WLAN security: Best practices for wireless network security
Follow these wireless network security best practices to ensure your company's WLAN remains protected against the top threats and vulnerabilities.
For many businesses, wired Ethernet is no longer supreme. Instead, IEEE 802.11 Wi-Fi has become the go-to network access technology for users and endpoints. Wireless LANs offer many advantages over their wired alternatives. They are reliable and flexible, and they can reduce cost of ownership. WLANs offer easy installation, the ability to move and not be tied to a physical location, and scalability.
With the advantages, however, comes a major disadvantage: security. Wi-Fi's borderless nature -- in combination with a confusing array of legacy and modern authentication, access control and encryption techniques -- makes WLAN security an overwhelming challenge.
Implementing WLAN security measures is complex, so let's break it down in steps. First, we discuss some common WLAN threats enterprises face when the correct security policy isn't in place. Then, we examine the history of WLAN security and the techniques security engineers consider to be the best. Finally, we detail some WLAN best practice security guidelines.
What is WLAN security?
WLAN cybersecurity threats can lead to data theft. To prevent against this risk, security teams put mechanisms in place to stop attempts to read communications being transmitted or received over the wireless medium and collect sensitive information, such as personal information, login credentials or business data.
Teams can use several methods to protect Wi-Fi communications. Some of these methods are generic and help manage both wired and wireless communications risks. These methods include enterprise-grade authentication mechanisms, restricting corporate network access by way of media access control (MAC) address allowlisting, network- and device-based antivirus and malware services, and the use of third-party VPNs.
However, most businesses use a built-in encryption protocol. This forces all Wi-Fi communications to encrypt their data prior to being sent and requires the receiving side to have a decryption code to unencrypt the data once it reaches its destination.
WLAN threats and vulnerabilities
WLAN cybersecurity threats can lead to data loss, malware infections, DDoS attacks and other detrimental scenarios. Teams should be aware of many WLAN threats and vulnerabilities, including the following:
- IP and MAC spoofing. If bad actors successfully connect to the corporate WLAN, they can use tools to impersonate -- or spoof -- trusted devices by changing the source IP address in the packet header or by manipulating an allowlisted device's MAC address. In turn, receiving devices might unknowingly accept the spoofed communications. DDoS botnets and man-in-the-middle attacks are among the most common tactics employed with spoofing.
- DNS cache spoofing/poisoning. DNS spoofing is the act of placing an unauthorized device on the WLAN to spoof the DNS server that other connected clients use. In turn, the spoofed DNS server redirects users and devices that attempt to access a trusted remote resource, such as a website, to a malicious one.
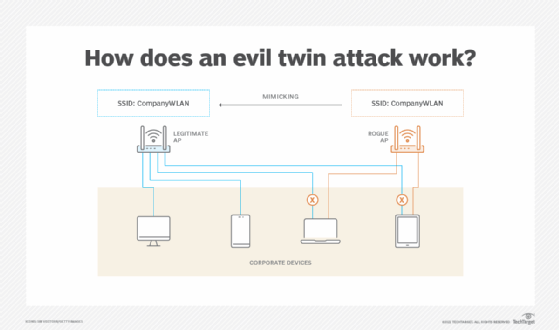
- Rogue/evil twin access points (APs). These occur when bad actors deploy a wireless AP that uses the same or similar-looking service set identifier (SSID). Unsuspecting users connect to the rogue device, where traffic can then be captured and monitored, or are even redirected to malicious destinations.
![Graphic describing how an evil twin access point works]()
An evil twin AP mimics a corporate SSID as it attempts to have company devices connect to it instead of the legitimate AP. - War driving. When WLAN signals propagate outside company walls and into public spaces, war drivers search for open or exploitable WLANs to use for free internet access -- called piggybacking. Bad actors can also use war driving for more nefarious reasons, such as attempting to find and steal sensitive corporate data.
How WLAN security standards have evolved over time
Early iterations of Wi-Fi focused more on connectivity, as opposed to security. As a result, WLAN security protocols were designed to provide secure access.
WEP
The Wired Equivalent Privacy (WEP) standard, introduced in the late 1990s, was the first attempt to keep hackers from accessing wireless traffic, but it was fatally flawed. WEP relied solely on pre-shared keys (PSKs) to authenticate devices. Users didn't change PSKs frequently enough, however, and hackers found they could use simple tools to crack the statically encrypted key in a few minutes.
WEP is now considered to be woefully insecure and should be removed from corporate use.
WPA
In 2003, the Wi-Fi Alliance introduced a new standard, Wi-Fi Protected Access (WPA). WPA offered a more secure encryption mechanism. The initial WPA uses a stronger, per-packet key encryption foundation, dubbed Temporal Key Integrity Protocol (TKIP).
WPA2, released in 2004, made configuration management easier and added Advanced Encryption Standard (AES) for stronger security protection.
WPA3 uses even stronger encryption mechanisms. Because it was introduced in 2018, however, many legacy devices don't support WPA3. As a result, organizations commonly deploy a combination of the three WPA protocols to protect their corporate WLANs.
Teams commonly configure WPA using one of two authentication key distribution methods:
- WPA-Personal, also known as WPA-PSK, is based on a shared password users employ to gain network access. Because this authentication technique is shared, it's considered less secure than WPA-Enterprise.
- WPA-Enterprise, also known as WPA-Extensible Authentication Protocol (WPA-EAP), uses 802.1x RADIUS to connect to a user database containing individual usernames and passwords. With WPA-EAP, each user must enter a valid username and associated password before gaining access to the WLAN. This method is considered secure because no passwords are shared between users and devices.

