security information and event management (SIEM)
What is security information and event management (SIEM)?
Security information and event management (SIEM) is an approach to security management that combines security information management (SIM) and security event management (SEM) functions into one security management system. The acronym SIEM is pronounced "sim" with a silent e.
The underlying principles of every SIEM system are to aggregate relevant data from multiple sources, identify deviations from the norm and take appropriate action. For example, when a potential issue is detected, a SIEM system might log additional information, generate an alert and instruct other security controls to stop an activity's progress.
Payment Card Industry Data Security Standard compliance originally drove SIEM adoption in large enterprises, but concerns over advanced persistent threats have led smaller organizations to look at the benefits SIEM tools can offer as well. Being able to look at all security-related data from a single point of view makes it easier for organizations of all sizes to spot unusual patterns.
At the most basic level, a SIEM system can be rules-based or employ a statistical correlation engine to make connections between event log entries. Advanced SIEM systems have evolved to include user and entity behavior analytics, as well as security orchestration, automation and response (SOAR).
SIEM systems work by deploying multiple collection agents in a hierarchical manner to gather security-related events from end-user devices, servers and network equipment, as well as specialized security equipment, such as firewalls, antivirus programs or intrusion prevention systems (IPSes). The collectors forward events to a centralized management console, where security analysts sift through the noise, connecting the dots and prioritizing security incidents.
In some systems, pre-processing can happen at edge collectors, with only certain events being passed through to a centralized management node. In this way, the volume of information being communicated and stored can be reduced. Although advancements in machine learning are helping systems flag anomalies more accurately, analysts must still provide feedback, continuously educating the system about the environment.
How does SIEM work?
SIEM tools gather event and log data created by host systems throughout a company's infrastructure and bring that data together on a centralized platform. Host systems include applications, security devices, antivirus filters and firewalls. SIEM tools identify and sort the data into categories such as successful and failed logins, malware activity and other likely malicious activity.
The SIEM software generates security alerts when it identifies potential security issues. Using a set of predefined rules, organizations can set these alerts as a low or high priority.
For instance, a user account that generates 25 failed login attempts in 25 minutes could be flagged as suspicious but still be set at a lower priority because the login attempts were probably made by a user who had forgotten their login information.
However, a user account that generates 130 failed login attempts in five minutes would be flagged as a high-priority event because it's most likely a brute-force attack in progress.
Why is SIEM important?
SIEM makes it easier for enterprises to manage security by filtering massive amounts of security data and prioritizing the security alerts the software generates.
SIEM software enables organizations to detect incidents that may otherwise go undetected. The software analyzes the log entries to identify signs of malicious activity. In addition, since the system gathers events from different sources across the network, it can re-create the timeline of an attack, enabling an organization to determine the nature of the attack and its effect on the business.
A SIEM system can also help an organization meet compliance requirements by automatically generating reports that include all the logged security events among these sources. Without SIEM software, the company would have to gather log data and compile the reports manually.
A SIEM system also enhances incident management by helping the company's security team to uncover the route an attack takes across the network, identify the sources that were compromised and provide the automated tools to prevent the attacks in progress.
Benefits of SIEM
Benefits of SIEM include the following:
- It shortens the time it takes to identify threats significantly, minimizing the damage from those threats.
- SIEM offers a holistic view of an organization's information security environment, making it easier to gather and analyze security information to keep systems safe. All an organization's data goes into a centralized repository where it's stored and easily accessible.
- Companies can use SIEM for a variety of use cases that revolve around data or logs, including security programs, audit and compliance reporting, help desk and network troubleshooting.
- SIEM supports large amounts of data so organizations can continue to scale out and add more data.
- SIEM provides threat detection and security alerts.
- It can perform detailed forensic analysis in the event of major security breaches.
Limitations of SIEM
Despite its benefits, SIEM also has the following limitations:
- It can take a long time to implement SIEM because it requires support to ensure successful integration with an organization's security controls and the many hosts in its infrastructure. It typically takes 90 days or more to install SIEM before it starts to work.
