browser hijacker (browser hijacking)
What is a browser hijacker?
A browser hijacker is a malware program that modifies web browser settings without the user's permission and redirects the user to websites the user had not intended to visit. It is often called a browser redirect virus because it redirects the browser to other, usually malicious, websites.
Part of the aim of a browser hijacker is to help the cybercriminal generate fraudulent advertising revenue. For instance, a browser redirects the victim's homepage to the hijacker's search page. Next, the hijacker redirects a victim's web searches to links the hijacker wants the victim to see, rather than to legitimate search engine results. When the user clicks on the search results, the hijacker gets paid. The cybercriminal can also sell information about the victim's browsing habits to third parties for marketing purposes.
A browser hijacker may contain spyware, enabling the attacker to obtain the user's banking information, credit card number or other sensitive data. Browser hijackers may also install ransomware, a type of malware that encrypts data on the victim's system, holding it hostage until the victim pays the hijackers a sum of money to unlock it.
How does browser hijacking work?
Browser hijackers can infect devices through malicious email attachments, by downloading infected files or by visiting infected websites. The browser hijacking software could be bundled with a browser extension or be part of the software. Browser hijackers can also originate from shareware, freeware, adware and spyware infections.
Browser hijackers are likely to be downloaded unintentionally by the user. The user may be tricked into agreeing to an additional download in the terms and conditions to install software. The victim may also be fooled after being offered the option to decline the installation of the browser hijacker software, but the query is worded in a way that deliberately confuses the user into downloading the software. Once installed by the user, malicious code embedded in the software begins altering the activity of the user's browser.
The browser settings targeted by browser hijacking vary depending on the hijacker and their goals. Some hijackings may make only small changes -- such as adding a new and unwanted toolbar. These changes tend to be more annoying than dangerous. But the more dangerous hijackings may target the domain name system (DNS) to redirect users to a dangerous website, possibly to steal their passwords and user credentials.
What are the impacts of browser hijacking?
Knowing what the effects of browser hijacking are can help users determine if they have been highjacked. They are as follows:
- changes made to a web browsing homepage, including mods to search engine preferences or the addition of unwanted toolbars;
- a major increase in pop-up ads that slow the computer down;
- a web browser is redirected to dangerous websites;
- unauthorized software is forced into the browser or the browser's toolbar; and
- modifications made beyond the browser -- changes can be made to registry entries to remain on the infected system, and the software can then be used to spy on users, access accounts or harvest data.
How can you tell if you have a browser hijacker?
A system infected with a browser hijacker may show a few obvious signs of infections. Users should watch out if they are experiencing:
- searches that are being redirected to other websites;
- multiple pop-up advertisements;
- slow-loading webpages;
- their search engine has been replaced; or
- one or more unauthorized toolbars appear on their internet browser.
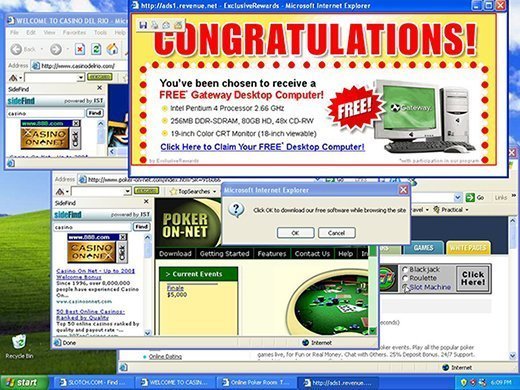
Hijacked devices may not always show signs of infection, however. Browser hijackers meant to go unnoticed may try to spy on the user's activity and collect data.
How do you remove browser hijackers?
Depending on the circumstances, browser hijacker removal can be relatively straightforward. Different actions to take include the following:
- Use a program such as an antivirus or antimalware software that specializes in spyware removal. Users can scan and remove unwanted toolbars.
- Automated tools can automatically delete browser hijacker-associated files and modifications on the registry.
- Clearing the system's DNS cache can also eliminate connections to malicious programs if the browser has been hijacked.
- Use the browser settings tool to reset the browser homepage. In some cases, simply resetting browser settings to the original defaults will remediate the attack. If not, the browser can be uninstalled and then reinstalled.
- If the other options do not work, browser hijacker infections can be manually removed from devices. On Windows 10 systems, for example, browser hijackers can be removed by using the uninstall program in the Windows control panel.
How do you prevent browser hijacking?
There are several ways to protect against browser hijacking, including:
- Stay current on operating system (OS) and browser patches. The latest security features can help prevent hijacking attacks, as hijackers typically exploit known vulnerabilities in the OS and browser. Running a software update can help shut down these points of entry.
- Avoid clicking on suspicious links. Users should never click on email links, messages or pop-up boxes that come from unknown senders. They could initiate the download of browser hijackers.
- Be careful about downloading software. Some browser hijacking software is bundled with legitimate software, so users should read all terms and conditions and end-user licensing agreements before downloading any software.
- Use antivirus software. Installing good antivirus software and keeping it updated with the latest patches helps defend against browser hijacking. Some antivirus software offer protection in Real Time, warning the user if downloaded software tries to change browser settings. Some antivirus software enable the user to stop those changes from being made.
- Avoid running freeware programs that may unpack software on installation. Check the download settings of software before installing.

Learn how to stop malicious browser add-ons in this article.







