NIST Cybersecurity Framework
What is the NIST Cybersecurity Framework?
The NIST Cybersecurity Framework (CSF) provides guidance on how to manage and reduce IT infrastructure security risk. The CSF is made up of standards, guidelines and practices that can be used to prevent, detect and respond to cyberattacks.
NIST created the CSF to help private sector organizations in the United States develop a roadmap for critical infrastructure cybersecurity. It has been translated into multiple languages and is used by the governments of Japan, Israel and others.
The NIST CSF is most beneficial for small or less-regulated entities -- specifically those trying to increase security awareness. The framework might be less informative for larger organizations that already have a focused IT security program.
The framework was created as a voluntary measure through a collaboration between private industry and government. NIST designed the framework to be flexible and cost-efficient, with elements that can be prioritized. The CSF is available as a spreadsheet or PDF and as a reference tool.
NIST CSF objectives
The NIST CSF aims to ensure critical IT infrastructure is secure. It is intended to provide guidance but is not compliance focused. Its goal is to encourage organizations to prioritize cybersecurity risks -- similar to financial, industrial/personnel safety and operational risks.
Another objective of the framework is to help include cybersecurity risk considerations in day-to-day discussions at organizations.
NIST's Cybersecurity Framework uses
The CSF is designed to help organizations protect infrastructure they deems critical. It can help increase security in the following ways:
- To determine current levels of implemented cybersecurity measures by creating a profile.
- To identify new potential cybersecurity standards and policies.
- To communicate new requirements.
- To create a new cybersecurity program and requirements.
NIST compliance
The framework is both voluntary and performance based, meaning organizations are not required to follow it. Originally, the CSF was designed as a guideline by executive order by former President Barack H. Obama. The standards continued to be implemented by government offices under former President Donald J. Trump and are still implemented by government offices under President Joe Biden.
While designed primarily for government and private sector organizations, public companies can also use the NIST Cybersecurity Framework. The U.S. government and NIST provide several tools to help organizations get started with cybersecurity programs and assessments. Version 1.1 of the framework added a section titled "Self-Assessing Cybersecurity Risk with the Framework" for organizations to follow.
NIST does not use the term comply when it comes to the CSF. If an organization chooses to follow the framework, NIST uses the term leverage -- as in an organization will leverage the NIST Cybersecurity Framework.
History of NIST CSF
In February 2013, President Obama, issued Executive Order 13636: Improving Critical Infrastructure Cybersecurity, which called for the development of a voluntary cybersecurity framework that would provide a prioritized, flexible and performance-based approach to aid organizations in managing cybersecurity risks for critical infrastructure services. While multiple federal agencies were tasked with developing elements related to this executive order, NIST was assigned to develop a cybersecurity framework with input from private industry. The final version of NIST's document was released in 2014.
The document was later translated into different languages, including Spanish, Japanese, Portuguese and Arabic, to be used by a variety of governments.
In 2017, draft version 1.1 of the document was circulated and later made publicly available in April 2018.
3 parts of NIST's framework
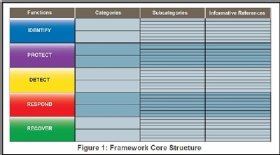
The CSF is broken down into three parts: the core, implementation tiers and profiles.
- The framework core, as described by NIST, is the set of cybersecurity activities and desired outcomes common across any critical infrastructure sector.
- The framework implementation tiers provide context around an organization's cybersecurity risks and processes to put in place to manage risks. The tiers describe the level at which an organization's cybersecurity risk management practices follow the characteristics defined in the CSF. A tier 1 organization, for example, is one that's ranked as partial, described as having limited awareness. Tier 2 is risk-informed, tier 3 is repeatable and tier 4 is adaptive, meaning the organization can best react to cybersecurity threats.
- The framework profiles describe the current state of an organization's security program, as well as compare the current state to the desired state. This process helps reveal any gaps, which can be later addressed. The goal of a profile is to aid organizations in establishing a roadmap for reducing cybersecurity risk.
The CSF is made up of the following five core functions:
- Identify refers to developing an understanding of how to manage cybersecurity risks to systems, assets, data or other sources.
- Protect refers to the safeguards put in place to ensure the delivery of critical infrastructure services.
- Detect defines how a cybersecurity event is identified.
- Respond defines what actions are taken when a cybersecurity event is detected.
- Recover identifies what services should focus on resilience and outlines restore capabilities of impaired services.
The goal of these functions is to provide a strategic view of the cybersecurity risks in an organization.





