private key
What is a private key?
A private key, also known as a secret key, is a variable in cryptography that is used with an algorithm to encrypt and decrypt data. Secret keys should only be shared with the key's generator or parties authorized to decrypt the data. Private keys play an important role in symmetric cryptography, asymmetric cryptography and cryptocurrencies.
A private key is typically a long, randomly or pseudo-randomly generated sequence of bits that cannot be easily guessed. The complexity and length of the private key determine how easily an attacker can execute a brute-force attack, where they try out different keys until the right one is found.
How does a private key work?
Private key encryption is also referred to as symmetric encryption, where the same private key is used for both encryption and decryption. In this case, a private key works as follows:
- Generating a new private key. Prior to encryption, generate a new key that is as random as possible; encryption software is typically used to generate private keys.
- Securely storing the private key. Once generated, the private key must be stored securely. Depending on the application, keys may be stored offline or on the computer used to generate, encrypt and decrypt data. Private keys may be protected with a password, encrypted or hashed for security -- or all three.
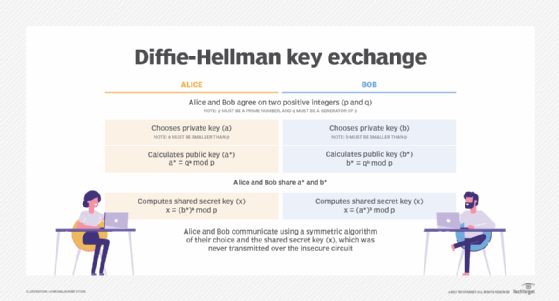
- Key exchange. The private key is used to decrypt, as well as to encrypt, so using it for symmetric encryption requires a key exchange to share that key securely with trusted parties authorized to exchange secured data. Cryptographic software is usually used to automate this process.
- Key management. Private key management is required to prevent any individual key from being used for too long. It helps to securely retire keys after their useful lifetime is reached.
A private key is also used in asymmetric cryptography, which is also known as public key cryptography. In this case, the private key refers to the secret key of a public key pair. In public key cryptography, the private key is used for encryption and digital signatures. It works as follows for asymmetric cryptography:
- Generating a public-private key pair. Randomness is even more important for this process. Encryption application software is usually used to generate key pairs. It should require a source of randomness, such as mouse movement.
- Securely storing the private key. Once generated, the private key must be stored securely. Like the symmetric cryptography process, keys may be stored offline or on the computer used to generate, encrypt and decrypt data. Here, too, private keys should be protected with a password, encrypted or hashed for security.
- Key exchange. The private key of a public key pair should almost never be shared with others. Public key cryptography, including digital signatures, is typically used to securely share session keys used for symmetric encryption. However, other protocols for public key infrastructure are used to authoritatively share public keys between cooperating parties.
- Using the private key. The owner of a public key pair uses their private key for decrypting data that has been encrypted with the public key of the pair. Only the holder of the private key should be able to decrypt data encrypted with the public key. For digital signatures, the owner of the key pair uses their private key to encrypt the signature. In this way, anyone with access to the public key can decrypt the signature and verify that it was signed by the private key owner.
- Key management. Public key pairs are often generated with expiration dates, and key management is vital to maintaining access to data protected with a key pair. For example, an expired public key certificate, which depends on a public key pair, may cause browsers to flag access to a website as insecure. Secret keys should be stored with the highest security, and public key pairs should be managed to avoid compromise or issues related to key pair expiration.
Advantages of private encryption keys
Private key encryption provides several useful features. They include the following four benefits:
- More secure. Private keys that are longer and have greater entropy, or randomness, are more secure from brute-force or dictionary attacks.
- Faster. Symmetric key encryption is faster computationally than asymmetric encryption with its public-private key pairs.
- Best for encryption. Most cryptographic processes use private key encryption to encrypt data transmissions. They typically use a public key algorithm to securely share secret keys.
