digital signature
What is a digital signature?
A digital signature is a mathematical technique used to validate the authenticity and integrity of a digital document, message or software. It's the digital equivalent of a handwritten signature or stamped seal, but it offers far more inherent security. A digital signature is intended to solve the problem of tampering and impersonation in digital communications.
Digital signatures can provide evidence of origin, identity and status of electronic documents, transactions and digital messages. Signers can also use them to acknowledge informed consent. In many countries, including the U.S., digital signatures are considered legally binding in the same way as traditional handwritten document signatures.
How do digital signatures work?
Digital signatures are based on public key cryptography, also known as asymmetric cryptography. Using a public key algorithm, such as Rivest-Shamir-Adleman, or RSA, two keys are generated, creating a mathematically linked pair of keys: one private and one public.
Digital signatures work through public key cryptography's two mutually authenticating cryptographic keys. For encryption and decryption, the person who creates the digital signature uses a private key to encrypt signature-related data. The only way to decrypt that data is with the signer's public key.
If the recipient can't open the document with the signer's public key, that indicates there's a problem with the document or the signature. This is how digital signatures are authenticated.
Digital signing certificates, also called public key certificates, are used to verify that the public key belongs to the issuer. Signing certificates are sent with the public key; they contain information about the certificate's owner, expiration dates and the digital signature of the certificate's issuer. Trusted third-party certificate authorities (CAs), such as DocuSign or GlobalSign, issue signing certificates.
Digital signature technology requires all parties to trust that the person who creates the signature image has kept the private key secret. If someone else has access to the private signing key, that party could create fraudulent digital signatures in the name of the private key holder.
Signing certificate and certificate authority
Digital signatures get their official status through signing certificates. Signing certificates serve as authentication for transmitted documents, their contents and the author of these documents. An official third-party certificate authority is responsible for administering these certificates. CAs verify that organizations are in compliance with cybersecurity standards, such as International Organization for Standardization (ISO) standards. Only after an organization has been approved is a certificate provided.
The approval process starts with the CA assessing the needs of the author and ensuring their methods comply with regulations. The CA then issues a signing certificate and the cryptographic key pair needed to secure the documents' contents. A mathematical algorithm generates this key pair to ensure the contents can't be accessed without both keys. Ultimately, the digital signature includes the following:
- The author's electronic signature of the document.
- A piece of data called a cryptographic hash that is unique to the author's documents and is used to verify the authenticity of the document.
- The signing certificate from the CA, which contains the public key and the written proof that the CA has approved the process.
- The private key, which the author must keep confidential and which is used to encrypt the documents.
Signing certificates assure recipients of the authenticity of both the author and documents and that the documents are free from prior tampering or forgery. The author sending the documents and the recipient receiving them must agree to use a given CA.
What are the benefits of digital signatures?
Digital signatures offer the following advantages:
- Security. Security capabilities are embedded in digital signatures to ensure a legal document isn't altered and signatures are legitimate. Security features include asymmetric cryptography, personal identification numbers (PINs), checksums and cyclic redundancy checks (CRCs), as well as CA and trust service provider (TSP) validation.
- Timestamping. This provides the date and time of a digital signature and is useful when timing is critical, such as for stock trades, lottery ticket issuance and legal proceedings.
- Globally accepted and legally compliant. The public key infrastructure (PKI) standard ensures vendor-generated keys are made and stored securely. With digital signatures becoming an international standard, more countries are accepting them as legally binding.
- Time savings. Digital signatures simplify the time-consuming processes of physical document signing, storage and exchange, letting businesses quickly access and sign documents.
- Cost savings. Organizations can go paperless and save money previously spent on the physical resources, time, personnel and office space used to manage and transport documents.
- Positive environmental effects. Reducing paper use cuts down on the physical waste paper generates and the negative environmental impact of transporting paper documents.
- Traceability. Digital signatures create an audit trail that makes internal record-keeping easier for businesses. With everything recorded and stored digitally, there are fewer opportunities for a manual signee or record-keeper to make a mistake or misplace something.
