Pretty Good Privacy (PGP)
What is Pretty Good Privacy (PGP)?
Pretty Good Privacy or PGP was a popular program used to encrypt and decrypt email over the internet, as well as authenticate messages with digital signatures and encrypted stored files. PGP now commonly refers to any encryption program or application that implements the OpenPGP public key cryptography standard.
PGP was initially brought out as freeware and later as a low-cost commercial product. First published by Philip R. Zimmermann in 1991, it was once the most used privacy program and a de facto email encryption standard.
The original freeware and commercial versions of PGP are no longer available. Ownership of the program shifted several times before its eventual demise. Zimmerman originally owned PGP, and later PGP Inc., the company he founded to market PGP, took over ownership. Network Associates Inc. (NAI) acquired PGP Inc. in 1997. Other companies that have marketed some or all of the PGP technologies include the following:
- Broadcom
- Intel
- McAfee Associates
- PGP Corp.
- Symantec
- Townsend Security
While it may no longer be simple to acquire a new copy of the original PGP program, the Internet Engineering Task Force (IETF) has published PGP protocols as internet standards since 1996. Both open source and commercial implementations of the OpenPGP protocol are widely available. The GNU Privacy Guard (GPG) implementation is published under the GNU Public License (GPL).
In 2015, it was reported that Zimmermann no longer used PGP because working versions were not available for any of his devices.
The Pretty Good Privacy trademark was abandoned as of April 2020. Implementations of the OpenPGP specification now often refer to their implementations of the protocol as Pretty Good Privacy or simply PGP.
How does PGP work?
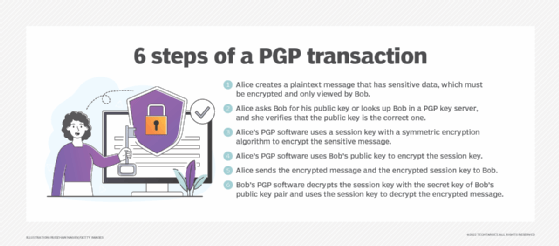
Pretty Good Privacy uses a variation of the public key system. In this system, each user has an encryption key that is publicly known and a secret or private key that is known only to that user. Users encrypt a message they send to someone else using that person's public PGP key. When the recipient receives the message, they decrypt it using their private key.
Encrypting an entire message using public key encryption can consume excessive amounts of resources. As a result, PGP uses a symmetric key encryption algorithm to encrypt the message and then uses the public key to encrypt that symmetric encryption key. Both the encrypted message and the encrypted symmetric encryption key are sent to the recipient, who first uses their private key to decrypt the short key and then uses that key to decrypt the message.
The original PGP program was offered in two versions, one using the Rivest-Shamir-Adleman (RSA) algorithm for key exchange, and one using the Diffie-Hellman algorithm for key exchange. PGP was required to pay a license fee to RSA for the RSA version. That version used the International Data Encryption Algorithm to generate a short key for the entire message and RSA to encrypt the short key. The Diffie-Hellman version used the CAST algorithm for the short key to encrypt the message and the Diffie-Hellman algorithm to encrypt the short key.
When sending digital signatures, PGP uses an efficient algorithm that generates a hash (a mathematical summary) from the user's name and other signature information. This hash code is then encrypted with the sender's private key. The receiver uses the sender's public key to decrypt the hash code. If it matches the hash code sent as the digital signature for the message, the receiver is sure that the message has arrived securely from the stated sender. PGP's RSA version used the MD5 algorithm to generate the hash code. PGP's Diffie-Hellman version used the SHA-1 algorithm to generate the hash code; neither of those hashing algorithms is considered secure today.
How to get PGP
To get a Pretty Good Privacy program, users must download or buy it and install it on their computer system. It typically contains a user interface that works with the user's email program. The public key that the PGP program provides must be registered with a PGP public-key server so that people exchanging messages with the user will be able to find it.
PGP software that supports the OpenPGP protocol can be a standalone application like GPG, or it may be a front-end interface, applet or plugin implementing the protocol. In most cases, PGP software is packaged as part of an email client or web browser.
PGP concepts
PGP depends on some concepts that enable users to easily access and share public keys, and to transmit cryptographic information across networks and systems. Important terms include the following:
- Alice and Bob are names assigned to generic actors in cryptographic processes. Alice, Bob and other generic actor names are often used when illustrating cryptographic exchanges like those used by PGP.
- Web of trust is a concept used to describe the way trust is established in public keys. A PGP user can try to establish trust directly with every key holder they interact with. In those cases where trust is established, they may also be willing to sign those keys to signify that they have authenticated the key pair and its holder. The PGP user can also accept trust in key holders that certain other PGP users have already signed to indicate they are trustworthy. If Alice accepts that Bob is sufficiently trustworthy in how carefully he vets the public keys he accepts as authenticated, then Alice can also trust those other public keys that Bob trusts.
- Implicit trust is one of the two different types of trust that can be established through the web of trust. Implicit trust is used when Alice signs Bob's public key pair. This indicates that Alice has vetted Bob -- and his private and public keys and his email address -- and is willing to assert (through her own signature) that she found Bob to be who he says he is and that the email and key pair are under Bob's control.
- Explicit trust is the other type of trust established through the web of trust. It occurs when Carlos, a third generic user, is willing to trust Alice's judgement about other individuals whose keys she has signed. Carlos can use explicit trust in Alice to accept that Bob's public key pair is also valid.
- Key signing is the PGP function that enables one person to announce that they have verified the person who claims to own the public key pair. PGP creator Zimmermann stresses verifying the following:
- The key you are signing should be verified as controlled by the person who claims it.
