
privileged access management (PAM)
What is privileged access management (PAM)?
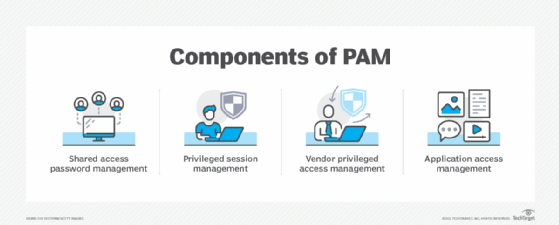
Privileged access management (PAM) is the combination of tools and technology used to secure, control and monitor access to an organization's critical information and resources. Subcategories of PAM include shared access password management, privileged session management, vendor privileged access management (VPAM) and application access management.
Privileged user accounts are significant targets for attack as they have elevated permissions, access to confidential information and the ability to change settings. If compromised, a large amount of damage could be done to organizational operations. Types of accounts that implement PAM can include emergency cybersecurity procedure, local administrative, Microsoft Active Directory, application or service, and domain administrative accounts.
Why is PAM important?
Implementing a PAM system helps organizations effectively monitor the entire network and provides insight into which users have access to what data.
A PAM system is one of the best ways for an organization to protect against external threats by preventing malicious parties from accessing sensitive corporate data through internal accounts.
PAM is critical because privileged accounts can pose major security risks to businesses. For example, a cybercriminal who compromises a standard user account will only have access to that specific user's information. But a hacker who compromises a privileged user account will have far greater access and possibly the power to destroy systems.
In addition to combating external attacks, PAM can help companies combat threats -- either malicious or inadvertent -- originating from employees and other internal people with access to corporate data.
PAM is also key to achieve compliance with industry and government regulations. With PAM as part of a complete security and risk management program, enterprises can record and log every activity related to their critical information technology (IT) infrastructures and sensitive corporate data, helping to simplify audit and compliance requirements.
PAM software and tools work by gathering the credentials of privileged accounts, also known as system administrator accounts, into a secure repository to isolate their use and log their activity. The separation is intended to lower the risk of admin credentials being stolen or misused. Some PAM platforms do not allow privileged users to choose their own passwords. Instead, the password manager of the platform will tell admins what the password is for a given day or issue one-time passwords each time an admin logs in.
PAM software features
Privileged access management is important for companies that are growing or have a large, complex IT system. Many popular vendors, such as BeyondTrust, Centrify, CyberArk, SecureLink and Thycotic, have begun offering enterprise PAM tools.
PAM tools and software typically provide the following features:
- multifactor authentication (MFA) for administrators;
- an access manager that stores permissions and privileged user information;
- a password vault that stores secured, privileged passwords;
- session tracking once privileged access is granted;
- dynamic authorization abilities -- for example, only granting access for specific periods of time;
- automated provisioning and deprovisioning to reduce insider threats; and
- audit logging tools that help organizations meet compliance.
Challenges of privileged access management
Companies may encounter some challenges when implementing and monitoring their PAM systems:
- Manage account credentials. Many IT shops use manual administrative processes prone to error in their function to rotate and update privileged credentials, making it an inefficient and expensive approach.
- Track privileged activity. Some organizations are unable to track and control privileged sessions from a central location, which can expose them to cybersecurity threats and compliance violations.
- Monitor and analyze threats. Many enterprises don't implement comprehensive tools to analyze threats, so they can't proactively uncover suspicious activities and mitigate security incidents.
- Control privileged user access. Companies often struggle to effectively control privileged user access to cloud platforms like infrastructure as a service, platform as a service, software-as-a-service applications and social media, which creates operational complexity and compliance risks.
- Balance security with ease of use. PAM tools should not only be highly secure, but also easy to use for IT admins. They should also enable admins to create accounts, grant and revoke access, and handle urgent situations, like user account, lockout as quickly and as easily as possible.
Vendor privileged access management
Vendor privileged access management is a subset of PAM that focuses on high-level external threats that come from an organization's reliance on external partners to support, maintain or troubleshoot certain technologies and systems. Representatives from these vendors require remote privileged access to an enterprise network in order to complete these tasks, thus posing a unique threat to IT management.
VPAM platforms are specifically built for managing the distinctive, high-stake threats that third-party vendors present. Third-party users complicate threat management as they are not tracked and managed in the same way as internal employees. Since employees working for vendors fall outside the control of their customers, companies may have little understanding about who they are, how they are using a company-provided login and when they are no longer working with the vendor. VPAM helps organizations control and monitor third parties' privileged access to critical applications and systems, while streamlining the management of all transient users, like vendors.
VPAM products provide three key areas of value to mitigate risks associated with third-party vendor access:
- Identification and authentication. Vendor access is difficult to manage because of both the lack of oversight and the potential number of users. Therefore, implementing MFA and vendor identity management techniques are critical. VPAM tools provide customized authentication options that can easily offboard and onboard users. This functionality prevents vendor reps that exit the company from taking their access with them.
- Access control. Once a user is authorized, permissions need to be granted. A VPAM solution gives network managers the ability to give access permissions and create an efficient working system to meet a desired set of requirements. For admins, access control can be as granular as individual accounts or as general as allowing access to an entire network application. They can also schedule access by supervised or unsupervised technicians at times convenient for monitoring, adding to the efficiency and security of an enterprise network.
- Recording and auditing. VPAM tools monitor user activity during every session and can document the exact who, what, where, when and why of any remote support session. An audit functionality within a VPAM platform also means that enterprise organizations can ensure vendor accountability and compliance with industry regulations.
PAM vs. identity management
PAM is often confused with identity and access management. While some overlap exists, PAM is only focused on accounts with privileged or administrative access, while identity management encompasses any users that require access to a system. Identity management provides organizations with a way to authenticate and authorize general access to employees, partners and customers.
To ensure the highest level of security and usability, companies should look into implementing both privileged access and identity management. Identity management systems cover larger attack surfaces within the organization's network, while PAM systems cover smaller, higher-valued attack surfaces.
Common privileged access management strategies
The following are strategies to help organizations ensure that their PAM implementations are effective:
- Keep an inventory of all privileged accounts and document any changes.
- Disallow admins from sharing accounts.
- Limit personal privileged accounts to one for each admin.
- Establish and enforce password policy for passwords.
- Change all the passwords on all company devices so users aren't using default passwords.
- Ensure that privileged account passwords change regularly to lessen the risk that employees who leave the company could compromise its systems.
- Secure privileged accounts with two-factor authentication.
- Limit permissions scope for all privileged accounts.
- Enforce separation of duties among employees.
- Enforce least privilege -- i.e., employees are only given the privileges they need to do their jobs.
- Apply best practices to elevate users who need extra access rights, such as documented request and approval processes.
- Use a variety of logging and monitoring tools and techniques to obtain a clear picture of the actions privileged users take.
- Update employees about changes in privileged access policies and procedures to ensure they understand how to correctly use and manage their privileged credentials.
- Document account management rules and processes, and require verification from company leaders.








