Best practices to conduct a user access review
User entitlement reviews ensure only authorized users have access to essential systems and data. Uncover the steps of a user access review and helpful best practices.
Controlling and regularly reviewing which employees have access to which systems and data aren't just enterprise security 101 -- they're a compliance necessity. Sarbanes-Oxley Act, PCI DSS, HIPAA and GDPR all have mandatory user access review requirements that could land your company in hot water if not reviewed regularly.
Users with excessive privileges can create more than just compliance challenges, however. They could lead to data loss and data breaches.
To counter these problems, it's critical to conduct user access reviews.
What is a user access review?
Many enterprises use a variety of identity and access management (IAM) mechanisms, such as role-based access control (RBAC) and principle of least privilege (POLP), to define the access permissions that secure their systems. But, once these are in place, then what? These aren't one-and-done activities.
Think about the number of employees who have quit or been terminated at your company in the past year. Then, add in the number of current employees who have changed roles or departments. If you work for a large organization, this number could be in the hundreds or even thousands.
Now, consider the data, applications and systems those employees had or have access to. Terminated employees could still hold the keys to some of the company's most valuable information. Current employees with user privileged account accumulation present just as big a risk.
A user access review is exactly what it sounds like: the process of periodically reviewing the rights of anyone who has access to enterprise systems and data. Users can include employees, partners, third parties, service providers and vendors. User access reviews are critical to achieving a strong security posture and ensuring cyber resilience.
Why are user access reviews important?
Performing user account reviews, also known as account recertification, account attestation or entitlement reviews, is critical to monitor, manage and audit the user account lifecycle from creation to termination -- and everywhere in between.
Including regular user access reviews as part of an enterprise cyber hygiene program can reduce the risk of data loss and data breaches by ensuring users only have access to the data and systems they need to do their job. They can also help mitigate unauthorized access, privilege creep and privilege escalation attacks.
Common user access risks
The wrong access rights can result in malicious attacks or internal mistakes that could be detrimental to the company's brand and its bottom line. Common access risks include the following:
- Privilege creep.
- Privilege escalation attacks.
- Inappropriate or unauthorized access.
- Fraud.
- Access abuse.
- Insider threats, malicious and accidental.
- Account misconfiguration.
- Outdated user access policies.
Users can become overprivileged for a number of reasons -- for example, changing roles in a company and not having their access rights adjusted to their new role, quitting or getting fired yet retaining access rights, M&A and more.
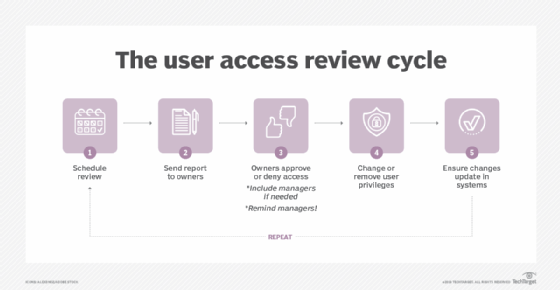
User access review best practices
Take the following steps, and implement the following best practices to ensure a smooth and effective user access review process.
1. Define policy scope
To create a user access review policy, gather the following information:
- An inventory of enterprise assets. This includes anything users can access across the organization. Document all databases, applications, systems, networks, OSes, data centers, rooms, buildings, etc.
- A list of owners for each asset. This could be a manager, administrator or IT team, among others. Owners should provide a detailed list of the types of data and accessible content in their assets, which maps to access levels and roles.
- Descriptions of access levels and roles. Assign job roles and responsibilities and their access requirements at a granular level. For example, some employees need read-only access to data to perform their job functions, while some require editing capabilities and others need permissions to delete data.
This is also a good time to assess and assign risk values to each asset.
2. Set review frequency and types
User access audits can be trigger-based reviews -- one-off updates initiated by predefined rules, such as when an employee changes departments or is terminated -- or scheduled, periodic user access reviews conducted on a regular basis. Reviews can be per system, per employee, per role -- as in RBAC -- or a combination of the three. A per-system review audits access controls based on who has access to each system. A per-employee review examines privileges based on the systems an employee accesses. A role-based review assesses what a predefined role or group can access.
How often to conduct reviews varies by organization. Smaller companies might be able to review the entire policy more frequently than larger corporations, which might only assess one system at a time or test a sample and conduct a full review only when discrepancies occur. Depending on the system, person or role, run reviews monthly, quarterly, biannually or annually. Audit high-risk assets more often, while lower-risk systems can be assessed less frequently.
When defining frequency, consider how to administer the next review. Some businesses work from previous reviews and follow the same processes, but this isn't advisable for all organizations, especially those that have changed a lot in a given time period. For example, a company that has undergone a reorganization, adopted new applications or systems, or been involved in M&A should revisit its review processes and schedules.
3. Create and implement a user access review policy
Establish a clearly written access review policy. Include specifics about the review process, as well as information about who completes the reviews, provisioning and deprovisioning processes, compliance regulations, security controls in place to manage and protect user access, and how reviews are to be communicated to users.