What are the challenges of digital signatures?
Challenges sometimes crop up when organizations use digital signatures. These include the following:
- Insecure channels. Despite the security layer digital signatures provide, the channels used to transmit documents can still have inadequate security measures. Without proper encryption and authentication, they could lead to compromised documents and data loss.
- Key management. Compromised or lost keys are useless; therefore, organizations must be prepared to craft policies and procedures for employees to properly manage their keys, which can be complicated.
- Compliance. Different standards are used in different jurisdictions regarding digital signatures, so an organization must consult with legal experts or have a knowledgeable person to handle these matters.
How do you create a digital signature?
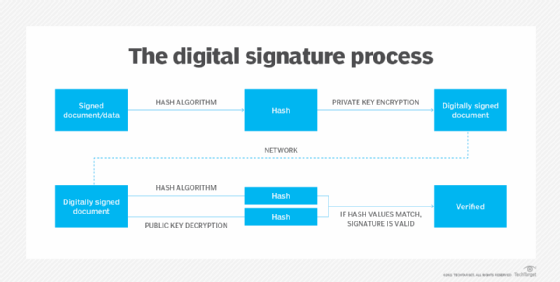
To create a digital signature, signing software, such as an email program, is used to provide a one-way hash of the electronic data to be signed.
A hash is a fixed-length string of letters and numbers generated by an algorithm. The digital signature creator's private key is used to encrypt the hash. The encrypted hash -- along with other information, such as the hashing algorithm -- is the digital signature.
The reason for encrypting the hash instead of the entire message or document is because a hash function can convert an arbitrary input into a fixed-length value, which is usually much shorter. This saves time, as hashing is much faster than signing.
The value of a hash is unique to the hashed data. Any change in the data -- even a modification of a single character -- results in a different value. This attribute lets others use the signer's public key to decrypt the hash to validate the integrity of the data.
If the decrypted hash matches a second computed hash of the same data, it proves that the data hasn't changed since it was signed. But, if the two hashes don't match, the data has either been tampered with in some way and is compromised or the signature was created with a private key that doesn't correspond to the public key presented by the signer. This signals an issue with authentication.
A digital signature can be used with any kind of message, whether or not it's encrypted, simply so the receiver can be sure of the sender's digital identity and that the message arrived intact. Digital signatures make it difficult for the signer to deny having signed something, as the digital signature is unique to both the document and the signer, and it binds them together. This property is called nonrepudiation.
The signing certificate is the electronic document that contains the digital signature of the issuing CA. It's what binds together a public key with an identity and can be used to verify that a public key belongs to a particular person or entity. Most modern email programs support the use of digital signatures and signing certificates, making it easy to sign any outgoing emails and validate digitally signed incoming messages.
Digital signatures are also used to provide proof of authenticity, data integrity and nonrepudiation of communications and transactions conducted over the internet.
Classes and types of digital signatures
There are three different classes of digital signature certificates (DSCs) as follows:
- Class 1. This type of DSC can't be used for legal business documents because they're validated based only on an email ID and username. Class 1 signatures provide a basic level of security and are used in environments with a low risk of data compromise.
- Class 2. These DSCs are often used for electronic filing (e-filing) of tax documents, including income tax returns and goods and services tax returns. Class 2 digital signatures authenticate a signer's identity against a preverified database. Class 2 digital signatures are used in environments where the risks and consequences of data compromise are moderate.
- Class 3. The highest level of digital signatures, Class 3 signatures, require people or organizations to present in front of a CA to prove their identity before signing. Class 3 digital signatures are used for e-auctions, e-tendering, e-ticketing and court filings, as well as in other environments where threats to data or the consequences of a security failure are high.
Use cases for digital signatures
Digital signature tools and services are commonly used in contract-heavy industries, including the following:
- Government. The U.S. Government Publishing Office publishes electronic versions of budgets, public and private laws, and congressional bills with digital signatures. Governments worldwide use digital signatures for processing tax returns, verifying business-to-government transactions, ratifying laws and managing contracts. Most government entities must adhere to strict laws, regulations and standards when using digital signatures. Many governments and businesses also use smart cards to identify their citizens and employees. These are physical cards with an embedded chip that contains a digital signature that provides the cardholder access to an institution's systems or physical buildings.
