The 7 core pillars of a zero-trust architecture
Learn how Forrester's seven pillars of zero trust model can help IT leaders identify, organize and implement the appropriate cybersecurity tools for a zero-trust framework.
The zero-trust framework is gaining traction in the enterprise due to its security benefits. Organizations are increasingly adopting a zero-trust model in their security programs, replacing the traditional perimeter-based security model.
The perimeter-based model considers users, devices and resources residing directly on the corporate LAN and WAN as more trustworthy than those from outside the network. The challenge presented by insider threats and the explosion of IoT and edge devices required major changes to the security architectures and tools implemented on enterprise networks. This is where the seven zero-trust pillars come into play because, in a zero-trust model, everything is considered untrusted, regardless of where the user or resource resides.
But making the switch to a zero-trust model requires logistical considerations and planning. To help with the migration from a perimeter-based security architecture to a zero-trust framework, many organizations have referred to the Forrester Zero Trust eXtended (ZTX) model to help. ZTX has become a go-to reference on how to best purchase and implement the right tools, policies and methodologies.
7 pillars of the zero-trust model
The Forrester zero-trust framework breaks down seven necessary pillars to properly deploy zero-trust security across all technologies and corporate cultures. Here's an introduction to the seven ZTX pillars:
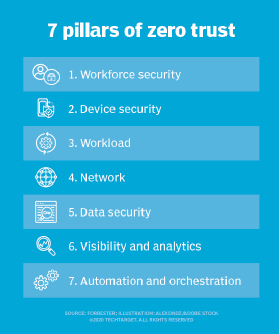
1. Workforce security
The workforce security pillar centers around the use of security tools such as authentication and access control policies. These tools identify and validate the user attempting to connect to the network before applying access policies that limit access to decrease the attack surface area.
2. Device security
Much like workforce security, the primary goal of the device security pillar is identification and authorization when devices attempt to connect to enterprise resources. The devices may be user-controlled or completely autonomous, as in the case of IoT devices.
3. Workload security
The workload security pillar refers to the applications, digital processes, and public and private IT resources used by an organization for operational purposes. Security is wrapped around each workload to prevent data collection, unauthorized access or tampering with sensitive apps and services.
4. Network security
The network security zero-trust pillar is used to help microsegment and isolate sensitive resources from being accessed by unauthorized people or things.
5. Data security
This zero-trust pillar revolves around the categorization of corporate data. Once categorized, the data can be isolated from everyone except those that need access. This pillar also includes the process of determining where data should be stored, as well as the use of encryption mechanisms while data is in transit and at rest.
6. Visibility and analytics
All security processes that revolve around access control, segmentation, encryption, and application or data organization must be closely monitored. The visibility and analytics pillar may prescribe the use of AI to automate some processes, including anomaly detection, configuration control and end-to-end data visibility.
7. Automation and orchestration.
The final pillar of the zero-trust framework covers modern ways in which organizations can automate and centrally control the entire zero-trust model on the LAN, WAN, wireless WAN, and public or private data centers.
Security leaders can implement these seven pillars of the ZTX model to apply the appropriate security tools and better secure IT. The ZTX playbook or similar zero-trust pillars are designed to help IT security administrators identify, organize and implement the appropriate security tools that satisfy the overall goal of a zero-trust strategy.








