network operating system (NOS)
What is a network operating system (NOS)?
A network operating system (NOS) is a computer operating system (OS) that's designed primarily to support workstations, PCs and, in some instances, older terminals that are connected on a local area network (LAN). The software behind a NOS enables multiple devices within a network to communicate and share resources with each other. However, a typical NOS no longer exists, as most OSes have built-in network stacks that support a client-server model.
A NOS coordinates the activities of multiple computers across a network. This can include such devices as PCs, printers, file servers and databases connected to a local network. The role of the NOS is to provide basic network services and features that support multiple input requests simultaneously in a multiuser environment.
Types of network operating systems
There are two basic types of network operating systems:
- Peer-to-peer (P2P) network OSes let users share network resources saved in a common, accessible location. In this architecture, all devices are treated equally in terms of functionality. P2P usually works best for small and medium LANs and is less expensive to set up compared to the client-server model.
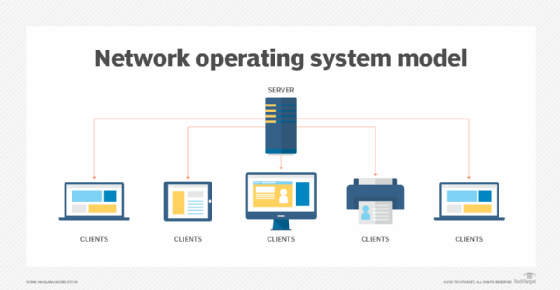
- Client-server network OSes provide users with access to resources through a server. In this architecture, all functions and applications are unified under one file server that can be used to execute individual client actions, regardless of physical location. Client-server tends to be more expensive than P2P to set up and requires significant technical maintenance. An advantage of the client-server model is that the network is controlled centrally, which makes changes or additions to technology easier to incorporate.
Common features of network operating systems
Features of network operating systems are typically associated with user administration, system maintenance and resource management functionality. These include the following:
- Basic support for OSes, including protocol and processor support, hardware detection and multiprocessing.
- Printer and application sharing.
- Common file system and database sharing.
- Network security capabilities, such as user authentication and access control.
- Directory services.
- Backup and web services.
- Internetworking.
Examples of network operating systems
True network OSes are categorized as software that enhances the functionality of operating systems by providing added network features.
The following are examples of current network OSes and their providers:
- Microsoft Windows Server. This is the most widely used NOS designed by Microsoft. Windows servers are known for their powerful functionalities, availability, stability and high security, which is designed for enterprise-level management, data storage, networking and application hosting. Windows Server 2003 was the initial version of Windows Server. Since then, eight more versions have been released. Windows Server 2022, which was released in August 2021, is the latest version.
- Unix OS. The Unix OS was first developed by AT&T Corporation's Bell Laboratories in the late 1960s. It's a portable, stable, multiuser and multitasking system that's typically used for web servers, desktop computers and laptops. The Unix OS operates on three main parts: the kernel, the shell and programs. Many different types of Unix are in use today, including Oracle Solaris, FreeBSD and IBM Advanced Interactive eXecutive.
- Cisco Internetwork OS (IOS). Cisco IOS is a family of proprietary network OSes that both service providers and enterprises use. IOS is included on several router and network switch models that Cisco Systems manufactures. It provides a full package of routing, switching, internetworking and telecommunications functions integrated into a multitasking OS.
- Junos OS. Also known as Juniper Junos, Junos OS is a FreeBSD-based NOS that powers every networking device developed by Juniper, such as networking switches and firewalls. Junos OS is designed to provide increased network availability, flexibility and operational efficiency.
In addition, some multipurpose OSes, such as OpenVMS, come with capabilities that enable them to be described as network operating systems. OpenVMS is a server OS that runs on multiple chip architectures. It offers multisite cluster configurability and is designed to support mission-critical environments. In addition, the most popular OSes -- Windows, Unix, Linux and Mac -- include built-in networking functions that might not require additional network services.
Discontinued network operating systems include the following:
- Artisoft LANtastic. This P2P network OS supported most PC operating systems. The most current version, LANtastic 8.01, was released in 2006 and connected PCs running MS-DOS 5.0 or later and Windows 3.x to Windows 7.
- Banyan Vines. This discontinued network OS used a client-server architecture to request specific functions and services.
- Novell NetWare. Discontinued in 2009, this was the first network OS to be released and was designed based on the Xerox Network Systems protocol architecture.
- Microsoft LAN Manager. Microsoft LAN Manager operated as a server application and was developed to run under the Microsoft OS. Now, most of the functionality of LAN Manager is included in the Windows OS itself. It was discontinued in 1994.
Computer networks can be composed of a small handful of devices, or they can be millions of devices spread across the world. Learn about the most common types of networks and their use cases.







