Top zero-trust certifications and training courses
Most organizations are expected to implement zero trust in the next few years. Learn about zero-trust certifications and trainings that can help prepare your security team.
Traditional approaches to security historically included perimeter-based defenses and an implicit trust of network insiders. Zero trust, a wholly different approach to security, treats all users and resources, wherever they are located, as equally untrusted.
Sixty percent of organizations will embrace zero trust by 2025, according to Gartner. To assist with these changes, organizations will need all hands on deck -- and that may require zero-trust certifications and training.
Understanding zero trust
Before IT and security teams can start implementing a zero-trust model, they'll need to convince other departments -- which are likely less security-conscious -- about the importance and benefits of this approach. A zero-trust team stretches across IT functions, from security, networking, applications and data to finance, HR and C-suite executives.
To get started, IT and security professionals need to learn how to communicate what a zero-trust strategy is and why it's important to the business. But be aware: The real benefits can quickly get mixed up in vendor hype and marketing jargon.
Equipped with the right training, business and IT leaders will be able to make smart decisions about how zero trust can fit into their organization. They might even be surprised by what already exists in their enterprise that can foster zero-trust security. Organizations likely already use zero-trust principles in their data loss prevention, endpoint security and identity and access management programs.
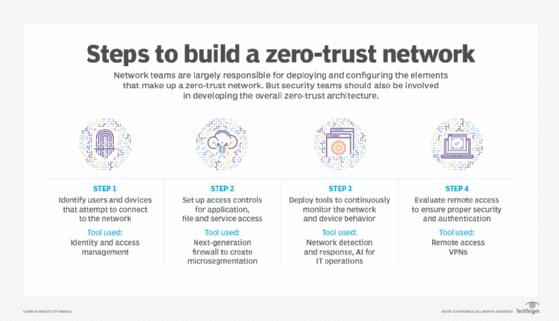
Zero-trust certification and training programs
Organizations can invest in zero-trust training and certification programs to ensure not only knowledge of zero trust, but also that the cross-functional team can speak the same language and collaborate on a comprehensive, enterprise-wide strategy.
Let's look at the top zero-trust certifications and training courses, ranging from beginner to intermediate, available for security practitioners and business professionals.
1. Forrester's Adopting Zero Trust certification course
Forrester's Adopting Zero Trust on-demand course is cohort-based and runs for 60 days. Attendees are invited to a live orientation session and encouraged to participate in discussions throughout the duration of the course. It is best suited for experienced technologists and priced at $2,260 per person.
The course is also included in Forrester's Technology Executives and Security & Risk services.
The following six modules are included in Forrester's Adopting Zero Trust course:
- The Zero Trust eXtended Framework
- Five Steps to a Zero-Trust Network
- The Business Case for Zero Trust
- Supporting Zero Trust
- Leading Change
- Maturing Zero Trust
Professionals who complete the course and pass a final online exam will receive a certificate and badge recognizing their skills and knowledge.
2. Cybrary's Zero Trust Networks training course
In Cybrary's Zero Trust Networks training course, students will learn the fundamentals necessary to securely manage trust of users, devices, applications and network traffic. This beginner-level training covers the principles of zero trust, in addition to best practices for implementing enterprise-scale zero trust.
While the course has no prerequisites, Cybrary recommends students have a prior understanding of perimeter firewalls, traditional network security architecture, public key infrastructure and network zones.
The course can be accessed with a Cybrary subscription. Upon completing all components of the three modules -- which typically takes one hour and 17 minutes -- participants will receive two continuing professional education (CPE)/continuing education unit credits and a certificate of completion.
3. Pluralsight's Zero Trust trainings
Pluralsight offers several prerecorded beginner and intermediate zero-trust trainings:
- Zero Trust Architecture: Executive Briefing
- Zero Trust Architecture: Getting Started
- Zero Trust Architecture: Use Case Identification and Implementation
- Zero Trust Architecture: Strategize and Establish
- Zero Trust Networking: The Big Picture
The courses are instructed by Pluralsight's authors Matt Conran, an independent networking and security consultant at Network Insight, and Lyron Andrews, a cybersecurity advisor at Profabula and former (ISC)2 authorized trainer. All courses can be accessed with a Pluralsight membership, which costs $29 per month.
4. (ISC)2's Preparing for a Zero Trust Initiative training course
(ISC)2's Preparing for a Zero Trust Initiative examines the principles of zero trust. The course covers threat scenarios, reference architectures and policy governance frameworks, and is designed for professionals with a background in computer science or cybersecurity who have a basic understanding of zero trust.
