dumpster diving
What is dumpster diving?
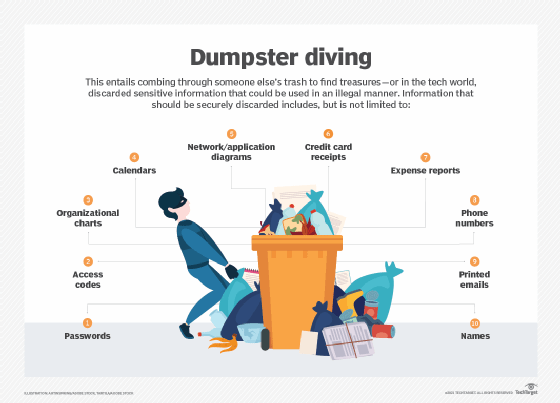
Dumpster diving is looking for treasure in someone else's trash. In the world of information technology (IT), dumpster diving is a technique used to retrieve information that could be used to carry out an attack or gain access to a computer network from disposed items.
Dumpster diving isn't limited to searching through the trash for obvious treasures, such as access codes or passwords written down on sticky notes. Seemingly innocent information, such as a phone list, calendar or organizational chart, can be used to assist an attacker using social engineering techniques to gain access to the network.
To prevent dumpster divers from learning anything valuable from trash, experts recommend that businesses establish a disposal policy where all paper -- including printouts -- is shredded in a cross-cut shredder before being recycled, all storage media is erased and all staff is educated about the danger of untracked trash.
Disposed computer hardware can be a gold mine for attackers. Information can be recovered from storage media, including drives that have been improperly formatted or erased. This includes stored passwords and trusted certificates. Even without the storage media, the equipment may include Trusted Platform Module (TPM) data or other hardware IDs that are trusted by an organization. An attacker may also be able to use the hardware to identify the equipment manufacturer to craft potential exploits.
Medical and personnel records may have legal consequences if not properly disposed of. Documents that contain personally identifiable information (PII) must be destroyed, or the organization could be exposed to breaches and potential fines. For example, in 2010, a medical billing office in Massachusetts was fined $140,000, and in 2014, a medical provider in Kansas City, M.O., was fined $400,000.
Dumpster diving and social engineering attacks
Social engineering is using human interaction to trick another person into giving access or performing an action for the attacker. A primary goal of social engineering is to establish trust between the attacker and the target. Dumpster diving is a way for attackers to gain information that they use to establish trust. While attackers will also take any computer equipment they find, typically, the primary focus of a dumpster diving attack is to gain information about an organization. Even innocuous documents can be used by an attacker.
A list of names -- such as a directory or phone list -- can be used in many ways by an attacker. Employees' names can be used to guess their computer username, to attack their personal web accounts or for identity theft. A name list can also be used as part of a general phishing campaign against an organization or a spear phishing attack against an executive.
Telephone numbers can be used with caller ID spoofing to coerce an employee to reveal other information in a voice phishing (vishing) attack. An attacker could use this to call an employee with a story like, "Hi, this is John in accounting. The head of finance, Bill, needs some numbers by tonight. I asked Debbie, and she said to talk to you. Can you help me?"
Social engineering attacks use information gathered from dumpster diving. If attackers find a receipt for a vending machine restocking service, they may pretend to be employees of the service with a name badge on the same day and time as an expected delivery to gain access to areas that are not open to the public. Attackers could use this access to do a shoulder surfing attack or install a keylogger to gain access to the network.
How to prevent a dumpster diving attack
Although it may seem like a lot of work to properly care for trash, processes can be put in place to help prevent a dumpster diving attack. These should be documented and clearly explained to employees.
- Have a documented equipment decommissioning process. Ensure all identifiable information is removed from computer equipment before it is disposed of or sold. This includes securely erasing data from hard drives and clearing TPM data. Remove any trust factors in organizational databases, such as domain trust relationships, media access control (MAC) address authentication or expiring trust certificates.
- Use the appropriate secure storage media deletion process. This may include securely erasing disk drives, shredding compact discs (CDs) and degaussing magnetic storage.
- Have a data retention policy, and use certificates of destruction for sensitive data. Data retention policies should state how long documents and data should be kept and how they should be discarded. A certificate of destruction should be created and filed for legal tracking.
- Make shredding convenient. Provide easy access to shredders next to recycling bins, or use secure shred bins next to every trash can. For employees who work from home, provide home paper shredders.
- Educate employees. Provide information on proper disposal and typical social engineering methods. Do not allow employees to take printouts home, and do not give old computer equipment to employees.
- Secure trash. Use locked trash and recycling bins, or keep refuse in a secure area until it is ready to be picked up. Use trusted equipment recyclers.