COBIT
What is COBIT (Control Objectives for Information and Related Technologies)?
COBIT is an IT governance framework for businesses wanting to implement, monitor and improve IT management best practices. COBIT is the acronym for Control Objectives for Information and Related Technologies.
The COBIT framework was created by ISACA to bridge the crucial gap between technical issues, business risks and control requirements.
COBIT can be implemented in any organization from any industry to ensure quality, control and reliability of information systems.
In the United States, COBIT is the most commonly used framework for achieving compliance with the Sarbanes-Oxley Act (SOX).

What is ISACA?
ISACA sets and develops guidance and controls for information governance, control, security and audit professionals.
The global organization sponsors and drives the COBIT framework. ISACA originally stood for "Information Systems Audit and Control Association," but the organization now simply goes by ISACA.
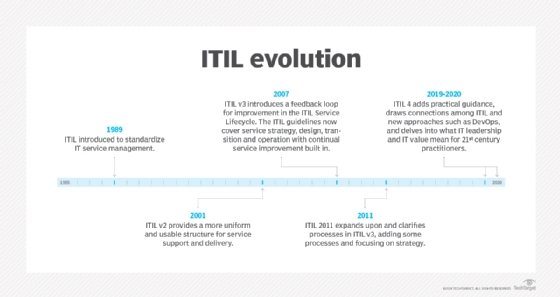
What is the history of COBIT?
The original version of COBIT was published in 1996 for financial auditors to better navigate the growth of IT environments.
ISACA released a more comprehensive version in 1998 that covered areas beyond audit controls. Versions 3 and 4, released in the 2000s, included further management guidelines around cybersecurity.
Released in 2013, COBIT 5 focused on providing tools, best practices and objectives that were universally applicable to all enterprise IT operations.
COBIT 5 expanded on COBIT 4 by integrating related standards from the International Organization for Standardization (ISO), including IT Infrastructure Library (ITIL).
In 2019, ISACA announced the current COBIT version: COBIT 2019. This current version is a more generic, comprehensive and flexible tool that can be used by all enterprises regardless of their size or immediate goals.
It also better addresses rapidly changing technology and is designed to evolve with more frequent updates.
Why is COBIT important?
The goal of the COBIT framework is to provide a common language for IT professionals, business executives and compliance auditors to communicate with each other about IT controls, goals, objectives and outcomes.
Without a common language, an enterprise under audit runs the risk of having to educate individual auditors about when, where, how and why specific IT controls were created.
What are the COBIT framework basics?
COBIT incorporates more than just technical standards for IT managers. The framework supports business requirements through the combined application of IT, related sources and processes. Two main parameters provided are:
- Control. Includes IT management procedures, practices, policies and structures designed to provide an acceptable level of assurance that business goals will be met.
- IT control objective. Defines the level of acceptable results to be attained by implementing control procedures concerning a particular IT operation.
What are the principles of COBIT?
COBIT is based on five key principles for IT enterprise governance:
- Principle 1: Meeting Stakeholder Needs
- Principle 2: Covering the Enterprise End-to-End
- Principle 3: Applying a Single Integrated Framework
- Principle 4: Enabling a Holistic Approach
- Principle 5: Separating Governance from Management
The framework also identifies seven aspects of governance that need to align in order to support the five principles above:
- Principles, Policies and Frameworks
- Processes
- Organizational Structures
- Culture, Ethics and Behavior
- Information
- Services, Infrastructure and Applications
- People, Skills and Competencies
What do you need to know before using COBIT?
COBIT 2019 is not a cheat sheet but a generic tool to support business decisions.
- Objectives. COBIT 2019 contains over 40 business management and governance objectives. IT managers can prioritize or ignore these objectives based on the needs of different stakeholders.
- Domains. COBIT objectives are grouped into specific domains. The domains map to different business processes like planning, building and monitoring.
- Goals cascade. This defines the connection between needs and business goals.
- Components. Components or enablers are generic elements like skills, infrastructure, process descriptions and structures that influence IT.
- Design factors. These include contextual, strategic and tactical factors that help define the needs of an organization and how they must be addressed in a framework. These factors drive implementation choices regarding technology (such as cloud data), methods (such as DevOps, ITIL 4 or Agile) and outsourcing
What is the difference between COBIT 5 and COBIT 2019?
All previous versions of COBIT faced a variety of criticism. They were thought to facilitate limited opportunities -- and sometimes even adverse results.
A major IT firm found that COBIT practices can lead to a "hot potato" situation wherein all stakeholders had passed on the tasks down the line.
Critics maintained that COBIT 5.0 encouraged paperwork and rote rules rather than merely promoting IT governance engagements and improving accountability.
Major changes between COBIT 5 and the latest version COBIT 2019 update include the following:
- an updated alignment with global standards, frameworks and best practices;
- a mechanism that enables the COBIT community to provide feedback, share applications and propose enhancements to the framework; and
- new guidance and tools for tailoring an IT governance system to meet specific IT goals and support better decision-making.
How does COBIT compare with other governance frameworks?
In this section, we'll examine how COBIT compares to other related frameworks.
COBIT vs. ITIL
COBIT and ITIL are both regarded as important analytical tools for governing IT services. The two frameworks, which overlap somewhat, can be used together quite effectively.
While the ITIL framework has a narrow focus on IT service management (ITSM), the COBIT framework has a broader, risk management focus that can be applied to almost any area of the business.
When an enterprise needs to document compliance, ITIL requires the use of third-party tools, such as the Tudor IT Process Assessment (TIPA). In contrast, COBIT audits are always conducted by ISACA Certified Information Systems Auditors (CISAs).
COBIT vs. TOGAF
The Open Group Architecture Framework (TOGAF) is another governance, risk and compliance (GRC) framework that complements COBIT. The Open Group, an independent industry association, created and maintains TOGAF.
It builds on an earlier framework known as TAFIM, or Technical Architecture Framework for Information Management, originally devised by the U.S. Defense Department (DOD). In early 2009, The Open Group released TOGAF version 9.
The Open Group and others commonly lead TOGAF certification and educational programs today. Typically, enterprise architects lead the use of TOGAF within organizations.
How to obtain COBIT certifications
ISACA offers COBIT certifications for information security, cloud computing and other IT professionals. They include COBIT Foundation, COBIT Design and Implementation and COBIT 5 certificates.







