
WannaCry ransomware
What is WannaCry ransomware?
WannaCry ransomware is a cyber attack that spreads by exploiting vulnerabilities in the Windows operating system. At its peak in May 2017, WannaCry became a global threat. Cybercriminals used the ransomware to hold an organization's data hostage and extort money in the form of cryptocurrency.
WannaCry spreads using EternalBlue, an exploit leaked from the National Security Agency (NSA). EternalBlue enables attackers to use a zero-day vulnerability to gain access to a system. It targets Windows computers that use a legacy version of the Server Message Block (SMB) protocol.
WannaCry is one of the first examples of a worldwide ransomware attack. It began with a cyber attack on May 12, 2017, affecting hundreds of thousands of computers in as many as 150 countries.
WannaCry ransomware is particularly dangerous because it propagates through a worm. This means it can spread automatically without victim participation, which is necessary with ransomware variants that spread through phishing or other social engineering methods.
This article is part of
What is ransomware? How it works and how to remove it
What is known about WannaCry?
The EternalBlue exploit, initially developed by the NSA, was stolen and leaked about a month before the WannaCry attack by a hacker group called The Shadow Brokers.
The Shadow Brokers group surfaced in 2016 when it began releasing exploit code from the NSA. The Shadow Brokers released EternalBlue to the public in April 2017, claiming it stole EternalBlue and other exploits and cyber weapons from the NSA-linked Equation Group.
Although Microsoft had issued a patch for the vulnerability in March 2017 -- a month before it was disclosed by The Shadow Brokers -- many organizations failed to update their Windows systems, exposing them to the WannaCry cryptoworm.
EternalBlue uses a vulnerability found only in SMB version 1, which was superseded in 2013. Any Windows system that accepts SMBv1 requests is at risk for the exploit. Only systems that have later versions of SMB enabled or that block SMBv1 packets from public networks resist infection by WannaCry.
After WannaCry began to spread across computer networks in May 2017, some experts suggested the worm carrying the ransomware might have been released prematurely due to the lack of a functional system for decrypting victim systems after paying the ransom.
Security researchers tentatively linked the WannaCry ransomware worm to the Lazarus Group, a nation-state advanced persistent threat group with ties to the North Korean government. In December 2017, the White House officially attributed the WannaCry attacks to North Korea.
Due to early reports indicating the threat actors behind the ransomware weren't providing decryption keys to victims who paid the ransom, many of those attacked chose not to pay. A day after the attack surfaced, security researcher Marcus Hutchins, then better known as MalwareTech, discovered a kill switch that stopped WannaCry from spreading.
How does WannaCry work?
WannaCry encrypts files on the hard drives of Windows devices so users can't access them. In May 2017, the cryptoworm demanded a ransom payment of between $300 to $600 in bitcoin within three days to decrypt the files. However, even after paying, only a handful of victims received decryption keys.
WannaCry exploits a vulnerability in Microsoft's SMBv1 network resource-sharing protocol. The exploit lets an attacker transmit crafted packets to any system that accepts data from the public internet on port 445 -- the port reserved for SMB. SMBv1 is a deprecated network protocol.
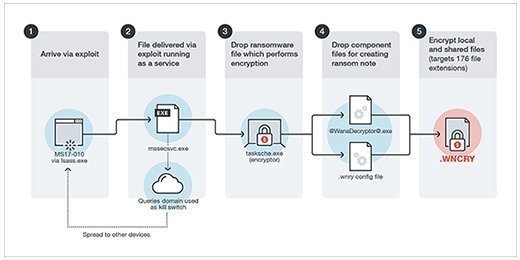
WannaCry appears on computers as a dropper, which is a small helper program that delivers and installs malware. Components in the dropper include an application for data encryption and decryption, files of encryption keys and a copy of Tor for command-and-control communications.
WannaCry uses the EternalBlue exploit to spread. The first step attackers take is to search the target network for devices accepting traffic on TCP port 445, which indicates the system is configured to run SMB. This is generally done by conducting a port scan. Next, attackers initiate an SMBv1 connection to the device. After the connection is made, a buffer overflow is used to take control of the targeted system and install the ransomware component of the attack.
Once a system is affected, the WannaCry worm propagates itself and infects other unpatched devices -- all without any human interaction.
Even after victims paid the ransom, the ransomware didn't automatically release their computers and decrypt their files, according to security researchers. Rather, victims had to wait and hope that WannaCry's developers would deliver decryption keys for the hostage computers remotely over the internet -- a completely manual process that contained a significant flaw: The hackers didn't have any way to prove who paid the ransom. Since there was only a slight chance the victims would get their files decrypted, the wiser choice was to save their money and rebuild the affected systems, according to security experts.
What was the impact of WannaCry?
WannaCry caused significant financial consequences, as well as extreme inconvenience for businesses across the globe.
The initial May 2017 attack is estimated to have hit more than 230,000 devices. Innumerable devices have fallen victim since. More than 150 countries were affected by the attack, including England, India, Russia, Taiwan and Ukraine. Many different industries were also infected by the attack, including those in the automotive, emergency, healthcare provider, security and telecom sectors. For example, hospital equipment and ambulances were affected by the attack.