- Healthcare. Digital signatures are used in the healthcare industry to improve the efficiency of treatment and administrative processes, strengthen data security, e-prescribe and process hospital admissions. The use of digital signatures in healthcare must comply with the Health Insurance Portability and Accountability Act of 1996.
- Manufacturing. Manufacturing companies use digital signatures to speed up processes, including product design, quality assurance, manufacturing enhancements, marketing and sales. The use of digital signatures in manufacturing is governed by ISO and the National Institute of Standards and Technology Digital Manufacturing Certificate.
- Financial services. The U.S. financial sector uses digital signatures for contracts, paperless banking, loan processing, insurance documentation and mortgages. This heavily regulated sector uses digital signatures, paying careful attention to the regulations and guidance put forth by the Electronic Signatures in Global and National Commerce Act (E-Sign Act), state Uniform Electronic Transactions Act regulations, the Consumer Financial Protection Bureau and the Federal Financial Institutions Examination Council.
- Cryptocurrencies. Bitcoin and other cryptocurrencies use digital signatures to authenticate the blockchain they use. They're also used to manage transaction data associated with a cryptocurrency and as a way for users to show ownership of currency and their participation in a transaction.
- Non-fungible tokens (NFTs). Digital signatures are used with digital assets, such as artwork, music and videos, to secure and trace these types of NFTs anywhere on the blockchain.
Why use PKI or PGP with digital signatures?
Digital signatures use the PKI standard and the Pretty Good Privacy (PGP) encryption program. Both reduce potential security issues that come with transmitting public keys. They validate that the sender's public key belongs to that individual and verify the sender's identity.
PKI is a framework for services that generate, distribute, control and account for public key certificates. PGP is a variation of the PKI standard that uses symmetric key and public key cryptography, but it differs in how it binds public keys to user identities. PKI uses CAs to validate and bind a user identity with a signing certificate, whereas PGP uses a web of trust. Users of PGP choose whom they trust and which identities get vetted. PKI users defer to trusted CAs.
The effectiveness of a digital signature's security is dependent on the strength of the private key security. Without PKI or PGP, it's impossible to prove someone's identity or revoke a compromised key, and it's easier for malicious actors to impersonate people.
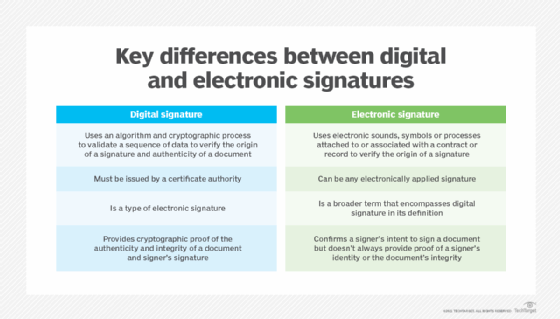
What's the difference between a digital signature and electronic signature?
Though the two terms sound similar, digital signatures are different from electronic signatures. Digital signature is a technical term, defining the result of a cryptographic process or mathematical algorithm that can be used to authenticate a sequence of data. It's a type of electronic signature. The term electronic signature (e-signature) is a legal term that's defined legislatively.
For example, in the U.S., the E-Sign Act, passed in 2000, provides a definition of an e-signature. It stated that an e-signature is "an electronic sound, symbol or process attached to or logically associated with a contract or other record and executed or adopted by a person with the intent to sign the record."
E-signatures are also defined in the Electronic Signatures Directive, which the European Union (EU) passed in 1999 and repealed in 2016. It regarded them as equivalent to physical signatures. This act was replaced with electronic identification, authentication and trust services, or eIDAS, which regulates e-signatures and transactions in the EU, as well as the embedding processes that ensure the safe conduct of online business.
