10 identity and access management tools to protect networks
IAM tools keep enterprises safe by ensuring only authorized users can access sensitive data and applications. Read this in-depth product overview of top tools on the market.
Modern identity and access management tools help IT security professionals centrally manage access to all applications and files for employees, customers, partners and other authorized groups. This IAM-provided management is scalable across the entire corporate infrastructure, including the corporate LAN, wireless LAN, WAN, and even into public and private clouds and edge computing points of presence. In many cases, IAM is a must-have for resources that fall under regulatory compliance rules.
Throughout the COVID-19 pandemic, IAM tools proved invaluable as employees operated either in a permanent work-from-home or hybrid work environment. The significant increase in remote workers combined with a lack of security visibility into end users and devices forced IT departments to heavily rely on the security features within IAM platforms to reduce the risk of data loss across applications.
The two most basic IAM processes required to secure access to digital assets are the following:
- Identify who it is that is trying to access resources by using authentication.
- Verify that identified users indeed should be authorized to reach the resource they are attempting to access.
At its core, this is the purpose of identity and access management. These platforms create a secure way to identify people or devices and then provide them with the appropriate access to digital resources.
The features and benefits of IAM don't end at identification and access control. Here is a list and brief description of common features found within IAM platforms today:
- User provisioning. These tools streamline the onboarding process of user account creation and the assignment of authorization roles that define what resources the user can access.
- Centralized access management. No matter where applications and data reside, IAM centralizes the management of those resources so admins can uniformly manage access and authorization controls across the entire infrastructure.
- Single sign-on (SSO). SSO is a series of processes that enables users to authenticate one time through a centralized portal and then have full access to the resources they're authorized to have without needing to undergo additional authentication steps. It accomplishes this by passing the singular granted authentication from system to system on an as-needed basis.
- Multifactor authentication (MFA). This is the use of more than one method to authenticate a user or device. MFA provides better assurance that authenticators are who they claim to be.
- User activity compliance/compliance control. This enables an organization to take advantage of the capabilities of IAM to help protect and identify activity risks regarding the privacy and protection of data that is under strict regulatory compliance rules.
- Identity governance. This is a policy-driven approach mandated by many regulatory compliance rules that requires the platform to demonstrate that it is handling identity and access management appropriately according to specific compliance requirements.
- Managed security. As companies grow, one of the biggest issues revolves around maintaining a scalable authentication and access control framework. IAM platforms achieve this in a centralized platform that is far easier to manage compared to siloed authentication and access control on a per-application or per-device basis.
- Access portal service. For large organizations, a self-service portal can save a tremendous number of man-hours. Employees and customers can use portals for self-registration, password resets, profile management, access requests and other similar tasks.
- API. While most IAM platforms provide pre-built integrations with hundreds or thousands of third-party applications to authenticate and grant access against, some businesses use legacy or custom-built applications that require a bit more work. In these cases, an API can create a custom front end to enable the application to authenticate and control access using IAM. The API gateway then funnels all API calls to the back-end IAM system so it can properly identify users and grant/deny access.
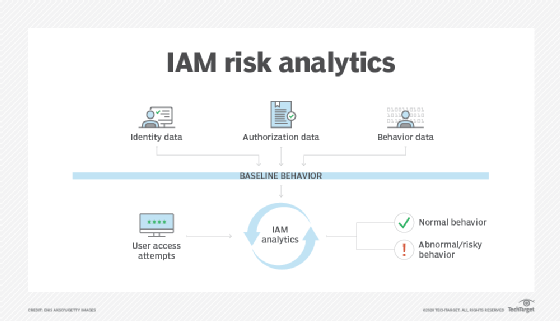
- Risk analytics. Some IAM platforms collect user authentication and access identity behavior over time. Additionally, relevant data, including end-user access location, time of day and the type of desired access, is also collected. Using AI, IAM can use this baseline information to spot anomalies in user behavior that can point to misuse or attacks. Triggers can be set up to either alert security admins or to outright block access until IT staff completes and clears further investigations.
Next, let's look at 10 of the top IAM vendors and products to provide a brief example of the available choices enterprise customers have and how products differ within the current IAM market space.
1. CyberArk
In early 2019, Centrify spun its IAM business out to form Idaptive, which was purchased by CyberArk one year later and rebranded as CyberArk Workforce Identity. This product offers a SaaS-based IAM platform, utilizes a zero-trust framework as a foundation and is available for cloud, on-premises or mobile applications and services.
CyberArk Workforce Identity integrates well with existing identity repositories that many small to large-sized organizations may already have, including Microsoft Active Directory (AD), Lightweight Directory Access Protocol (LDAP) and Google Workspace. Additionally, the platform uses an AI-backed form of MFA known as Adaptive MFA. This enables customers to use several secondary authentication methods, as well as AI, to monitor and potentially block access to mission-critical applications using behavior-based techniques.
This option is also notable for its cleanly designed dashboard, where admins can quickly identify things such as failing integrations, potential threats and other issues that IT admins should quickly address.
2. ForgeRock
In 2016, ForgeRock commercialized the popular open source OpenAM identity and access management platform and significantly expanded usability and management functions for enterprise environments. For IT professionals familiar with OpenAM or similar open source forks, ForgeRock's Identity Platform is a great option.
From a workforce IAM perspective, ForgeRock offers features like Intelligent Access, which personalizes authentication and access preferences at a granular level using a simplified drag-and-drop management interface. Intelligent Access also provides the option for self-service registration and credential resets that are directly integrated into the unified login experience.
