Symmetric vs. asymmetric encryption: What's the difference?
Explore the differences between symmetric vs. asymmetric encryption, including how they work and common algorithms, as well as their pros and cons.
Cryptography is the art of encrypting and decrypting data. Encryption is the process of encoding unencrypted data, or plaintext, into encrypted data, or ciphertext, to disguise the data and make it unreadable. Decryption is the method of decoding encrypted data into readable information.
Encryption algorithms, or ciphers, involve the use of a variable -- known as a key -- which makes the data unreadable. Only the person or entity with the proper decryption key is able to read the data.
The two widely used types of ciphers are symmetric and asymmetric.
What is symmetric encryption and how does it work?
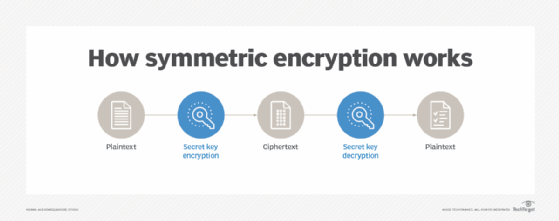
Symmetric encryption, also known as secret key encryption or single-key encryption, converts plaintext into ciphertext and back using a single secret key for both encryption and decryption.
Stream and block are the two types of symmetric algorithms. Stream ciphers encrypt data 1 bit at a time, while block ciphers encrypt data divided into set lengths, or blocks.
This article is part of
What is data security? The ultimate guide
In symmetric encryption, sender Alice encrypts her message with an agreed-upon shared key and sends the encrypted message to Bob. Bob receives the encrypted message and uses the shared key to decrypt the message.
Symmetric encryption algorithms
There are numerous types of symmetric encryption algorithms, including the following:
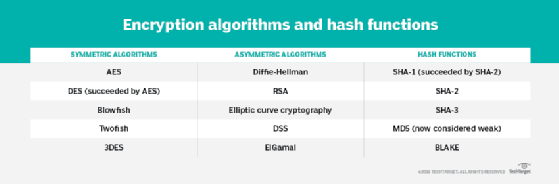
- Data Encryption Standard (DES), published in 1976, was the first modern symmetric encryption algorithm. The block cipher is no longer considered secure.
- Advanced Encryption Standard (AES) is the most widely used algorithm in symmetric key cryptography. AES was named successor to DES by NIST in 2001. AES comprises three block ciphers -- AES-129, AES-192 and AES-256 -- each of which is deemed sufficient to protect government-classified information up to the Secret level, with Top Secret information requiring either 192- or 256-bit key lengths.
- Triple DES (3DES), also known as Triple Data Encryption Algorithm, or TDEA), is a block cipher that uses three 56-bit keys for a total of 168-bit strength. It is more secure than DES but not as strong as AES. NIST deprecated its use in new applications in 2017 and called for the full deprecation of 3DES through 2023, after which its use will become disallowed.
- International Data Encryption Algorithm (IDEA) has a typical block size of 64 bits. IDEA is used in Pretty Good Privacy and its successor, OpenPGP.
- Blowfish is a 64-bit block cipher. Its small block size makes it vulnerable to attacks.
- Twofish is the successor of Blowfish. It has a block size of 128 bits.
- Skipjack is a 64-bit block cipher developed by the National Security Agency. As of 2016, it is no longer certified to encrypt government data.
- Rivest Cipher 4 (RC4) is a stream cipher. Attacks in the 2000s and 2010s revealed weaknesses in the RC4 algorithm, and its use in TLS was prohibited by the Internet Engineering Task Force in February 2015.
Uses of symmetric encryption include payment applications, validations and pseudo-random number generation or hashing.
Pros and cons of symmetric encryption
Here are the pros of symmetric encryption:
- It is relatively fast and easy to set up.
- It is secure.
Cons of symmetric encryption include the following:
- It requires a mechanism for sharing a secret key securely across an open network (internet).
- If the secret key used by both parties is compromised, both sides of the transaction are at risk and can be decrypted.
What is asymmetric encryption and how does it work?
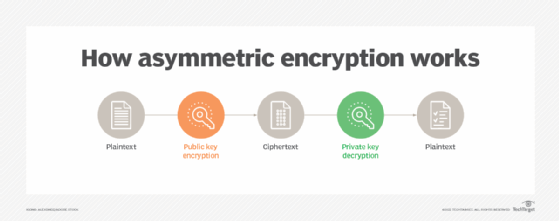
Asymmetric encryption, also known as public key encryption, converts plaintext to ciphertext using two interdependent keys: one to encrypt the data, a public key, and another to decrypt data encrypted with the public key, called a private key. Public keys can be used by anyone to encrypt the data. The private key, or secret key, is known only to the entity decrypting the message.