Also, define and document the segregation of duties. This involves splitting tasks and privileges for a specific process among two or more people.
4. Conduct reviews
At review time, generate a user access report that includes a list of databases, applications and systems, as well as who currently has access to them. Include all employees and third parties, such as vendors, service providers and consultants.
Send a copy of the report to each asset owner, who then audits the list to verify who has access and at what level, noting whose access privileges need to be changed or revoked. This is sometimes based on role, department or responsibility, while, other times, it could take a more granular approach because responsibilities and privileges can vary for people in the same role.
In some reviews, owners might approve or reject whole departments. Department managers then must verify or reject whether specific employees from their respective departments need access. If an asset owner rejects a department's access privileges, the owner should notify the department manager who should then have time to negotiate the case for access, if necessary.
Make sure owners sign off on the report by the deadline.
5. Remediate and report
Once reviews are complete, execute changes based on the owners' reports. Remove revoked access, and update employees' privileges as needed. Generate a new user access report to verify changes have gone into effect.
Finalize, print and store the report. Finalized reports should include previous and current roles, access rights, who approved them, the names of the systems' owners and any notes or further actions. This provides an audit trail and evidence of access recertification compliance.
Now is a good time to assess security gaps. For example, if several user IDs are removed due to a specific policy, rethink that policy. The report can also measure how well security policies and IAM strategies work, as well as whether access policies during hiring, transferring or termination are efficient and in line with the security model of the business.
Take time to review the process, too. What went well? Are there steps that could simplify the process next time? What ways could you make user access reviews more efficient?
6. Provision and deprovision
Provisioning, the first step in the user account lifecycle, explains how access privileges are assigned to a new hire. Deprovisioning outlines how to revoke user access rights when an employee changes roles or is terminated. Removing access rights to enterprise assets is part of the deprovisioning and offboarding process but is often overlooked. Regular access reviews notify managers and owners of issues during offboarding, enabling the company to update its processes and remediate any changes.
Verify the removal of former employees' access rights in an audit. If employees maintain access rights, they could be stolen by cybercriminals to use maliciously or used by disgruntled employees who want revenge on the company.
7. Involve employees and managers
An entitlement review is an enterprise-wide project. While a CISO or security admin might own the task, other C-level staff and managers should help define and review access controls.
Remember, an effective team requires effective, easily digestible data. Many business systems classify user IDs and access controls in their own formats. Combining data from multiple systems can be complicated and confusing. Collate and simplify the data for owners. If data is difficult to read, owners might sign off on a report without conducting a thorough analysis.
Communicate the importance of user access reviews during security awareness trainings. This helps managers understand the risks of providing employees with too many privileges. For end users, it can help them understand the access review process and access security risks.
Users and their managers know best what access rights they need to do their jobs. Enlist the help of both to get input on access controls and to solidify the importance of -- and their involvement in -- user access reviews.
8. Perform manual or automated reviews
Account attestation can be manual or automated. Manual access reviews can be time-consuming and cumbersome. Existing or specialized software can automate the process.

For some organizations, directory services are sufficient, such as Active Directory for Windows or Lightweight Directory Access Protocol for Unix. These tools might not offer the granular account recertifications needed by all businesses, however. Many commercial IAM tools offer reporting options for user access reviews. Machine learning algorithms and automation can also help streamline the process.
9. Enforce the principle of least privilege
POLP is an access control concept that dictates users only have access to the applications, data, systems and other resources they need to complete their specific job.
POLP helps ensure high-value data and assets cannot be accessed by anyone and everyone within a company. It also helps prevent compromised accounts from being used in lateral movement attacks in which attackers can infiltrate other parts of the network. Rather, the attacker is restricted to only accessing what that particular user has access to.
10. Consider role-based access control
RBAC is an authentication methodology that sets users' level of access rights based on their role within the organization.
Roles can be broad -- by groups and departments, such as sales, operations and finance -- or granular, such as a finance intern versus a finance manager. Use roles to control access to applications, data and systems. For example, a data entry clerk wouldn't need to access ADP, while an HR manager would.
RBAC creates a standardized access control approach, which can help reduce complexity, simplify onboarding and provisioning, maintain compliance, reduce costs, increase visibility and decrease risk, among other benefits. RBAC also automatically updates users' privileges if they change roles within the company.
Additional best practices
- Deploy multifactor authentication (MFA). MFA boosts secure access by verifying a user's identity using multiple authentication methods. This helps provide stronger security of credentials and assets and prevents account abuse.
- Adopt a strong password policy. Weak passwords are a major credential security issue. Use an enterprise password policy to strengthen users' passwords and, in turn, the security of data and assets.
- Adopt a zero-trust strategy. The zero-trust security model grants users access to systems based on their identities and roles.
- Grant temporary access. Certain users, such as contractors and third parties, only require temporary access to data and systems. Permissions can automatically expire after a particular time period or role change or be manually revoked if necessary.








