SSL VPN (Secure Sockets Layer virtual private network)
What is an SSL VPN (Secure Sockets Layer virtual private network)?
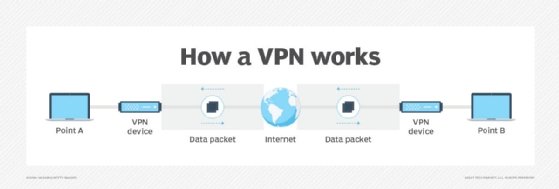
An SSL VPN is a type of virtual private network (VPN) that uses the Secure Sockets Layer (SSL) protocol -- or, more often, its successor, the Transport Layer Security (TLS) protocol -- in standard web browsers to provide secure, remote access VPN capability.
SSL VPNs enable devices with an internet connection to establish a secure remote access VPN connection with a web browser. An SSL VPN connection uses end-to-end encryption (E2EE) to protect data transmitted between the endpoint device client software and the SSL VPN server through which the client connects securely to the internet.
Enterprises use SSL VPNs to enable remote users to securely access organizational resources, as well as to secure the internet sessions of users who are accessing the internet from outside the enterprise.
SSL VPNs are important because they provide an E2EE mechanism for client internet sessions and because they can be easily implemented without the need for specialized client software other than a modern web browser. By providing a higher level of compatibility with client platforms and configurations for remote networks and firewalls, SSL VPNs provide more reliable connections.
Because the SSL protocol itself has been deprecated by the Internet Engineering Task Force (IETF) and replaced by TLS, SSL VPNs running on modern browsers now use TLS to encrypt and authenticate data transmitted across the VPN.
SSL VPNs enable users to access restricted network resources remotely via a secure and authenticated pathway by encrypting all network traffic and making it look as if the user is on the local network, regardless of geographic location.
The primary reason to use an SSL VPN product is to prevent unauthorized parties from eavesdropping on network communications and extracting or modifying sensitive data. SSL VPN systems offer secure and flexible options for enterprise employees, telecommuters and contractors to remotely connect to private enterprise networks.
To implement an SSL VPN, organizations can purchase a stand-alone appliance that functions solely as an SSL VPN server; a bundled device, such as a next-generation firewall or unified threat management product that offers SSL VPN capability; or as a service, using a virtual SSL VPN appliance.
How SSL VPNs work
SSL VPNs rely on the TLS protocol, which has replaced the older SSL protocol, to secure remote access. SSL VPNs enable authenticated users to establish secure connections to internal HTTP and HTTPS services via standard web browsers or client applications that enable direct access to networks.
There are two primary types of SSL VPNs: VPN portal and VPN tunnel. An SSL portal VPN enables one SSL VPN connection at a time to remote websites. Remote users access the SSL VPN gateway with their web browser after they have been authenticated through a method supported by the gateway. Access is gained via a webpage that acts as a portal to other services.
An SSL tunnel VPN enables users to securely access multiple network services via standard web browsers, as well as other protocols and applications that are not web-based. The VPN tunnel is a circuit established between the remote user and the VPN server; the server can connect to one or more remote websites, network services or resources at a time on behalf of the client. The SSL tunnel VPN requires the web browser to handle active content and provide functionality that is not otherwise accessible through an SSL portal VPN.
Advantages of SSL VPNs
One of the primary advantages of an SSL VPN is that it uses the TLS technology implemented in modern web browsers, so there is no need to install specific client software. That makes it easy to deploy. In addition, the encrypted circuits created using TLS provide much more sophisticated outbound connection security than traditional VPN protocols.
Another benefit is that SSL VPNs require less administrative overhead and technical support than traditional VPN clients due to their ease of use and reliance on widely used web clients. SSL VPNs enable users to choose any web browser, regardless of the operating systems (OSes) their devices are running.
In addition, users do not need to download any additional software or configuration files or go through complex steps to create an SSL VPN. Unlike other tunneling security protocols, such as Layer 2 Tunneling Protocol (L2TP) or IP security (IPsec), SSL VPNs only require an updated browser to establish a secure network.
