cyberterrorism
What is cyberterrorism?
Cyberterrorism is usually defined as any premeditated, politically motivated attack against information systems, programs, and data that threatens violence or results in violence. It might include any cyberattack that intimidates or generates fear in the target population of a country, state, or city, usually by damaging or disrupting critical infrastructure that's vital to social, economic, political, and business operations.
Cyberterrorist acts are carried out using computer servers, other devices and networks visible on the public internet. Secured government networks and other restricted networks are often targets of such acts. Other targets include the banking industry, military installations, power plants, air traffic control centers, and water systems.
The U.S. Federal Bureau of Investigation (FBI) defines cyberterrorism as any "premeditated, politically motivated attack against information, computer systems, computer programs and data, which results in violence against noncombatant targets by subnational groups or clandestine agents." Per the FBI, a cyberterrorist attack is a type of cybercrime explicitly designed to cause physical harm.
Other organizations and experts include less harmful attacks as acts of cyberterrorism, especially when those are intended to be disruptive or to further the attackers' political agenda. The North Atlantic Treaty Organization (NATO), defines cyberterrorism as a cyberattack that uses or exploits computer or communication networks to cause "sufficient destruction or disruption to generate fear or to intimidate a society into an ideological goal."
Methods used for cyberterrorism
The intention of cyberterrorist groups is to cause mass chaos, disrupt critical infrastructure, support political activism or hacktivism, or inflict physical damage and even loss of life. Cyberterrorism actors use various methods to achieve these aims, including:
- Advanced persistent threat (APT) attacks, which use sophisticated, concentrated penetration methods to gain network access. Once inside the network, the attackers stay undetected for a time, intending to steal data. Organizations with high-value information, such as those in the defense, manufacturing, healthcare, and financial industries are typical targets for APT attacks.
- Computer viruses, worms and malware target IT control systems. They are used to attack utilities, transportation systems, power grids, critical infrastructure, government departments, and military systems.

- Denial of service (DoS) attacks attempt to prevent legitimate users from accessing targeted computer systems, devices, or websites. These attackers often go after critical infrastructure and governments.
- Hacking seeks to gain unauthorized access to steal critical data, often from institutions, governments and businesses.
- Ransomware, a type of malware, is aimed at holding data or information systems hostage (usually via encryption) until the victim pays the ransom. Some ransomware attacks also exfiltrate data.
- Phishing attacks attempt to collect information through a target's email, using that information to access systems or steal the victim's identity.
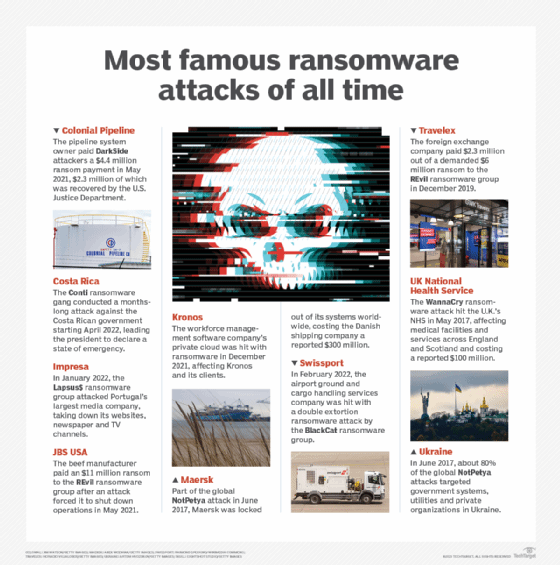
What are examples of cyberterrorism?
Examples of cyberterrorism include:
- Disruption of major websites. The intent is to stop traffic to websites that serve many users and whose disruption might create widespread public inconvenience.
- Unauthorized access. Attackers often aim to gain access to certain systems or to modify communications that control military systems or other critical technology.
- Disruption of critical infrastructure systems. Threat actors try to disable or disrupt cities, cause a public health crisis, endanger public safety or cause massive panic and fatalities, for example, by targeting a water treatment plant, causing a regional power outage, or disrupting an oil or gas pipeline.
- Cyberespionage. Rogue governments or nation-states carry out or sponsor cyberespionage attacks to spy on rival nations and gather sensitive, secret, or confidential intelligence, such as troop locations or military strategies.
Strategies to defend against cyberterrorism
In the past, cyberterrorism mostly targeted government entities. But now, businesses and other organizations are becoming targets as well, so they must implement extensive cybersecurity measures and vigilance to counter cyberterrorism. For one, they must ensure that all internet of things devices are secured and inaccessible via public networks. To protect against ransomware and similar types of attacks, they must back up systems regularly and implement continuous monitoring techniques. They must also use firewalls, antivirus software, and antimalware to protect their systems from these attack vectors. Companies must also implement controls and IT security policies to protect business data. This includes limiting access to sensitive data and enforcing strict password and authentication procedures, like two-factor authentication or multifactor authentication.
International efforts to combat cybercrime and cyberterrorism
The National Cyber Security Alliance is a public-private partnership to promote cybersecurity awareness and create a more secure and interconnected world. It is contributing to the global fight against cybercrime and cyberterrorism. Similarly, the U.S. Department of Homeland Security (DHS) coordinates with other public sector agencies and private sector partners. It shares information on potential terrorist activity and how to protect national security, as well as counterterrorism measures that the U.S. -- and all countries -- can implement to combat the (growing) problem of cyberterrorism.
The Council of Europe's Convention on Cybercrime (also known as the Budapest Convention on Cybercrime) is the world's first-ever international treaty that seeks to address cybercrime and cyberwarfare by getting countries to cooperate with each other, share information, and harmonize their national laws. As of 2024, 69 countries have ratified the Convention. Another 22 have been invited to accede.
The United Nations has also proposed a major cybercrime treaty that is likely to address multiple topics, including international cooperation, access to digital evidence by law enforcement authorities, and procedural safeguards. Its text and all associated negotiations are expected to be finalized in 2024.
Want to protect your IT infrastructure and data from cyberterrorists and other attackers? Check out our guide to successful cybersecurity planning. Explore top seven enterprise cybersecurity challenges and how to fix the top five cybersecurity vulnerabilities. See how to develop a cybersecurity strategy. Check out nine cybersecurity trends to watch.