- The identity of the key holder should be verified with at least one form of photo ID. Even friends or coworkers should be formally identified if you have never previously seen that person's ID.
- Email and private key ownership should be verified. The email address in the signed key should be verified as the correct one for the person claiming the key pair.
- ASCII armor, also known as Radix-64 encoding, is a way of formatting encrypted data in a printable format. PGP uses ASCII armor to format data in a way that resists the introduction of errors through different computer formats as the data transits the internet. ASCII armor uses only ASCII characters and header and footer blocks to identify the start and finish of the armored data.
- Session key is a symmetric encryption key used for just one encryption session.
What is PGP used for?
There are two main reasons to use PGP.
- Encryption. PGP enables encryption of sensitive information or data whether it is a file, email or message. A PGP user can secure data through encryption, in a format that is easily transmitted but that can only be decrypted with the recipient's secret key.
- Authentication. PGP enables digital signing of a message, file or email -- whether encrypted or not. The recipient uses the signer's public key to authenticate the digital signature.
More specifically, PGP software enables users to do all basic PGP transactions, including the following functions:
- creating a PGP public key pair;
- revoking a PGP public key pair, so that others will no longer use it;
- key server functions, like specifying a default key server and registering key pairs;
- encrypting a message or file;
- decrypting a message or file;
- digitally signing a message or file;
- authenticating a digital signature;
- signing a public key; and
- key management.
Different OpenPGP implementations have different -- but similar -- processes for each of these functions.
PGP is used mostly to encrypt or digitally sign emails, though it can also be used to do the following:
- Encrypt and digitally sign transmissions in messaging applications. PGP has been implemented as an applet or an add-on to messaging applications. The basic GPG implementation operates at the command line, but numerous projects and some products act as a graphical user interface (GUI) front end for GPG.
- Encrypt and digitally sign disk drives. Depending on the OS, PGP-based applications are available for encrypting disk volumes.
- Scripts and application programming interfaces (API)s for programming with PGP. Developers can use scripts of cryptographic processes. Many of these common but complicated scripts are available online. Users can also develop their own scripts or use APIs to integrate PGP support into their customized applications.
PGP's challenges
PGP's success was largely a result of offering early users access to strong cryptography with little or no investment in software licenses. However, implementing and using PGP can be challenging for the following reasons:
- Usability. PGP implementations tend to be difficult to use, whether at the command line or in a GUI.
- Conceptual complexity. New users often have difficulty understanding key PGP concepts and processes.
- Decentralized infrastructure. Using a web of trust can pose a problem when there are not enough participants in the larger general population.
While most users do not use PGP, there is still enough of a user base to fuel continued development of OpenPGP-compliant implementations and related applications.
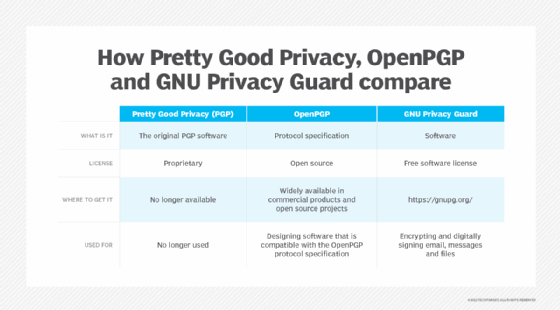
PGP vs. OpenPGP and GNU Privacy Guard
Although originally conceived of as proprietary software, PGP became popular with computer professionals and organizations in the 1990s. After being published as an information standard in 1996, PGP was renamed OpenPGP and moved to the IETF standards track in 1998.
There is still confusion about the term PGP, which until recently was used to refer to the freeware and commercial programs first developed by Zimmermann. It is now more commonly used to describe any software that supports the OpenPGP protocol specification.
GPG was one of the first OpenPGP implementations. It is an open source version of PGP published under GPL.
History of PGP
1991. Zimmermann releases the first version of PGP.
1993. U.S. Customs Service launches an investigation of Zimmermann for allegedly exporting munitions -- strong encryption software -- without a license.
1995. To gain protection from prosecution for exporting PGP, Zimmermann publishes all PGP source code in book form.
1996. Customs Service ends criminal investigation of Zimmermann without filing any charges.
1996. IETF publishes PGP Message Exchange Formats (RFC 1991) as an informational protocol.
1997. First public release (version 0.0.0) of the GPG program comes out.
1997. Entirely updated version of PGP, initially referred to as PGP 3, is published. Because the then-current version of PGP was 4, the new update was released as PGP 5.
1997. NAI acquires PGP Inc. Zimmermann and the PGP team are hired as NAI employees.
1999. First production release (version 1.0.0) of the GPG program.
2000. Cryptography software vendor Townsend Security partners with NAI and develops a mainframe version of PGP. That version is still available for IBM mainframes.
2002. NAI announces it will no longer work on PGP and offers its PGP assets for sale -- except for the E-Business Server product.
2002. PGP Corp., formed by former PGP team members, purchases PGP assets from NAI. The new corporation picks up support for existing PGP customers, as well as offering updated and new products in the line.
2007. IETF publishes OpenPGP Message Format (RFC 4880), a revised standards track specification.
2010. Symantec acquires PGP Corp., which held the rights to the PGP code, and soon stops offering the freeware version of the technology.
2010. Intel acquires McAfee (formerly NAI) and its McAfee E-Business Server product. 2013. Intel passes McAfee E-Business Server to Software Diversified Services, an enterprise mainframe software vendor.
PGP has long been the standard for encrypting and digitally signing messages, but it's not the only tool available for securing email. Find out more about the most important email security protocols.