Prospective buyers should note machine learning and AI capabilities set the product apart from many competitors. The AI function can help measure risk visibility and increase operational efficiencies by eliminating many management, incident and reporting processes that security admins previously had to perform manually.
3. IBM
IBM has transitioned from a PC, laptop and server hardware provider to a trailblazer in cloud/edge computing, AI and advanced analytics. Its Cloud IAM platform is a SaaS-based product that works for on-premises, cloud/edge and hybrid cloud architectures. Cloud IAM is a well-rounded offering that includes features such as the following:
- MFA
- SSO
- privileged access management
- identity governance
The product works well for both workforce- and customer-facing applications. Since IBM is well versed in AI, big data and deep analytics, Cloud IAM incorporates these advanced features into the product, which helps automate the modification of user access controls/limits and identify anomalous or risky levels of access.
4. Microsoft
Microsoft's AD is popular within enterprises to assist with authentication and access control within Windows domains. Azure IAM boasts thousands of pre-made, third-party application integrations that cover a range of business services, including the following:
- cloud storage
- management tools
- collaboration
- CRM
- e-commerce
- ERP
The product is also known for its open standard API, which enables creation of custom application and service integrations. Azure IAM is part of the larger Azure Security Center suite of tools. Thus, for organizations that use Microsoft Azure AD -- and, primarily, for off-the-shelf businesses that have pre-integrated hooks into the Azure platform -- it's a solid choice.
5. Okta
A pure-play vendor, Okta is considered a pioneer in the SaaS-based IAM market. As a vendor-neutral platform, it can function well, regardless of the types of underlying infrastructure technologies in use. While Okta is most known for customer IAM, it is building a solid workforce IAM market base as well for both enterprise cloud and hybrid cloud environments. The Okta universal user/group/device directory can pull data from several directory sources.
The platform also includes Okta Access Gateway, an application to securely authenticate users and allow access to on-premises applications without the need for remote access VPN connectivity.
Lastly, the Okta ThreatInsight feature blocklists known malicious IP addresses that attempt to steal credentials, while rate limiting other sources to prevent distributed denial-of-service attacks.
6. OneLogin
The OneLogin Workforce Identity platform is a solid option for enterprise organizations that need to synchronize users and groups located in multiple directories, including AD, LDAP, Workday and Google Workspace. Admins can reference and push user attributes to downstream applications for access purposes through the use of Security Assertion Markup Language or via an API.
OneLogin includes an AI-backed adaptive authentication mechanism called SmartFactor Authentication, which gives the IAM platform more intelligence when authenticating users and devices compared to traditional static rules. One of the ways that intelligence integrates into SmartFactor is the use of Vigilance AI Threat Engine. The engine continuously scans both first- and third-party sources with the purpose of identifying potential authentication-focused threats.
7. Oracle
Existing Oracle customers will likely gravitate to Oracle's Identity Cloud Service platform for their IAM needs. Identity Cloud Service is ideal for hybrid cloud architectures and especially useful for managing identity and access in multi-tenant scenarios. The platform's customizable user portal is great for businesses that want to offload simple tasks to end users through an easy-to-use, self-service website.
Oracle Identity Cloud Service also touts a highly extensive API to integrate custom applications that don't already have pre-built integrations.
Lastly, Oracle continues to work on the overall performance of the platform, making it one of the most reliable and fastest platforms on the market.
8. Ping Identity
As another pure-play vendor, Ping is well known in the IAM space and is a trailblazer in SSO and MFA. In fact, it's widely known that Ping is the only vendor Microsoft tapped to offer the use of identity services within the Microsoft Azure AD Premium offering. Ping Identity is available in several different package offerings, depending on whether businesses require IAM services for internal employees, external customers or a combination of the two.
Ping also offers several useful turnkey cointegrated systems for companies that have specific IAM needs. Some turnkey platform examples include IAM for Microsoft AD Federation Services, AWS, Google Cloud, Zscaler Internet Access and Zoom.
9. RSA
Whether an environment is on premises, hybrid cloud or fully SaaS, RSA SecurID Suite is a good all-around choice as the platform offers flexible deployment options. This is especially true if MFA flexibility is necessary for an enterprise. This product also checks all the necessary feature boxes for larger organizations, such as the following:
- SSO
- identity and lifecycle management
- identity governance
The RSA Ready program is a technology partner portal that enables third-party software vendors to offer integrations of their products into SecurID Suite. Currently, the program consists of over 500 software partners with more than 1,000 RSA-certified integrations.
Also, keep in mind that RSA is a subsidiary of Dell EMC. Thus, for businesses that are already heavily invested in other Dell EMC or RSA technologies, choosing RSA SecurID Suite makes sense from an integration and support standpoint.
10. SailPoint
SailPoint is another pure-play IAM provider. It's also one of the smaller companies on this list. Yet, what it lacks in size, it makes up for in IAM functionality and overall flexibility to operate within any enterprise architecture. The company claims that its IdentityIQ platform enables businesses to connect, on average, up to 99% of all current applications and data using simplified integration wizards and pre-configured workflows.
Another notable detail is that customers can separate the core IAM features from their more advanced, AI-driven analytics components. The AI portion of the product is known as Predictive Identity. Customers can choose to purchase Predictive Identity and integrate it with the other parts of IdentityIQ immediately or opt to add this capability later or not at all.
This is a great model for those companies that may not currently have the in-house staff to properly manage the analytics side of the product but wish to enable it sometime in the future.