- Work for stream and block ciphers. Secret key ciphers -- the algorithm for encrypting and decrypting data -- generally fall into one of two categories: stream ciphers or block ciphers. A block cipher applies a private key and algorithm to a block of data simultaneously, whereas a stream cipher applies the key and algorithm one bit at a time.
Challenges of private encryption key management
The security of encryption keys depends on choosing a strong encryption algorithm and maintaining high levels of operational security. Encryption key management is necessary for any organization using encryption to protect its data. That goes for symmetric, as well as asymmetric, encryption.
While private key encryption can ensure a high level of security, the following key management challenges must be considered:
- Overall management. Encryption key management is necessary to protect cryptographic keys from loss, corruption or unauthorized access.
- Continual updating. Private keys used to encrypt sensitive data should be changed regularly to minimize exposure should they be leaked or stolen.
- Recoverability and loss. If an encryption key becomes inaccessible, data encrypted with that key will be unrecoverable and lost.
Private keys vs. public keys
Asymmetric cryptography, also known as public key cryptography, uses pairs of public and private keys. These two different but mathematically linked keys are used to transform plaintext into encrypted ciphertext or encrypted text back to plaintext.
When the public key is used to encrypt ciphertext, that text can only be decrypted using the private key. This approach enables anyone with access to the public key to encrypt a message, and only the private key holder will be able to decrypt it.

When the private key is used to encrypt ciphertext, that text can be decrypted using the public key. That ciphertext can be a component of a digital signature and used to authenticate the signature. Only the holder of the private key could have encrypted ciphertext, so if the related public key successfully decrypts it, the digital signature is verified.
The public key is made available to everyone that needs it in a publicly accessible repository. The private key is confidential and should only be accessible to the public key pair owner. In this method, whatever is encrypted with the public key requires the related private key for decryption and vice versa. Public key encryption is typically used for securing communication channels, such as email.
Generating secure private keys
Private keys share the following characteristics with passwords:
- They must be kept secret to be secure.
- They restrict access to data (private keys) or resources (passwords).
- Their strength depends on their length and randomness.
While passwords are usually limited to characters accessible from a computer keyboard, cryptographic keys can consist of any string of bits. Such strings may be rendered in human-accessible character sets, if necessary. Length and randomness are two important factors in securing private keys.
Length
The length of a cryptographic key necessary to secure it against brute-force attacks depends on the encryption algorithm being used. As computers have become more powerful, cryptographic keys have grown longer to withstand brute-force attacks.
For example, early web browsers protected data with 40-bit keys; in 2015, the National Institute of Standards and Technology recommended a minimum key length of 2,048 bits for use with RSA, or Rivest-Shamir-Adleman, encryption.
Randomness
Just as important to the strength of a private key is its randomness.
Commercial software often relies on a pseudo-random number generator (PRNG) to generate private keys. However, PRNG output is not truly random and can be defeated by an attacker.
True random number generators require a source of physical entropy, such as a physical coin toss, roll of dice or unusual generators, like lava lamps. For example, the Pretty Good Privacy public key encryption program prompts users to generate entropy for a new public key pair by randomly moving their mouse.
Use of private keys in cryptocurrencies
Cryptocurrencies like bitcoin depend on cryptographic algorithms to generate, store and exchange digital value. Cryptocurrencies use public key cryptography for creating digital signatures that authenticate value transfers, as well as symmetric encryption to protect data exchanges.
While secret keys are used for symmetric encryption in cryptocurrency protocols, there is usually a public-private key pair assigned to the cryptocurrency owner to protect their ownership interests.
Cryptocurrency owners should store private keys securely because losing control or access to a private key means losing access to the cryptocurrency asset. Secure options for storing private keys include storing them on an isolated computer with no network connections, in hard copies that are physically secured or committed to memory.
The takeaway
As use of the public internet continues to expand for commercial, government and personal communication, so too does the need for securely using encryption to protect those exchanges.
Securing the private keys used to protect that data is the foundation of maintaining security in all types of communication.
Learn more about how end-to-end encryption works to keep data secure.






