
The differences between inbound and outbound firewall rules
Firewalls can support both inbound and outbound firewall rules, but there are important differences between the two. Learn more about each and their uses.
It is critical to compare the roles of inbound and outbound firewall rules before deploying a corporate firewall to ensure it properly secures an enterprise IT environment.
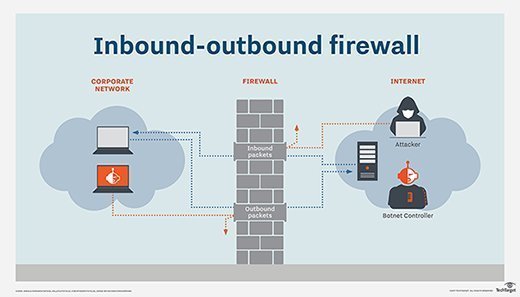
Simply put, inbound firewall rules protect the network from unwanted incoming traffic from the internet or other networks -- in particular, disallowed connections, malware and DoS attacks. Outbound firewall rules control outgoing traffic -- that is, requests to resources outside of the network. For example, a connection request to an email service or the TechTarget website might be allowed, but connection requests to unapproved or dangerous websites are stopped.
A single firewall typically serves both functions, but it's essential to understand the differences -- as well as the benefits and drawbacks -- of inbound and outbound firewall rules.
Inbound traffic versus outbound traffic
Enterprise networks have both inbound traffic and outbound traffic. Inbound requests originate from outside the network, such as a user with a web browser, email client, server or application making requests -- like FTP and SSH -- or API calls to web services.
Outbound requests originate from inside the network, destined for services on the internet or outside networks.
Firewalls are designed and deployed to prevent inbound traffic from entering a network and to stop outbound traffic from connecting to external resources that are noncompliant with an organization's security policies.
The difference between inbound and outbound firewall rules
Firewall rules, which are either inbound or outbound, can be customized to allow traffic on specific ports, services and IP addresses to enter or leave the network:
- Inbound firewall rules protect a network by blocking traffic known to be from malicious sources. This stops various attacks, such as malware and DDoS, from affecting internal resources.
- Outbound firewall rules define the traffic allowed to leave a network and reach legitimate destinations. These rules also block requests sent to block requests sent to malicious websites and untrusted domains. They can also prevent data exfiltration by analyzing the contents of emails and files sent from a network.
The firewall policy that governs the configuration of inbound and outbound rules is based on a risk assessment of the assets it is protecting and the business needs for users and services inside the network. For example, the HR department might be allowed access to the internet and the company's accounting department's network but not vice versa.
Any changes to inbound and outbound firewall rules should be carefully planned, implemented and monitored to avoid unforeseen consequences, among them blocking valid requests, which can throttle legitimate business activities and frustrate users.
Using inbound firewall rules
For years, firewalls have protected internal network systems from outside threats by enforcing rules that control the flow of inbound traffic. The goal of inbound firewall rules is to keep malicious traffic out of a network and protect resources located within it.
Firewalls can be located at various points within a network -- most certainly on the perimeter where the network connects to the internet but also within an organization's own network to divide it into smaller individual subnetworks, known as network segmentation. This approach enables each firewall's inbound rules to be configured to protect the specific resources on each segment. For example, the firewall protecting the HR segment of the network only permits inbound requests from HR employees with the necessary privileges. A firewall protecting the network perimeter, meanwhile, has less restrictive rules. These rules, however, are based on threat intelligence and block traffic from known bad IP addresses or locations.
Using outbound firewall rules
Outbound firewall rules also protect internal network resources, but they work by preventing internal users from accessing malicious content, as well as by keeping sensitive data from leaving the network in violation of security policy rules. For example, outbound firewall rules can be beneficial in locked-down environments that need to control network behavior down to the host, application and protocol levels. Monitoring and controlling outbound traffic via firewall rules are important tasks for security teams as they can prevent the exfiltration of sensitive data or other activities involving malware and malicious insiders.
A dedicated firewall appliance or an off-site cloud service, such as a secure web gateway, is sometimes used to control outbound traffic because of the specialized filtering technologies necessary. Such systems can perform targeted functions, such as content filtering for email or web browsing. They often tie into the business's directory service -- Active Directory and Lightweight Directory Access Protocol -- so they can provide access, filtering and reporting based on each user's network account.
Other firewall systems look for outbound malware and security-related threats, including DNS lookups to hosts known to be threatening or blocklisted.
Firewalls are constantly evolving and will always be a key security control in any network. Modern firewalls use threat intelligence feeds, AI and machine learning to update inbound and outbound rules on the fly, enabling them to combat new and emerging threats as they develop.
Remember that inbound and outbound firewall rules require careful configuration, as well as monitoring for system anomalies. Even the most secure firewalls can only do so much. Those enterprises without the necessary internal resources -- among them product training and security knowledge -- might consider outsourcing the management of their firewall environments to an outsourced managed security service provider (MSSP). A dedicated, 24/7 MSSP network security monitoring service is often the best way to minimize associated risks.
Michael Cobb, CISSP-ISSAP, is a renowned security author with more than 20 years of experience in the IT industry.
Kevin Beaver is an independent information security consultant, writer and professional speaker with Atlanta-based Principle Logic LLC. With more than 30 years of experience in the industry, he specializes in performing vulnerability and penetration tests, as well as virtual CISO consulting work.







