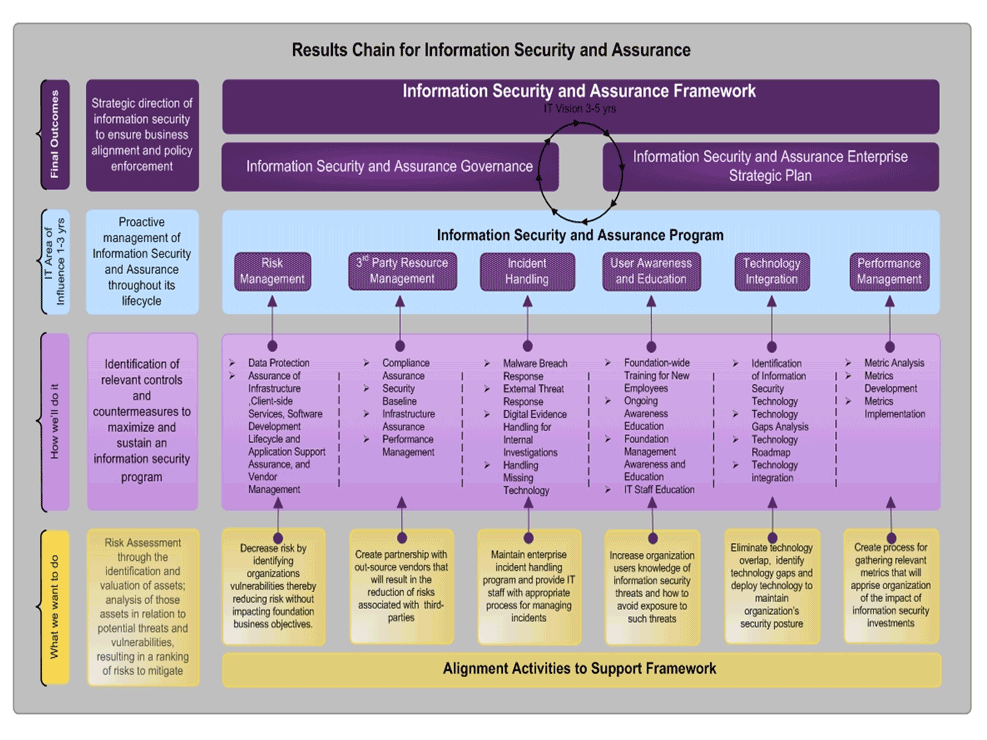
Results Chain for Information Security and Assurance
Based on the information gathered in your security blueprint, you can develop the results chain model here to build a framework that will allow you to clearly identify and present the actions that will be taken to achieve an outcome.