The online, self-paced course is comprised of three modules:
- Foundations in Zero Trust Architecture
- Creating a Zero Trust Strategy
- Implementing Zero Trust Architectures
Participants receive a certificate of completion and earn two CPE credits if they receive a score of 70% or higher on the course's final assessment. The course is free for (ISC)2 members and $80 for nonmembers.
5. SANS SEC530: Defensible Security Architecture and Engineering: Implementing Zero Trust for the Hybrid Enterprise
SANS SEC530: Defensible Security Architecture and Engineering: Implementing Zero Trust for the Hybrid Enterprise teaches students how to build and maintain a security architecture, as well as how to implement zero-trust principles across hybrid environments.
The six-day course is offered in person, remotely or on demand, and is designed for students pursuing GIAC Defensible Security Architecture certification.
The syllabus includes the following modules:
- Defensible Security Architecture and Engineering: A Journey Towards Zero Trust
- Network Security Architecture and Engineering
- Network-Centric Application Security Architecture
- Data-Centric Application Security Architecture
- Zero-Trust Architecture: Addressing the Adversaries Already in Our Networks
- Hands-On Secure the Flag Challenge
Students who complete the course will receive 36 CPEs. Costs include $8,275 for the course, $949 for GDSA certification and an additional $949 for the optional on-demand bundle that allows students to review the course materials for an additional four months.
6. Udacity's Zero Trust Security course
Udacity's Zero Trust Security course covers the foundational capabilities, principles and requirements that constitute a zero-trust architecture. Students should be familiar with basic cybersecurity concepts and practices before attempting this course.
The self-paced training, which typically takes one month to complete at an average of five to 10 hours per week of study time, includes real-world projects from industry experts, technical mentor support and quizzes to test your knowledge. The program has a pay-as-you-go offering, priced at $399 per month.
7. Udemy's Zero Trust Networks Online Training Course
Udemy's Zero Trust Networks is a two-hour on-demand course that teaches professionals the steps involved in establishing a zero-trust architecture, including the following:
- the basics of zero trust;
- implementation challenges;
- NIST guidance on building zero trust;
- steps for building a zero-trust network;
- conditional access policies; and
- zero-trust use cases.
The course is designed for security managers, consultants, CISOs, CIOs, and cybersecurity and network engineers. It costs around $20 and participants receive a certificate upon completion.
8. CSA's Zero Trust Advancement Center
The Cloud Security Alliance, a leading nonprofit research organization, in early 2022 launched the Zero Trust Advancement Center in partnership with CrowdStrike, Okta and Zscaler.
Currently consisting of zero-trust research resources, presentations and webinars, the initiative is to soon include an annual Zero Trust Summit and a new certification: the Certificate of Zero Trust Knowledge.
Stay tuned here and check out CSA's website for the latest updates on this initiative.
9. Cprime's Zero Trust Security Boot Camp
Cprime's Zero Trust Security Boot Camp is a course that teaches participants about the foundations of zero trust. Designed for security administrators, engineers, product managers, CIOs and CSOs, professionals will learn the following skills:
- how to implement zero-trust tenets and concepts;
- how to design zero-trust networks;
- how to assess an organization's readiness for zero trust; and
- how to mature zero-trust implementation.
The course, priced at $1,695, is currently only available for private sessions. Cprime plans to start offering the course to the public starting in 2023.
10. LinkedIn Learning's Understanding Zero Trust
LinkedIn Learning's Understanding Zero Trust is an intro-level course that examines the principles and models of zero trust. It consists of three parts:
- Background, which includes the history of technology trust;
- Zero Trust, which includes the basics of zero trust; and
- Implementing Zero trust, which includes designing a policy engine.
The course is led by Malcolm Shore, cybersecurity expert and former director of New Zealand's Government Communications Security Bureau. The program is included with a LinkedIn Learning membership, which costs around $39.99/month if paid monthly or $19.99/month paid annually. Participants receive a certificate upon completion.
Vendor trainings
As zero-trust adoption increases, vendors have begun releasing their own vendor-specific trainings, such as the following:
- Microsoft's "Explore the Zero Trust security model" module explains zero trust and how it applies to Microsoft 365.
- Cisco's Zero Trust Workshops hub offers two virtual options: "Strategy and Planning" and "Implement and Execute."
- Fortinet: Zero Trust Access curriculum has multiple zero-trust courses, including FortiGate Security, Secure Wireless LAN and Secure Access.
- Zscaler Academy offers five zero-trust certifications: Zscaler Internet Access Administrator, ZIA Professional, Zscaler Private Access Administrator, ZPA Professional and Zscaler Digital Experience Administrator.