This means that a digital signature, which can be expressed digitally in electronic form and associated with the representation of a record, can be a type of e-signature. More generally, though, an e-signature can be as simple as a signature online, like the signer's name being entered in a web browser on a form.
To be considered valid, e-signature schemes must include the following three capabilities:
- A way to verify the identity of the entity signing it.
- A way to verify the signing entity intended to affirm the document being signed.
- A way to verify that the e-signature is associated with the signed document.
A digital signature fulfills these requirements to serve as a valid e-signature under the following conditions:
- The public key of the digital signature is linked to the signing entity's electronic identification.
- The digital signature can only be affixed by the holder of the public key's associated private key, which implies the entity intends to use it for the signature.
- The digital signature only authenticates if the signed data -- for example, a document or representation of a document -- is unchanged. If a document is altered after being signed, the digital signature fails to authenticate.
Authenticated digital signatures provide cryptographic proof that a stated entity signed a document and that the document hasn't been altered. However, not all e-signatures provide the same guarantees.
Digital signature security
Security is the main benefit of using digital signatures. Security features and methods used in digital signatures include the following:
- PINs, passwords and codes. These are used to authenticate and verify a signer's identity and approve their signature. Email, username and password are the most common methods used.
- Asymmetric cryptography. This uses a public key algorithm that includes private and public key encryption and authentication.
- Checksum. This long string of letters and numbers is used to determine the authenticity of transmitted data. A checksum is the result of running a cryptographic hash function on a piece of data. The value of the original checksum file is compared against the checksum value of the calculated file to detect errors or changes. A checksum acts like a data fingerprint.
- CRC. A type of checksum, this error-detecting code and verification feature is used in digital networks and storage devices to detect changes to raw data.
- CA validation. CAs issue digital signatures and act as trusted third parties by accepting, authenticating, issuing and maintaining signing certificates. The use of CAs helps avoid the creation of fake signing certificates.
- TSP validation. This person or legal entity validates a digital signature on a company's behalf and offers signature validation reports.
Digital signature attacks
Possible attacks on digital signatures include the following:
- Chosen-message attack. The attacker either obtains the victim's public key or tricks the victim into digitally signing a document they don't intend to sign.
- Known-message attack. The attacker obtains messages the victim sent and a key that enables the attacker to forge the victim's signature on documents.
- Key-only attack. The attacker has access to the victim's public key and re-creates the victim's signature to digitally sign documents or messages that the victim doesn't intend to sign.
Digital signature tools and vendors
There are numerous digital and electronic signature tools and technologies on the market. Gartner has compiled a list of electronic signature tools that is worth a look:
- Adobe Acrobat Sign. This is a cloud-based service designed to provide secure e-signatures across all types of devices. Adobe Acrobat Sign integrates with existing applications, including Microsoft Office and Dropbox.
- Docusign. Its standards-based services ensure e-signatures are compliant with existing regulations. Services include Express Signature for basic global transactions and EU Qualified Signature, which complies with EU standards.
- Dropbox Sign. This tool helps users prepare, send, sign and track documents. Features include embedded signing and templates, as well as custom branding. Dropbox Sign integrates with applications such as Microsoft Word, Slack and Box.
- EmSigner. This product creates workflows for orchestrating and automating the signing of digital documents.
- GetAccept. This sales collaboration platform facilitates the e-signature process for business documents with traceability capabilities.
- OneSpan Sign. This tool provides signature authentication and validation capabilities for commercial and banking applications.
- PandaDoc. This e-signature software lets users upload, send and collect document payments. Users can also track document status and receive notifications when someone opens, views, comments on or signs a document.
- SignNow. As part of AirSlate Business Cloud, SignNow provides a PDF signing tool.
- Zoho Sign. With this tool, users can sign documents while using either Zoho or third-party apps; it offers application programming interfaces to integrate and automate the document signing process.
As more documents get transmitted electronically, having the right digital signature platform has become important. Learn about e-signature software platforms that might be candidates.