WLAN cryptographic algorithms
Enterprise-grade WLANs can use different types of wireless security standards. The cryptographic security algorithm varies depending on the security protocol used. This is an important concept to grasp, as the security algorithm is what protects transmitted and received data from being accessed -- and the effectivity of that protection differs depending on a bad actor's ability to crack the security algorithm.
The following security algorithms are most common in current WLAN environments.
WEP
Based on Rivest Cipher 4 (RC4), the WEP encryption algorithm can use a 40-, 104- or 232-bit long key to encrypt data sent across Wi-Fi. The problem with WEP is these keys are static in nature and must be manually changed. If a key isn't updated regularly, bad actors can crack it in relatively short order. Thus, WEP is not recommended for enterprise use.
TKIP
Also based on RC4, TKIP uses the same cipher stream as WEP. However, the major difference with TKIP is the algorithm automatically changes the key over time and communicates those changes to the sending and receiving device. Additionally, the key size is bumped to 128 bits in length. These two factors eliminate much of the risk found in WEP, as cracking the encryption key takes time. In theory, by the time a bad actor cracks the 128-bit key and attempts to use it to steal data, the algorithm has already shifted and moved to a new key.
The rekey component of TKIP creates brand-new shared encryption keys each time 10,000 packets are sent, and it mixes the use of multiple keys on a per-packet basis. Additionally, TKIP implements a cryptographic integrity check hashing mechanism on packets, so the data payload is not sent in plaintext, as is the case with WEP. This helps protect against spoofing attacks.
From a WLAN perspective, TKIP is used when implementing the WPA security standard.
CCMP
Moving beyond shared key and shared key rotation, as used with WEP and WPA, respectively, the Counter Mode with Cipher Block Chaining Message Authentication Code Protocol (CCMP) algorithm is based on AES, which relies on the Rijndael symmetric block cipher.
CCMP uses cipher keys that are 128 bits long and block sizes that are 128 bits. While both TKIP and CCMP technically use 128-bit keys, TKIP combines the root key with the initialization vector. In contrast, CCMP uses the entire 128 bits to create the key. Additionally, CCMP requires checks to guarantee that only authorized receiving devices can decrypt the data, as opposed to TKIP's method of using less secure message integrity verification checks.
CCMP is used with the WPA2 and WPA3 encryption standards.
WLAN security checklist
When researching how to secure WLAN networks, network and security teams can use the following checklist to ensure they cover all the bases:
- Research production devices, and determine what is the highest level of encryption possible.
- If they must use less secure security standards, determine if these less secure devices can operate on a logically segmented wireless network using separate SSIDs.
- When possible, use 802.1x authentication methods, as opposed to PSKs.
- Provide guest access that allows access only to the internet.
- Implement network- and device-based security tools, such as firewalls, intrusion prevention systems and antivirus/malware prevention.
- Perform regular security patch maintenance on wireless APs and controllers.
- Physically secure Wi-Fi APs to prevent tampering.
- Conduct wireless scans of the WLAN to identify rogue APs.
- Create WLAN usage policies to help enforce proper usage and prevent password sharing.
WLAN security best practice tips
Enterprises should carefully plan and execute a cohesive strategy to protect their WLANs against data loss and unauthorized access. While the final security options depend on the level of protection required and available budget, teams can follow some important tips and techniques.
As with anything security, ensure IT security policies define access requirements: Who needs access to what and when? Include remote and on-the-go employees, too.
Other best practices include the following:
- Segmentation of Wi-Fi users and devices by SSID. Departments and devices use WLANs in different ways. Therefore, teams can't secure every device using the same standard. For example, one way to protect devices that support WPA-Enterprise from those that support only WPA-Personal is to segment legacy devices logically into a separate SSID. Once segmented, teams can wrap access policies around the less secure endpoints.
- Guest Wi-Fi. Set up a separate guest Wi-Fi SSID for those users and devices that only require internet access. Access policies can block these devices from communicating with any users or devices on the corporate network, while still delivering internet-bound traffic securely beyond the network edge.
- Avoiding signal strength bleeding out into insecure areas. APs installed near external walls should have their power levels carefully set to reduce any leakage into nearby parking lots or public squares. Doing so helps protect against external wireless interference and reduces the chance an unauthorized user can successfully connect to the network.
- Rogue AP detection. Most enterprise-grade WLAN platforms include tools that monitor the 802.11 wireless frequency ranges to identify rogue APs -- or those potentially spoofing corporate SSIDs.
- 802.1x authentication vs. PSK. Whenever possible, require users and devices to authenticate using 802.1x, as opposed to a PSK. This reduces the need to manually change PSKs multiple times a year. It also prevents the sharing of PSKs, which can potentially lead to hackers using Wi-Fi to gain unauthorized access to the corporate network.
- Network LAN switchport configurations. Configure the switchports that connect wireless APs to the corporate LAN with security in mind. Place AP management IP addresses on a segmented virtual LAN, allowing only specific VLANs to be trunked to the APs. Use static or sticky MAC address port security techniques to protect against people unplugging an AP and attaching an unauthorized device into the LAN.
- Employment of external security tools that further secure WLANs. Supplement with other tools to protect users, devices and data transported across the WLAN. Examples include the following:
- network access control or unified endpoint management platforms to provide granular access controls;
- VPN technologies to protect when sensitive data is transmitted or received across insecure Wi-Fi connections; and
- AI-backed network detection and response platforms that can monitor traffic flows and alert personnel when users, devices or traffic flows veer from normal behavior, a sign that some form of WLAN compromise may be occurring.
Other standard security best practices also apply, including the following:
- Use firewalls and antimalware.
- Ensure secure remote access via VPNs, zero-trust network access or Secure Access Service Edge.
- Keep software patched and up to date.
- Change any default credentials.
- Educate users about security.
- Keep up to date with current security threats.