- It's expensive. The initial investment in SIEM can be in the hundreds of thousands of dollars. And the associated costs can add up, including the costs of personnel to manage and monitor a SIEM implementation, annual support and software or agents to collect data.
- Analyzing, configuring and integrating reports require the talent of experts. That's why some SIEM systems are managed directly within a security operations center, a centralized unit staffed by an information security team that deals with an organization's security issues.
- SIEM tools usually depend on rules to analyze all the recorded data. The problem is that a company's network could generate thousands of alerts per day. It's difficult to identify potential attacks because of the number of irrelevant logs.
- A misconfigured SIEM tool might miss important security events, making information risk management less effective.
SIEM features and capabilities
Important features to consider when evaluating SIEM products include the following:
- Data aggregation. Data is collected and monitored from applications, networks, servers and databases.
- Correlation. Typically a part of SEM in a SIEM tool, correlation refers to the tool finding similar attributes between different events.
- Dashboards. Data is collected and aggregated from applications, databases, networks and servers and is displayed in charts to help find patterns and to avoid missing critical events.
- Alerting. If a security incident is detected, SIEM tools can notify users.
- Automation. Some SIEM software might also include automated functions, such as automated security incident analysis and automated incident responses.
Users should also ask the following questions about SIEM product capabilities:
- Integration with other controls. Can the system give commands to other enterprise security controls to prevent or stop attacks in progress?
- Artificial intelligence (AI). Can the system improve its own accuracy through machine learning and deep learning?
- Threat intelligence feeds. Can the system support threat intelligence feeds of the organization's choosing, or is it mandated to use a particular feed?
- Extensive compliance reporting. Does the system include built-in reports for common compliance needs and provide the organization with the ability to customize or create new compliance reports?
- Forensic capabilities. Can the system capture additional information about security events by recording the headers and contents of packets of interest?
SIEM tools and software
There are a wide variety of SIEM tools on market, but the following is just a sample:
- Splunk. Splunk is an on-premises SIEM system that supports security monitoring and offers continuous security monitoring, advanced threat detection, incident investigation and incident response.
- IBM QRadar. The IBM QRadar SIEM platform provides security monitoring for IT infrastructures. It features log data collection, threat detection and event correlation.
- LogRhythm. LogRhythm is a SIEM system for smaller organizations. It unifies Log Management, network monitoring and endpoint monitoring, as well as forensics and security analytics.
- Exabeam. Exabeam Inc.'s SIEM portfolio offers a data lake, advanced analytics and a threat hunter.
- NetWitness. The RSA NetWitness platform is a threat detection and response tool that includes data acquisition, forwarding, storage and analysis.
- Datadog Cloud SIEM. Datadog Cloud SIEM from Datadog Security is a cloud-native network and management system. The tool features both real-time security monitoring and log management.
- Log360. The Log360 SIEM tool offers threat intelligence, incident management and SOAR features. Log collection, analysis, correlation, alerting and archiving features are available in real time.
- SolarWinds Security Event Manager. The SolarWinds Security Event Manager SIEM tool automatically detects threats, monitors security policies and protects networks. The tool offers features such as integrity monitoring, compliance reporting and centralized log collection.
How to choose the right SIEM product
The key to selecting the right SIEM tool varies depending on a number of factors, including an organization's budget and security posture. However, companies should look for SIEM tools that offer the following capabilities:
- compliance reporting;
- incident response and forensics;
- database and server access monitoring;
- internal and external threat detection;
- real-time threat monitoring, correlation and analysis across a variety of applications and systems;
- an intrusion detection system, IPS, firewall, event application log, and other application and system integrations;
- threat intelligence; and
- user activity monitoring.
Best practices to implementing SIEM
Follow these best practices while implementing SIEM:
- Set understandable goals. The SIEM tool should be chosen and implemented based on security goals, compliance and the potential threat landscape of the organization.
