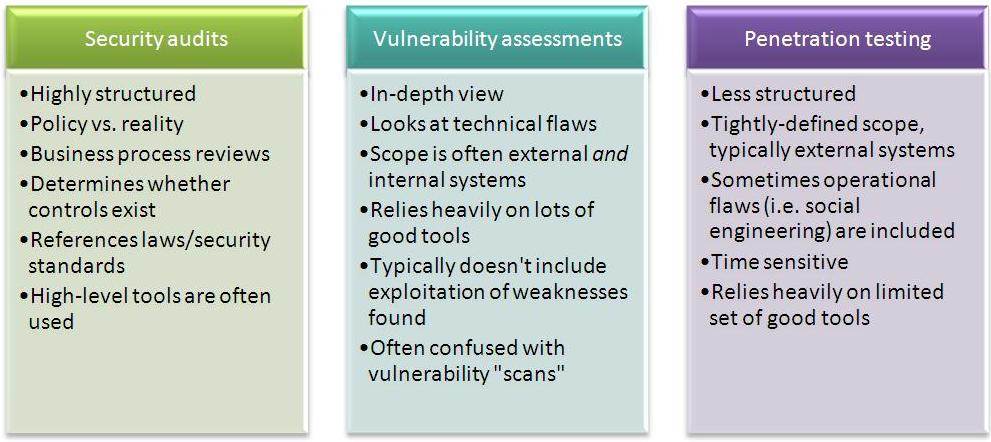 Testing is essential to the role of the ethical hacker.
Testing is essential to the role of the ethical hacker.
Ethical hacking techniques
Ethical hackers generally use the same hacking skills that malicious actors use to attack enterprises. They use a form of reverse-engineering to imagine scenarios that could compromise business and operational data. The varied techniques and tools are part of an overall vulnerability assessment the ethical hacker performs on a client's behalf.
Some of these hacking techniques include the following:
- scanning ports to find vulnerabilities with port scanning tools, such as Nmap, Nessus,Wireshark and others, looking at a company's systems, identifying open ports, studying the vulnerabilities of each port and recommending remedial action;
- scrutinizing patch installation processes to be sure that the updated software doesn't introduce new vulnerabilities that can be exploited;
- performing network traffic analysis and sniffing by using appropriate tools;
- attempting to evade intrusion detection systems, intrusion prevention systems, honeypots and firewalls; and
- testing methods to detect Structured Query Language injection to ensure malicious hackers can't introduce security exploits that expose sensitive information contained in SQL-based relational databases.
Ethical hackers also rely on social engineering techniques to manipulate end users and obtain information about an organization's computing environment. Like black hat hackers, ethical hackers rummage through postings on social media or GitHub, engage employees in phishing attacks through email or texting, or roam through premises with a clipboard to exploit vulnerabilities in physical security. However, there are social engineering techniques that ethical hackers should not use, such as making physical threats to employees or other types of attempts to extort access or information.
How to become an ethical hacker
There are no standard education criteria for an ethical hacker, so an organization can set its own requirements for that position. Those interested in pursuing a career as an ethical hacker should consider a bachelor's or master's degree in infosec, computer science or even mathematics as a strong foundation.
Individuals not planning to attend college can consider pursing an infosec career in the military. Many organizations consider a military background a plus for infosec hiring, and some organizations are required to hire individuals with security clearances.
Other technical subjects -- including programming, scripting, networking and hardware engineering -- can help those pursuing a career as ethical hackers by offering a fundamental understanding of the underlying technologies that form the systems they will be working on. Other pertinent technical skills include system administration and software development.
Certified ethical hackers
There are a number of ethical hacking certifications and related IT security certifications that help ethical hackers demonstrate their subject matter expertise. Industry certifications include the following:
- Three programs by CompTIA. Cybersecurity Analyst (CySA+), Advanced Security Practitioner (CASP+) and PenTest+. CySA+ teaches students to apply behavioral analytics to improve network security. The CASP+ certification "validates advanced-level competency" in risk management and issues related to enterprise security operations and architecture. The PenTest+ certification is geared to IT professionals engaged in pen testing and assessing vulnerabilities.
- Certified Ethical Hacker (CEH).This is a vendor-neutral certification from the International Council of Electronic Commerce Consultants (EC-Council), one of the leading certification bodies. This security certification, which validates how much an individual knows about network security, is best suited for a pen tester role. The certification covers more than 270 attacks technologies. Prerequisites for this certification include attending official training offered by EC-Council or its affiliates and having at least two years of infosec-related experience. The CEH Master certification encompasses two dozen hacking competitions and other challenges, with a focus on security for cloud computing and application containers.
- Certified Information Systems Auditor(CISA). This certification is offered by ISACA, a nonprofit, independent association that advocates for professionals involved in infosec, assurance, risk management and governance. The exam certifies the knowledge and skills of security professionals. To qualify for this certification, candidates must have five years of professional work experience related to information systems auditing, control or security.
- Certified Information Security Manager(CISM). CISM is an advanced certification offered by ISACA that provides validation for individuals who have demonstrated the in-depth knowledge and experience required to develop and manage an enterprise infosec program. The certification is aimed at infosec managers, aspiring managers or IT consultants who support infosec program management. As with the CISA certification, five years of related work experience is a prerequisite.
- GIAC Security Essentials (GSEC). This certification created and administered by the Global Information Assurance Certification organization is geared toward security professionals who want to demonstrate they are qualified for IT systems hands-on roles with respect to security tasks. Candidates are required to demonstrate they understand infosec beyond simple terminology and concepts.
- Microsoft Technology Associate Security Fundamentals. Microsoft offered this exam as a starting point for the more comprehensive Microsoft Certified Solutions Associate. As of June 2021, however, Microsoft said those exams will be discontinued in favor of its new role-based exams.
Careers for ethical hackers
In addition to industry certifications, many U.S. universities and colleges offer curricula for learning the basics of becoming an ethical hacker. As a job description, the U.S. Bureau of Labor Statistics (BLS) lumps ethical hacking into the broader category of infosec analyst.
According to BLS statistics, 131,000 people work in infosec analysis. The annual median salary is $103,590, or $49.80 per hour. BLS predicted 41,000 new infosec analyst jobs will be created by 2029, a growth rate of 31% that is much faster than the overall U.S. average.
Different types of hackers
Hacking is not always clear-cut. A gray hat hacker may expose a security exploit and publicize the findings but may not alert the system owner to take action. Gray hat hackers can provide valuable assessments of security vulnerabilities, although some also may trade this information for personal gain.
Green hat hackers are generally aspiring hackers who lack the technical acumen but display aptitude and interest in learning how to successfully hack computer machinery. Green hat hackers may include people involved in hacktivism and cyber espionage.
Blue hat hackers comprise two different types of hackers. The first type is a person skilled enough with malware to compromise computer systems, usually as a form of retaliation for perceived or real slights. Learning the trade is not a priority for this type of individual. The second type refers to someone asked to participate in Microsoft's invitation-only BlueHat security conference. Microsoft used ethical hackers to execute beta testing on unreleased products, looking for deficiencies in infosec in early software versions.
Red hat hackers are ethical hackers who specialize in cracking Linux-based systems. But, rather than turning black hats over to authorities, red hats execute a form of reverse-hacking measures to cripple the compute resources of a black hat.
TechTarget is responding to readers' concerns as well as profound cultural changes. In some cases, we are defaulting to industry standards that may be seen as linguistically biased in instances where we have not found a replacement term. However, we are actively seeking out and giving preference to terms that properly convey meaning and intent without the potential to perpetuate negative stereotypes.







