logic bomb
What is a logic bomb?
A logic bomb is a string of malicious code inserted intentionally into a program to harm a network when certain conditions are met. The term comes from the idea that the code "explodes" when triggered by a specific event, such as a certain date or time, the deletion of a particular record -- e.g., an employee -- from a system or the launch of the infected software application.
Also known as slag code, a logic bomb often remains undetected until it executes its function or launches its payload. The set of conditions able to set it off is virtually unlimited. Additionally, the degree of destruction from a logic bomb can vary greatly from deleting files and corrupting data to clearing hard drives and causing application failure.
Unlike many other types of cyber attacks, a logic bomb attack is subtle yet often sophisticated and capable of causing explosive damage that's difficult to trace or mitigate. A malicious piece of code is secretly inserted into a computer's or network's existing software. It may also be inserted into other forms of malware such as viruses, worms or Trojan horses.
A logic bomb is sneaky because its code lies dormant until the trigger occurs. This deliberate time lag between code insertion and action (payload release) enables bombers to control when the attack happens. More importantly, it enables them to cover their tracks since the logic bomb usually remains undetectable, sometimes for months or even years.
The bomb's "detonator" is the particular condition that must be met. If the trigger is related to a date or time, the logic bomb will go off on a certain date -- e.g., Y2K -- and is known as a time bomb. Its payload refers to the specific component that's programmed to cause damage, such as deleting files, sending spam emails and stealing data.
The payload is usually unknown until it triggers. This is why it is so difficult to mitigate, much less prevent, the damage from logic bombs.

How does a logic bomb work?
Either positive or negative conditions can trigger a logic bomb. A logic bomb coded with a positive condition goes off when that condition is met, while a bomb coded with a negative condition goes off when that condition is not met.
An example of a positive condition could be the opening of a particular file. An example of a negative condition is the code not being detected or deactivated before a certain date.
Whether the condition is positive or negative, as long as it's met, the logic bomb will go off and inflict damage unless a way is found to mitigate the condition or remove the code.
Is a logic bomb the same as malware?
The code in a logic bomb is malicious, but it's not technically malware. However, some types of malware like viruses can contain logic bombs to cause harm to a system or network.
Also, unlike some forms of malware like viruses or worms that break into a secure system on their own, a logic bomb attack is usually a form of cyber sabotage launched by an internal -- usually a malicious -- attacker. This might include a disgruntled current or former employee, such as a programmer or information technology administrator with access to sensitive data or administrative access to systems.
Employees who believe they might be fired might create logic bombs to exact revenge on their companies. While they remain with their companies, they might defuse the bombs each day. Then, once they're out, they can launch the attacks at any time to cause maximum harm.
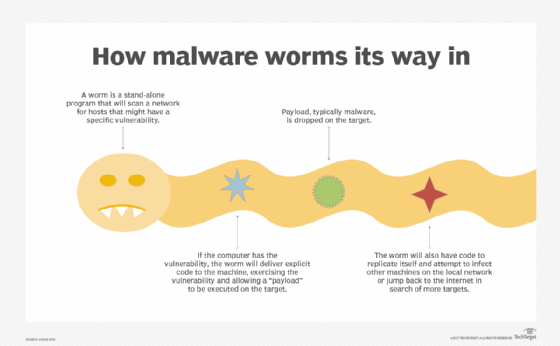
Logic bombs also pose some external malicious code threats. One example is WORM_SOHANAD.FM.
When an unsuspecting user downloads the worm from a malicious website, it installs additional malicious code files. It then creates a scheduled task using Windows Task Scheduler to execute the files sometime later.
How do time-triggered logic bombs and time-triggered trial software differ?
Some software applications come with a trial version, or trialware, offering users limited access for some specified period. When the time expires, the user can no longer access the trialware or use its premium features.
Thus, like a logic bomb, trialware also has a built-in logical condition. In this case, the condition is to disable access when X time period has passed.
But, unlike a logic bomb, a trialware's payload is known and is not malicious since it's not meant to cause harm but simply disable access to the free version of the paid software.
Examples of logic bombs
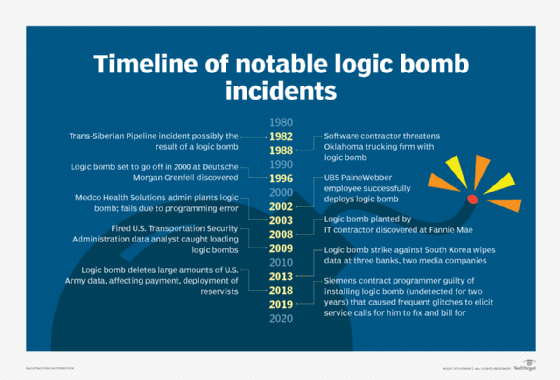
In the early 2000s, a disgruntled employee of UBS PaineWebber successfully deployed a logic bomb against his employer. His code ran the command /usr/sbin/mrm –r / &. This UNIX shell command recursively deletes the root partition, including files and subdirectories. It was triggered to go off on March 4, 2002, at 9:30 a.m. The logic bomb affected 2,000 company servers in 400 branch offices, preventing thousands of the company's brokers from executing trades. The employee was caught and sentenced to eight-plus years in federal prison.
In 2003, a system administrator at Medco feared being laid off. He installed a logic bomb designed to delete some data after he left the company. He was caught when he tried to fix his programming errors and was sentenced to 30 months in prison.
In 2019, a contract programmer for Siemens was found guilty of installing a logic bomb that caused frequent glitches in the system he designed in order to elicit service calls and bill the client for actioning them. He planted these logic bombs in the custom, automated spreadsheets he created, causing glitches like error messages and making onscreen buttons change sizes. The contractor "fixed" the issue -- and bilked his client for money -- by pushing back the date the spreadsheets would stop working. When caught, he was fined and incarcerated.
Logic bomb attacks are not new. As far back as 1982 and 1988, malicious individuals have launched such attacks to cripple an organization. The 1982 incident occurred during the Cold War between the U.S. and the former Soviet Union. In fact, this sabotage incident is widely considered the original logic bomb attack.
In 1988, a software contractor created a logic bomb following a disagreement with a client, an Oklahoma trucking firm; the contractor threatened to detonate the logic bomb unless the client paid its invoices. The case went to court. The client won.
Logic bombs have also affected the public sector. In 2018, the U.S. Army found itself on the wrong end of a logic bomb attack that deleted significant amounts of data and thus prevented Army reservists from being deployed and paid on time. The Army restored the data after spending more than $2.5 million to investigate the issue and repair its systems. The criminal received jail time and was ordered to pay $1.5 million in restitution.
How to safeguard against logic bombs
Organizations can prevent logic bombs by following some cybersecurity best practices:
- Use antivirus software, and update it regularly.
- Periodically scan all files, including compressed files and subdirectories.
- Require all users to activate security features like auto protect and email screening.
- Perform website safety checks, and avoid clicking on suspicious links.
- Avoid downloading email attachments from unknown/untrusted senders.
- Regularly update and patch operating systems.
- Train users on safety policies and best practices.