- Apply data correlation rules. Data correlation rules should be implemented across all systems, networks and cloud deployments so data with errors in it can be more easily found.
- Identify compliance requirements. This helps ensure the chosen SIEM software is configured to audit and report on correct compliance standards.
- List digital assets. Listing all digitally stored data across an IT infrastructure aids in managing log data and monitoring network activity.
- Record incident response plans and workflows. This helps ensure teams can respond to security incidents rapidly.
- Assign a SIEM administrator. A SIEM administrator ensures the proper maintenance of a SIEM implementation.
History of SIEM
SIEM technology, which has existed since the mid-2000s, initially evolved from log management, which is the collective processes and policies used to administer the generation, transmission, analysis, storage, archiving and disposal of large volumes of log data created within an information system.
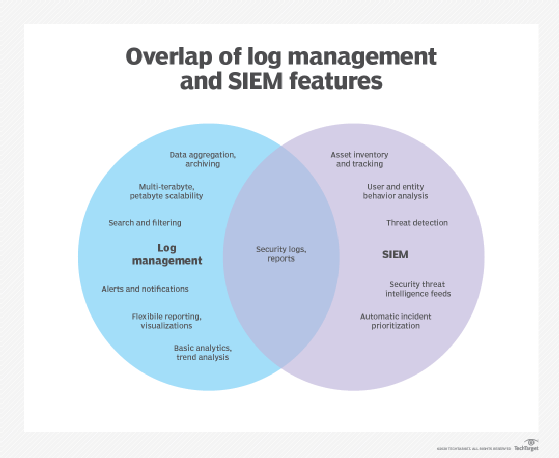
Gartner Inc. analysts coined the term SIEM in the 2005 Gartner report, "Improve IT Security with Vulnerability Management." In the report, the analysts proposed a new security information system based on SIM and SEM.
Built on legacy log collection management systems, SIM introduced long-term storage analysis and reporting on log data. SIM also integrated logs with threat intelligence. SEM addressed identifying, collecting, monitoring and reporting security-related events in software, systems or IT infrastructure.
Vendors created SIEM by combining SEM, which analyzes log and event data in real time, providing threat monitoring, event correlation and incident response, with SIM, which collects, analyzes and reports on log data.
SIEM is now a more comprehensive and advanced tool. New tools were introduced for reducing risk in an organization, such as the use of machine learning and AI to help systems flag anomalies accurately. Eventually, SIEM products with these advanced features started being called next-generation SIEM.
The future of SIEM
Future SIEM trends include the following:
- Improved orchestration. Currently, SIEM only provides companies with basic workflow automation. However, as these organizations continue to grow, SIEM must offer additional capabilities. For example, with AI and machine learning, SIEM tools must offer faster orchestration to provide the different departments within a company the same level of protection. Additionally, the security protocols and the execution of those protocols will be faster, more effective and more efficient.
- Better collaboration with managed detection and response (MDR) tools. As threats of hacking and unauthorized access continue to increase, it's important that organizations implement a two-tier approach to detect and analyze security threats. A company's IT team can implement SIEM in-house, while a managed service provider can implement the MDR tool.
- Enhanced cloud management and monitoring. SIEM vendors will improve the cloud management and monitoring capabilities of their tools to better meet the security needs of organizations that use the cloud.
- SIEM and SOAR will evolve into one tool. Look for traditional SIEM products to take on the benefits of SOAR; however, SOAR vendors will likely respond by expanding the capabilities of their products.
According to a recent Forbes article, the future of SIEM may involve the following five possible outcomes:
- Usage-based pricing models for SIEM will become common.
- Analysis tools will be built on universal SIEM data platforms.
- Organizations will partner to provide more integrations.
- The cost of SIEM will drop, making SIEM more affordable for smaller security teams.
- Startups will address more of the multifaceted challenges of managing security.
Learn more about SIEM products, including product architectures and the cost of adopting, deploying and managing SIEM systems.