In asymmetric encryption, sender Alice encrypts her message with a public key and sends the encrypted message to Bob. Bob receives the encrypted message and uses his private key to decrypt it.
Using two different keys provides a number of different features, the most important probably being digital signatures. Among other things, digital signatures are used to guarantee a message was created by a particular entity. Digital signatures also authenticate remote systems or users.
Asymmetric encryption algorithms
Some of the most common asymmetric encryption algorithms are the following:
- The Diffie-Hellman (DH) key exchange is one of the most common algorithms. It enables two parties to exchange cryptographic keys in a secure manner, regardless of whether the communication channel is public or private.
- Rivest-Shamir-Adleman (RSA) is another widely used asymmetric encryption algorithm. Based off DH, RSA is often used in e-commerce protocols and is believed to be secure given sufficiently long keys and the use of up-to-date implementations.
- Elliptic curve cryptography (ECC) is another type of asymmetric encryption. Based on elliptic curve theory, ECC uses algebraic functions to generate security between key pairs.
Asymmetric cryptography is used in key exchange, email and web security, and cryptocurrencies, such as bitcoin.
Pros and cons of asymmetric encryption
The pros of asymmetric encryption include the following:
- Keys are never distributed or exchanged.
- Because private keys aren't transmitted or revealed, security is increased.
- Digital signatures enable sender authentication.
- It enables nonrepudiation.
The cons of asymmetric encryption include the following:
- It is slower than symmetric encryption.
- If an entity loses its key, messages can't be decrypted.
- Public key ownership isn't authenticated. Users must verify that their public keys belong to them.
- If a private key is stolen, an attacker could use it to decrypt their messages.
Asymmetric cryptography is subject to brute-force and man-in-the-middle attacks. Plus, if hackers know either user's key, they can use it to decrypt the data.
Cryptographic hashing
A cryptographic hash function has a somewhat different role compared to other cryptographic algorithms. It is used to return a value based on a piece of data, such as a file or a message, for example. Any accidental or intentional change to the data changes this hash value.
A good hash algorithm should make it impossible to either create an initial input that produces a specific hash value or for the original input to be calculated from the hash value. Message-Digest 5, or MD5, and Secure Hash Algorithm 1 (SHA-1) were widely used hash algorithms that are now considered weak. They were deprecated in 2014 and were replaced by SHA-224, SHA-256, SHA-384 and SHA-512, collectively referred to as SHA-2. SHA-3 was released in 2015. It is composed of SHA-3-224, SHA-3-256, SHA-3-384 and SHA-3-512, as well as two extendable output functions, SHAKE128 and SHAKE256. SHA-3 was labeled a backup standard rather than a replacement for SHA-2.
Symmetric vs. asymmetric: Which is better?
When choosing an encryption algorithm, it's important to consider the type of data being encrypted. High-risk or sensitive data, such as confidential customer information, needs stronger encryption than marketing plans, for example.
Performance is another key factor. Asymmetric encryption is generally slower than symmetric encryption due to the creation of two keys instead of one. The tradeoff with symmetric encryption's use of the same key, however, is multiple chances for that key being exposed. Asymmetric encryption's distributed keys mean the keys are never distributed and, therefore, are more secure.
As noted, symmetric and asymmetric encryption algorithms have different vulnerabilities. It is important to understand the application to match the most appropriate algorithm with the particular use case.
In many scenarios, such as SSL/TLS, both asymmetric and asymmetric algorithms are used to boost security. Because asymmetric encryption is much slower than symmetric encryption, data is typically encrypted with a symmetric algorithm, and then the comparatively short symmetric key is encrypted using asymmetric encryption. This enables the key needed to decrypt the data to be securely sent to other parties along with the symmetrically encrypted data. In another example, Secure/Multipurpose Internet Mail Extensions, or S/MIME, uses an asymmetric algorithm for nonrepudiation and a symmetric algorithm for efficient privacy and data protection.
The landscape of cryptography is constantly changing. To stay abreast of the latest developments, follow the news and recommendations from standards bodies such as NIST.






