DNS over HTTPS (DoH)
What is DNS over HTTPS?
DNS over HTTPS (DoH) is a protocol that encrypts DNS traffic by passing DNS queries through an HTTPS encrypted session. DoH can help improve online security and privacy and protect DNS queries from attacks.
Introduced in 2018, DoH works similarly to DNS but uses HTTPS sessions to keep the requests secure and minimize the visibility of the information exchanged during queries.
Leading web browsers, including Mozilla Firefox, Microsoft Edge and Google Chrome, use DoH to increase data privacy and security for users.
How does DoH work?
Understanding how DoH means first understanding how regular DNS works. Websites are hosted on web servers, and every web server -- or site on a server -- has an associated IP address. For a browser to access a website, it must first determine the site's IP address, which is where DNS is important. A DNS server's job is to convert a hostname, such as "https://www.techtarget.com/whatis," into an IP address.
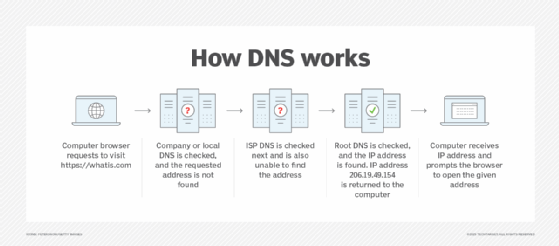
When users enter a hostname into their browser, the request is sent to a recursive resolver, which then passes the request to a root name server -- if the resolver does not already know how to resolve the query. A root name server handles top-level domains (TLDs), such as .com, .org and .edu. The root server then sends the address of the appropriate top-level DNS server back to the resolver. If, for example, a user is trying to access a .com site, the root DNS would provide the address associated with the .com TLD server.
At this point, the resolver sends its request to the TLD server, and the TLD server responds with the IP address of the DNS server that handles the requested domain. The resolver then sends the request to this DNS server, which returns the IP address of the website the user is trying to access. The browser can then issue an HTTP or HTTPS request to that IP address to access the website the user requested. In some cases, caching makes this process be faster.
DoH works in essentially the same way, but there are two key differences. The first -- and most obvious -- difference is that DNS requests are encapsulated within an HTTPS session rather than the browser making an HTTP request. Like HTTPS web traffic, these requests are sent over port 443. For DoH to work, both the browser and the DNS server must support DoH.
The other key difference between standard DNS and DoH is that DoH aims to minimize the information transmitted during the various DNS queries. It does this by transmitting only the portion of the domain name necessary to complete the current step in the name resolution process rather than sending the full domain name the user's browser is trying to resolve. For example, the DNS root does not need to know that the user's browser is trying to resolve "https://www.techtarget.com/whatis." It only needs to know the browser is trying to resolve a .com address.
What are the benefits of DoH?
The primary benefit of using DoH is that encrypting DNS name resolution traffic hides online activities. When users enter a URL into their browser, a DNS query is typically needed to resolve the domain portion of the URL into an IP address. While it may be tempting to think of this name resolution request as being sent directly to a DNS server, the reality is that unless a DNS server exists on the local network, the name resolution request has to pass through the internet service provider's network and through any routers that exist between the ISP and the DNS server. The name resolution request is visible at any of these hops.
This means, for instance, that an ISP can see exactly which sites are being visited, simply by monitoring DNS name resolution requests. DoH hides the name resolution requests from the ISP and from anyone listening or eavesdropping on intermediary networks.
DoH also helps prevent DNS spoofing and man-in-the-middle attacks. Because the session between the browser and the DNS server is encrypted, no one can alter the resolution request results to point the user's browser toward a fraudulent website.
What are the criticisms and controversies of DoH?
DoH has drawn sharp criticism. Vocal opponents of DoH, such as Comcast, have shared concerns that it would concentrate most DNS data with Google due to infrastructure centralization, giving it control of internet traffic routing and access to large amounts of consumer and competitor data.
DoH can also be problematic in the enterprise. Enterprises sometimes monitor DNS requests to block access to malicious or inappropriate sites. DNS monitoring can also sometimes be used to detect malware attempting to "phone home." Because DoH encrypts name resolution requests, it creates a security monitoring blind spot.








