
kras99 - stock.adobe.com
How to defend against TCP port 445 and other SMB exploits
Keeping TCP port 445 and other SMB ports open is necessary for resource sharing, yet this can create an easy target for attackers without the proper protections in place.
When ports are being discussed, the focus most of the time is on the well-known web ports 80 and 443. But, as security admins know, many other Internet Assigned Numbers Authority ports are in use. One that got a lot of attention just a few years ago is port 445, which was exploited as part of the WannaCry and NotPetya ransomware attacks.
Let's look at what port 445 is, why it can pose risks to organizations, how to detect a port 445 attack and how security professionals can support file sharing without putting company assets and information at risk.
What is port 445 and what is it used for?
Port 445 is a traditional Microsoft networking port with tie-ins to the original NetBIOS service found in earlier versions of Windows OSes. Today, port 445 is used by Microsoft Directory Services for Active Directory (AD) and for the Server Message Block (SMB) protocol over TCP/IP.
SMB traffic is important to the functionality of a network not only because it enables resource sharing, including printers and files on the LAN, but also because it is important to the operation of AD. If you're in an office and printing to a printer on another floor, you're probably using SMB.
SMBv1 was introduced in 1984. It has been updated many times, with the most recent version, SMBv3.1.1, being released in 2020. Since resource sharing is one of the main reasons for networking, it's common for companies running Windows to have port 445 open and available on both clients, such as laptops, and servers.
Other ports
SMB is available directly over TCP (port 445) and over NetBIOS over TCP/IP (port 139). Other ports you may see connected with NetBIOS communications are port 137 (nbname) and port 138 (nbdatagram) over User Datagram Protocol. Microsoft Remote Procedure Call (RPC), used for client-server communication, requires an endpoint mapper that is accessible through port 135 or over SMB on port 445.
RPC and SMB exploit examples
For resource sharing and communication to work, ports must be open and accessible. This means they are open for legitimate resource sharing but also become open and always-on targets for attackers.
While RPC and SMB attacks are numerous, the most well-known example is EternalBlue (CVE-2017-0144). This is the vulnerability behind two of the most infamous ransomware attacks: WannaCry and NotPetya. Any system using the Windows SMBv1 protocol is vulnerable. In addition to Windows desktops and servers, some other equipment, such as medical devices, also use the protocol.
EternalBlue has been used both as the initial vector of attack and as a way to perform lateral movement after a network has been infiltrated. The exploit works when attackers send crafted packets to a system running SMBv1. By doing so, they can run code remotely on that system. In the case of WannaCry, attackers exploited the vulnerability by loading malware on the vulnerable target system and then spreading that malware via the same vulnerability to other systems on the network. EternalBlue was also used in the NotPetya attacks and as part of the TrickBot malware Trojan.
In addition to EternalBlue, SMBv1 is vulnerable to DDoS attacks, which can lead to system outages. Race condition issues, such as those in Eternal Champion, where an attacker overwrites the SMB session to execute commands as the privileged user, also plague SMBv1.
How to detect port 445 attacks
Most internet-facing systems get port-scanned every day. A port scan involves a series of messages sent to learn which computer network services a given computer provides. A port scan also identifies which ports and services are open or closed on an internet-connected device. Port scanning does not necessarily indicate an attack, but it is important to monitor for scans to detect any abnormal or suspicious behavior that may be trying to exploit the system. For example, multiple port scanning requests could indicate a brute-force attack attempt.
Monitor ports with tools or services that can detect changes in configuration. Also, stay up to date with the latest vulnerabilities and patches to ensure the most secure software versions are installed.
Many security technologies can detect whether port 445 -- or any port -- has been potentially exploited, including intrusion detection and prevention systems, SIEM systems, firewalls, and threat detection and response tools. Also, use antimalware to detect potential infections.
How to detect SMB vulnerabilities with penetration testing
Performing pen tests is another way security admins can test for SMB vulnerabilities and uncover any issues that must be addressed.
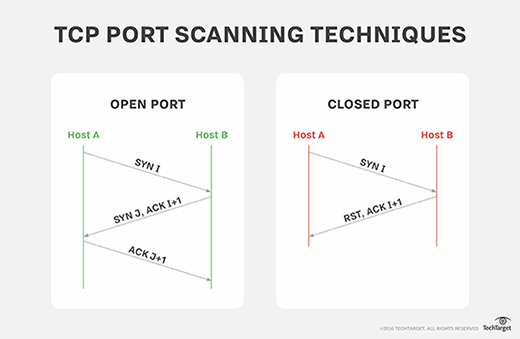
Most pen tests start with a port scan, which can indicate whether port 445 is available and, if it is, whether it's running a vulnerable implementation of SMBv1.
TCP port scanning is performed via network scanner tools, such as the popular and free Nmap scanner, as well as commercial scanners, such as NetScanTools Pro. Network vulnerability scanners, such as Nessus and Qualys, also incorporate TCP port scanning. Regardless of what tools a tester uses, TCP port scanning is an integral step in the vulnerability and pen testing process.
How to defend against port 445 exploits
The best way to improve security is to disable SMBv1 and patch to the latest version of SMB. The vulnerabilities discussed above affect SMBv1; using later, nonvulnerable versions of SMB prevents SMBv1-dependent attacks. Note that Microsoft disabled SMBv1 on Windows 10. Upgrading to the latest version of Windows is also advised.
Another way to prevent SMB exploits is to turn the protocol off and close port 445. This is not a solution for many organizations, however, because it can break network communications and take some Windows services offline. Before disabling or blocking port 445 on Windows systems, perform an in-depth analysis of how it will affect the services and programs running on them.
Actions that can be taken to improve security while still running SMB include the following:
- Block TCP port 445 at the network perimeter only if critical services will not be interrupted.
- Shore up endpoint detection with an integrated product that includes advanced antimalware defense and endpoint detection and response functionality. This helps prevent malicious connections from known bad actors.
- Implement segmentation and isolation wherever possible to prevent lateral movement.
- Enforce strong passwords across the AD domain and for local Windows accounts.
- Maintain a proper inventory of the services and applications running on your systems.
- Enable strong file and share permissions to keep sensitive information locked down.
- Perform proactive system monitoring and alerting, especially for critical Windows systems.
- Create firewall rules that only allow trusted IP addresses to access SMB ports.
- Stay abreast of any and all vulnerabilities, and patch them as soon as possible.