Estimates of the total financial impact of the initial WannaCry attack were generally in the hundreds of millions of dollars, though Symantec estimated the total costs at $4 billion. However, what surprised experts about this attack was how little damage it did compared to what it could have done given its worm functionality.
In the wake of the WannaCry attack, the U.S. Congress introduced the Protecting Our Ability to Counter Hacking Act in May 2017. The act proposed having any software or hardware vulnerabilities in the government's possession reviewed by an independent board. The act never passed.
WannaCry did prove to be a wake-up call for the enterprise cybersecurity world to implement better security programs and renew its focus on the importance of patching. Many security teams have better educated themselves and their IT departments to protect their organizations against ransomware. The chief information security officer role has also seen an upsurge in prominence, according to the Security Intelligence blog run by IBM Security.
The WannaCry attacks also ignited the popularity of commercial ransomware attacks among the hacker community. Ransomware constituted 24% of all breaches in 2022, according to Verizon's "2023 Data Breach Investigations Report." Of those cases, 94% include system intrusion.
Stopping the spread of WannaCry
One day after the initial attack, Microsoft released a security update for Windows 8, Windows Server 2003 and Windows XP to fix the vulnerability. Organizations were advised to patch their Windows systems to avoid being hit by the attack.
WannaCry uses a technique called a kill switch to determine whether the malware should encrypt a targeted system. Hardcoded into the malware is a web domain that WannaCry checks for the presence of a live webpage when it first runs. If attempting to access the kill switch and the domain doesn't result in a live webpage, the malware encrypts the system.
Hutchins discovered he could activate the kill switch if he registered the web domain and posted a page on it. Originally, Hutchins wanted to track the spread of the ransomware through the domain it was contacting, but he soon found that registering the domain stopped the spread of the infection.
Other security researchers reported the same findings as Hutchins and said new ransomware infections appeared to have slowed since the kill switch was activated.
In August 2017, after a two-year investigation and just months after he stopped the spread of WannaCry and was publicly identified, Hutchins was arrested by the Federal Bureau of Investigation. He was accused of helping create and spread the Kronos banking Trojan, malware that recorded and exfiltrated user credentials and personally identifiable information from protected computers. In 2019, Hutchins pled guilty to two of the 10 charges he faced but was spared a jail sentence. Instead, he served a one-year supervised release and was allowed to return to the U.K.
Is WannaCry still a threat?
Even though Microsoft issued security updates that fixed the SMBv1 vulnerability, the exploit that enabled the rapid spread WannaCry ransomware still threatens unpatched and unprotected systems.
Although the automatic update feature of Windows 10 blocks WannaCry and Windows 11 has a feature that protects computers from ransomware, many companies fail to patch their systems for several reasons. These include a lack of resources or planning, as well as the threat of downtime to critical systems in the updating process. Researchers at Check Point Software documented a 53% increase in companies affected by WannaCry attacks in the first quarter of 2021, in congruence with a 57% increase in ransomware attacks in the fourth quarter of 2020 and the first quarter of 2021.
With WannaCry also came the concept of the ransomworm and cryptoworm -- code that spreads via remote office services, cloud networks and network endpoints. A ransomworm only needs one entry point to infect an entire network. It then self-propagates to spread to other devices and systems.
Since the initial WannaCry attack, more sophisticated variations of the ransomworm have emerged. These new variants are moving away from traditional ransomware attacks that must have constant communication back to their controllers -- replacing them with automated, self-learning methods.
Exploits of Microsoft's SMB protocol have been extremely successful for malware writers, with EternalBlue also being a key component of the destructive June 2017 NotPetya ransomware attacks.
The exploit was also used by the Russian-linked Fancy Bear cyberespionage group, also known as Sednit, APT28 or Sofacy, to attack Wi-Fi networks in European hotels in 2017. The exploit has been identified as one of the spreading mechanisms for malicious crypto miners.
How to defend against WannaCry
The first step to preventing WannaCry is to disable SMBv1 and update to the latest software. Version 3.1.1 was released in 2020. Keep all Windows systems patched and up to date. If possible, block traffic on port 445.
Beyond that, organizations can defend against WannaCry and other ransomware variants by doing the following:
- Setting up secure backup procedures that can be used even if the network is disabled and backing up data regularly.
- Educating users on the dangers of phishing, weak passwords and other methods that could lead to ransomware attacks.
- Using antivirus programs with ransomware protection features.
- Keeping software, antimalware and firewall software up to date.
- Using complex passwords and changing them periodically.
- Not clicking on suspicious links or attachments.
WannaCry can be removed manually, though the process isn't recommended for less skilled users. Users can also remove WannaCry with a number of tools. For example, Microsoft's Windows Malicious Software Removal Tool and most other antimalware software remove the threat.
Learn how WannaCry ransomware continued to spread up to two years after the initial infection.