L2TP operates at the data link layer -- Layer 2 -- of the Open Systems Interconnection (OSI) networking model, while IPsec operates at the OSI network layer -- Layer 3. This means that more networking metadata can be encrypted when using those tunneling methods, but it also requires additional software and configuration to create VPNs with those protocols.
SSL VPNs operate at the transport layer, so network traffic can be more easily split into securely tunneled circuits for accessing protected resources, or applications and untunneled circuits for accessing public resources or applications.
SSL VPN servers can also be configured to enable more precise access control because they build tunnels to specific applications rather than to an entire enterprise network. That means users on SSL VPN connections can be restricted to only those applications for which they have been granted, not the whole network.
Security risks of SSL VPNs
Despite the benefits an SSL VPN provides, security risks are also associated with the technology. Notwithstanding its enhanced security measures, an SSL network can be susceptible to spreading malware, including spyware, worms, viruses and Trojan horse programs.
Because users can access an SSL VPN server remotely, a remote user's device that's not running updated antivirus software can spread malware from a local network to an organization's network.
Hackers can also exploit the split tunneling feature of an SSL VPN, which enables users to transmit secured traffic over an SSL VPN tunnel while using untunneled channels to communicate over unsecured channels. Split tunneling enables a user with remote access to share network traffic with both private and public networks at the same time, which can give an attacker the ability to execute an assault using the unsecured channel as an intermediary in the attack.
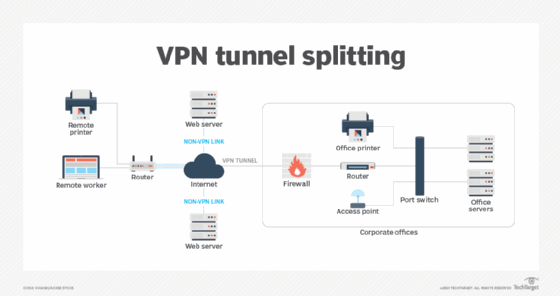
Additionally, if a remote computer has an established SSL VPN network connection to a company's internal network and a user leaves a session open, that internal corporate network will be exposed to anyone who has access to that system.
Another potential danger occurs when users attempt to set up an SSL VPN connection using a publicly accessible computer, such as those at kiosks. In those cases, the user may be vulnerable to attacks involving keyloggers installed on an untrusted system that is unlikely to meet enterprise security policies and standards. If keystroke loggers are present, attackers may be able to intercept user credentials and other confidential information.
IPsec VPN vs. SSL VPN
Using an SSL VPN can have advantages over using an IPsec VPN. First, IPsec remote access VPN connections require installation of IPsec client software on client systems, which may, in turn, require the purchase and configuration of additional software. SSL VPNs can be set up using existing browsers and minimal configuration modification.
Another advantage of SSL VPN over IPsec VPN lies in its ease of use. While different IPsec VPN vendors may have different implementation and configuration requirements, SSL VPNs can be deployed with virtually any modern web browser.
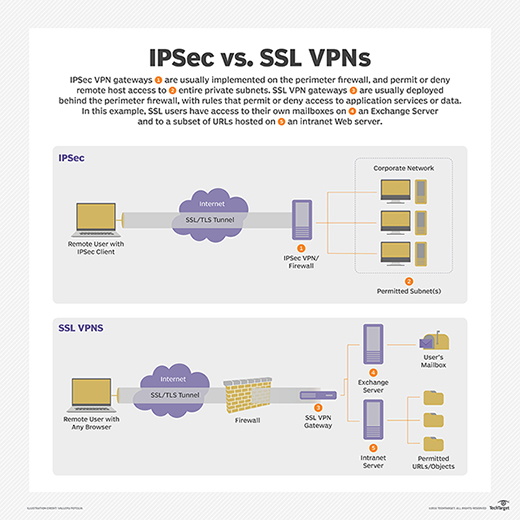
Also, once the user is authenticated to an IPsec VPN, the client computer has full access to the entire private network, which violates the principle of least privilege (POLP) and, as a result, may expose some private resources to attack.
Using an SSL VPN, on the other hand, can enable more precise access control by enabling creation of tunnels to specific applications using sockets rather than to the entire network. This enables organizations to provide different access rights for different users.







