Ultimate guide to secure remote access
This comprehensive secure remote access guide outlines the strategies, tools and best practices to provide anywhere access while protecting data, systems and users.
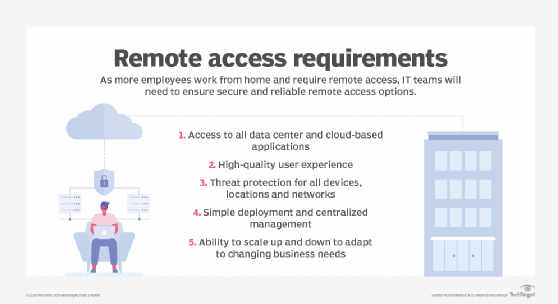
Secure remote access is one of the most critical aspects of networking and security today -- even more so because of the COVID-19 pandemic, which forced employers to expand and fortify their remote work capabilities. Companies need to provide employees and business partners remote access to resources, such as applications and data, without compromising security. In this guide, we examine how businesses should rethink key aspects of their secure remote access strategies, set policies accordingly and get to know the entirety of the secure remote access ecosystem.
What is secure remote access?
What it means to provide secure remote access has changed considerably in the past few years as a result of new technologies and the pandemic. At its most basic, secure remote access is having location-agnostic connectivity among enterprise users and centralized applications, resources and systems, whether cloud-based or on premises.
The following technologies can contribute to secure remote access:
- VPNs;
- intrusion prevention systems and intrusion detection systems;
- Secure Access Service Edge (SASE) and software-defined perimeter;
- firewalls;
- cloud access security brokers;
- zero-trust network access;
- virtual desktop infrastructure; and
- identity and access management (IAM).
Some of these technologies are explained in deeper detail below.
Who is responsible for secure remote access?
Although remote access tools, such as VPNs and firewalls, are typically under the purview of network teams, in this new era, cybersecurity teams tend to lead and manage the policies, processes and technologies associated with ensuring secure remote access.
Cybersecurity teams assess and mitigate the risks of remote access, including the following:
- password sharing;
- software that violates an organization's security standards;
- unencrypted personal devices and lack of cyber hygiene; and
- minimal to no patching.
Their responsibilities involve combating the top cybersecurity risks by strengthening and measuring the effectiveness of access controls, monitoring and managing remote access activities, keeping remote access rules current and testing remote access operations.
The diminishing power of VPNs
One tactic organizations use to combat the vulnerabilities associated with working remotely -- especially if employees are using consumer-grade systems -- is to reestablish VPN standards. This entails enforcing basic protections, such as strong passwords, multifactor authentication, role-based access and encryption.
That said, many experts believe VPNs have not scaled well to meet the accelerated needs of secure remote access for a hybrid workforce. As a result, VPNs will likely be replaced with more nimble technology over time.
Setting secure remote access policies
A hallmark of secure remote access is the underlying policy that safeguards access to and the use of enterprise resources, such as data, databases, systems and networks.
Cybersecurity expert Paul Kirvan recommended defining the following procedures and processes, among others:
- criteria for granting employees remote access;
- technologies used for remote access and minimally required security features;
- types of IT resources to be remotely accessed;
- network resources needed for remote access;
- IT employees charged with executing remote access security activities;
- emergency procedures in case of remote access security compromise; and
- integration of remote access security with other data protection activities.
Remote access security policy template
This free, editable remote access security policy template provides suggested wording for the policy and identifies areas to be completed by the policy author(s). The template can be modified in any way your policy development team sees fit.
Components of the secure remote access ecosystem
Secure remote access touches just about every aspect of enterprise security. TechTarget has curated a series of guides to help IT and security professionals get up to speed on important technologies and concepts.
The following guides are relevant to the secure remote access ecosystem.
Zero trust and secure remote access
Cybersecurity and IT teams realize words like perimeter and trust are quickly becoming outdated as borders dissolve and the base of users that need access to resources expands. No longer are organizations protected by four castle walls, with a firewall moat keeping miscreants out.
Many security teams today are turning to the concept of zero trust. A zero-trust model is based around the idea of "never trust, always verify." An alternative to traditional perimeter security, zero trust's continuous verification is a key component of securing a remote workforce reliant on the cloud.
Learn more about this networking security model in our ultimate guide to zero trust.
SASE and secure remote access
Secure Access Service Edge is an emerging concept that combines network and security functions into a single cloud service, not only to alleviate traffic from being routed through the data center, but also to embrace a remote workforce, IoT adoption and cloud-based application use.
With a SASE framework, enterprises can maintain edge-to-edge security while connecting remote users, preventing bottlenecks and improving performance.
Learn more about this cloud architecture model in our complete SASE guide.
SD-WAN and secure remote access
Wide area networks are mainstays in distributed organizations, connecting headquarters, branch offices, cloud services and users across multiple locations. They can be challenging to manage, however, as well as costly and time-consuming. WANs can also hinder traffic and performance depending on their architecture, and they introduce several security challenges.
Software-defined WANs can help organizations overcome the challenges of traditional WANs, providing a network overlay that enables IT to remotely configure, manager, monitor and secure most WANs, including edge devices and remote employees.
Learn more about the technology and its role in secure remote access in our ultimate guide to SD-WAN architecture.
Cloud security and secure remote access
The cloud is instrumental in managing a remote workforce, enabling users to access resources regardless of location. Cloud access can improve productivity, collaboration and employee satisfaction, but clouds also introduce security challenges that must be addressed.
While instrumental in enabling cybersecurity teams to oversee remote access with adaptive strategies, policies and tools, cloud use must be approached with proper planning, security measures and best practices in place to prevent specific cloud risks and vulnerabilities.
Learn more in our guide to cloud security management and best practices.
SecOps and secure remote access
The term SecOps refers to a highly skilled team made up of security and IT operations staff that mitigate risk in an organization. The increase in volume and velocity of cyber attacks combined with the challenge of accommodating a hybrid or remote workforce in the modern enterprise has compounded the need for SecOps.
To build a team that can support a combination of remote and on-premises work while maintaining security, be sure to include key roles in SecOps teams, use effective SecOps tools, manage cloud security, embrace automation and AI, and implement SecOps best practices.
Learn more in our guide to SecOps.

IAM and secure remote access
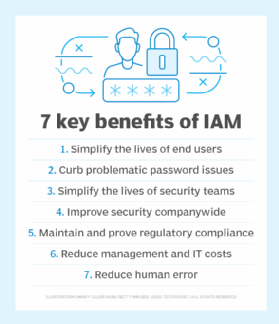
Managing a vast universe of remote and on-premises users requires a sophisticated approach. IAM has become a suitable solution for the secure remote access needs of employees, contractors, business partners, remote and mobile users, customers and devices. With cloud, on-premises and hybrid options, IAM is a flexible way to protect network resources while adapting to the diverse user needs of remote work environments.
Learn more about the framework of processes, policies and technologies that comprise IAM in our guide to identity and access management.







