challenge-response authentication
In computer security, challenge-response authentication is a set of protocols used to protect digital assets and services from unauthorized users, programs or activities. While challenge-response authentication can be as simple as a password, it can also be as dynamic as a randomly generated request. From login verification to machine learning (ML), challenge-response authentication is an easy-to-implement cybersecurity tool to secure sensitive information, identify suspicious behavior or block certain programs.
What is challenge-response authentication?
In its simplest form, challenge-response authentication is composed of two basic components: a question and a response. The goal of the question, or challenge, is to require a response that only authorized users will know. Users that successfully answer the question are allowed access to whatever digital materials the challenge-response authentication mechanism (CRAM) is safeguarding. Though this is a simple premise, the tools, knowledge and information required to pass these challenges can become quite complex.
The goal of challenge-response authentication is to limit the access, control and use of digital resources to only authorized users and activities. After all, users aren't the only ones sending requests. If a mobile application or a malicious software (malware) program requests access to a set of photos, it can be denied by integrating challenge-response authentication. Because challenges aren't just limited to questions and answers, they can involve more complicated tasks and code decryption.
Types of challenge-response questions
There are two main types of challenge-response questions: static and dynamic. Each varies in terms of complexity and response variability.
Static challenges are requests that can be satisfied using the same answer or process every time. A static challenge includes the password recovery questions one needs to answer to verify identity. A common example is the password for the lock screen on a smartphone.
Dynamic challenges require a different answer with each attempt. Often, the challenges themselves randomly change, and the user is expected to respond. Some financial institutions provide their account holders with a small security token, a device that can either receive codes or input them. Devices like these also provide a physical element to the authentication process, which makes it even harder for cybercriminals to exploit.
Challenge-response authentication wasn't always exclusive to digital use. In the early 20th century, U.S. military officials used DRYAD, a simple, paper cryptographic system, to authenticate the identities of radio users. The purpose of this challenge-response authentication system was to ensure the person on either end of the radio was not an imposter. Through the DRYAD numeral cipher, two individuals could verify their identities by reading out the corresponding number for a combination of letters. This example illustrates that challenges don't have to be in the form of a question; they can be numerical or digital permutations that require a designated response.
One of the most common examples of a challenge-response protocol is password authentication. The challenge, in this case, is providing the word, phrase or code that unlocks the device, network or program. Here, challenge-response authentication is the only thing preventing a criminal from accessing the sensitive files, credentials and information stored in a computer system. Without challenge-response authentication, it would be impossible to perform activities like online banking with a high degree of security confidence.
How challenge-response is used
Challenge-response is a barrier used to protect assets from unauthorized users, activities, programs and internet of things (IoT) devices. It forces cyber attackers to satisfy a potential series of challenges in order to bypass the security barrier and access further materials. A commercial bank, for instance, uses challenge-response authentication to create a multifactor authentication (MFA) process. This process authenticates the identity of a user by utilizing multiple CRAMs.
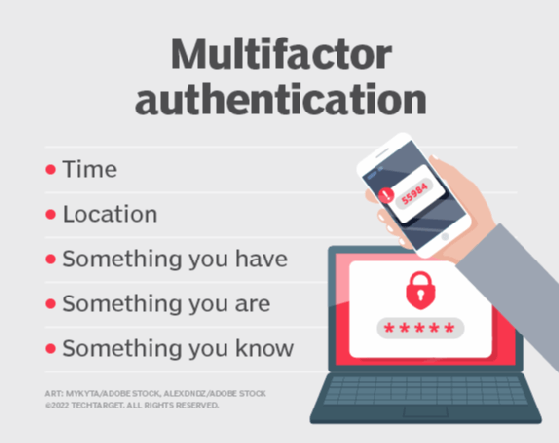
An example of a two-factor authentication (2FA) process involves providing a password and a code sent to a specified email address. An MFA variant may also require the answer to a personal question, like "What is your mother's maiden name?" Account logins aren't the only instance of challenge-response authentication, though.
Different uses of challenge-response authentication
In addition to login authentication, there are two main areas in which challenge-response can be utilized, particularly when it comes to cybersecurity.
Human verification
Sometimes, when users log in to a website, they are asked to complete a series of challenges to prove that they are not a robot (bot). Challenges like this are designed to block programs, not users, from accessing certain webpages or activities. For instance, many electronic commerce (e-commerce) platforms use human verification in order to prevent bots from automatically buying up massive amounts of supplies. Not only can these bots limit the experience of regular users, but they may also be using fraudulent or stolen information to complete purchases. Challenge-response authentication is a way to avoid this outcome and ensure the safety and security of specific web services. A common challenge used to verify human activity includes selecting images that contain a specific item or object, such as a fire hydrant, for example. CAPTCHA (Completely Automated Public Turing test to tell Computers and Humans Apart) is an example of this type of tool being put to use.
Machine learning training
One of the greatest advantages of machine learning is its ability to complete many tasks at the same time. In cybersecurity, ML or artificial intelligence (AI) software combs systems for suspicious or dangerous behavior. Challenge-response authentication tests and trains machine learning models to help them solve complex problems. Some ML programs are given human verification puzzles and their answers are matched and compared to those of humans. Over time, the ML program learns from the human examples to inform its future decision-making.
Examples of challenge-response authentication systems
In addition to its applications for verifying users and passwords, challenge-response authentication systems can be classified by the cryptographic algorithms and techniques they use for securing the authentication process.
Challenge-response commonly incorporates the following authentication technologies:
- Secure Shell (SSH) protocol includes a challenge-response mechanism that uses separate public key infrastructure (PKI) to authenticate communication sessions between servers. Each server authenticates itself by sending the other a value signed with the other's public key.
- Zero-knowledge password proof systems use cryptographic methods to confirm to each party that they have a correct password but without the need to share that password with each other.
- Challenge-Handshake Authentication Protocol (CHAP) uses a three-way handshake among an authenticating system, challenge message and local system. If the hash values generated from this handshake match, then the authenticating system can permit the connection. If they do not, it will terminate the session.
- OATH Challenge-Response Algorithm (OCRA) uses a challenge-response algorithm developed by the Initiative for Open Authentication for a cryptographically strong challenge-response authentication.
Best practices for challenge-response authentication
How well an organization implements, designs and deploys its interactive challenge-response authentication systems has a significant impact on its overall effectiveness. Businesses should consider the following best practices and guidelines for ensuring high-quality challenge-response authentication:
- Implement an automated enrollment system to invite users to complete their challenge-response profiles.
- Avoid questions with answers that can be guessed or researched.
- Use questions that can be remembered by users.
- Use a combination of standardized and user-selected questions. User-generated questions are more unique and, therefore, more difficult to guess.
- Use multiple tiers of questions: Ask standard questions first, and then ask user-generated questions after the first set has been correctly answered.
- Avoid asking the user to respond to more than six questions during the authentication process to discourage frustration and abandon rates.
- Do not display answers to challenge questions. Doing so can expose them to malicious eavesdroppers.
- Encrypt all data that may be used for authentication, particularly a user's answers to personal challenge questions.
- Lock user accounts after a specified number of failed authentication attempts.
Learn more about authentication methods and how to best implement them in "Strong authentication methods: Are you behind the curve?"








