
Why ransomware attacks on municipalities spiked in 2019
Ransomware spread to a number of city, state and local governments across the U.S. in 2019. Threat researchers weigh in on the increased attacks and what to expect in 2020.
The scourge of ransomware attacks that devastated U.S. city, state and municipal governments in 2019 was so bad that some to were forced to close, while others declared a state of emergency.
Several security vendors reported a dramatic increase in ransomware attacks on public sector networks last year. According to a recent report from Kaspersky Lab, titled "Story of the year 2019: Cities under ransomware siege," 174 municipal organizations were infected with ransomware last year, "an approximate 60% increase from the number of cities and towns that reported falling victim to attacks one year earlier." The information is based on publicly available statistics and announcements monitored by Kaspersky experts.
Kaspersky calculated that educational organizations accounted for 61% of cases and city halls and municipal centers ranked second at 29%.
Check Point Software Technologies saw a similar trend. According to Check Point Research's 2020 Cyber Security Report, "U.S. municipalities were a popular choice in the public sector" for ransomware attacks last year.
"Ransomware distribution has shifted from a numbers game to a more targeted approach of 'big game hunting' where advanced threat actors find or buy their way into specific target organizations," the report said. "This has enabled them to encrypt vital infrastructures and demand high ransom payments."
Lotem Finkelstein, head of threat intelligence at Checkpoint, said his company observed several trends throughout the year involving ransomware, the most notable of which was cooperation between different cybercriminal groups seeking to spread infections.
"Not long ago, the Department of Homeland Security report warned organizations to be more careful with infections of Emotet because this is the trigger for more dangerous infections," Finkelstein said. "We saw an alliance between two or three cybercriminals where one delivers Emotet, one delivers Trickbot and the other delivers Ryuk [ransomware]."
Although cybercriminals do not necessarily know which organizations or companies they are infiltrating beforehand, Finkelstein observed a trend of U.S. city, state and even federal governments being more targeted than others.
Matt Olney, director of threat intelligence at Cisco Talos, attributed security inadequacy as one reason behind the increase in ransomware attacks on municipalities.
"When you're on a town or municipal or county level, you're not always equipped with the top security talent, capabilities or components," Olney said. "Threat actors are looking for easy access using the tools they already have."
Notable attacks in 2019
Finkelstein said the trend of municipality strikes started with the SamSam ransomware attack on Atlanta in 2018; the trend intensified last year, with a slew of attacks on one government network after another.
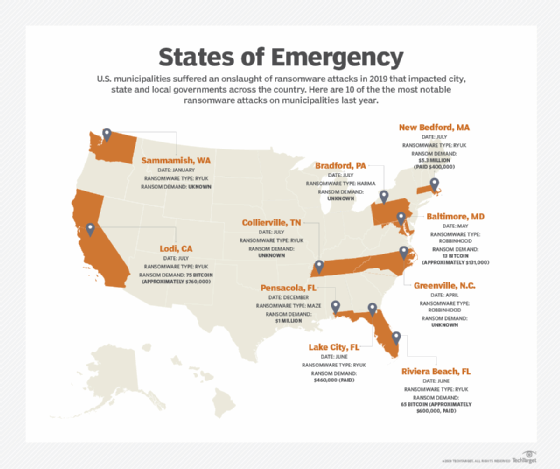
In March, New York's state capital was hit with an attack that affected some of Albany's services and sensitive data. In April, another capital was hit when the Augusta, Maine city network was knocked offline.
One month later, Baltimore suffered one of the year's most significant attacks. According to Kaspersky, threat actors deployed RobbinHood ransomware then demanded a bitcoin bounty equal to around $114,000, which the city refused to pay. The repercussion: they paid handsomely in recovery costs, which soared upward of $18 million.
New Bedford, Massachusetts, after being infected with Ryuk in July, was threatened with one of the largest known ransom demands ever: $5.3 million.
Some attacks caused so much disruption that governments were forced to take drastic actions. After New Orleans was hit in December, the city's mayor declared a state of emergency.
In August, the state of Texas was victimized in a coordinated attack where 22 municipalities were hit simultaneously; most of the targets were local governments that were connected through a single managed service provider (MSP) that was using ConnectWise Control, a remote access tool.
Multiple cities in Florida suffered attacks as well, including Stuart City and Pensacola, which faced a $1 million ransom demand. Two Florida cities eventually decided to pay the ransoms: Riviera Beach ($600,000) and Lake City (around $500,000).
In July, 225 U.S. mayors banned together in a resolution to stop paying the ransom.
But threat actors are evolving, as evident in the first months of 2020. Now, leaders have the added pressure of data exposure on top of data encryption, a rising trend in this complex threat landscape.
Targeting tactics
Fedor Sinitsyn, senior malware analyst at Kaspersky, said different threat actors have varying strategies when choosing their victims.
"A more sophisticated strategy, which is currently popular among the top criminal groups, requires manual involvement of a skilled operator. A group infects several random victims with a remote access Trojan, then the operator manually carries out reconnaissance in the infected system. If the actor discovers that the compromised PC is a part of a large network, they will try to gain privileges and infiltrate other nodes and the domain controller. At this point, the criminals will most likely be aware of what organization they have compromised."
Choosing the victim in advance and carrying out a targeted attack may prove more profitable for the threat actors, said Sinitsyn. Compromising the network of a managed service provider is one way to achieve that, he said.
Finkelstein agreed that MSPs are a common target.
"The targeted ransomware trend is the same as what we call a 'one stop before the target' trend. Even though one organization is victimized, they may just be one stop before the main attack, which is the case with MSPs. They are usually a trusted organization, and no one suspects they would compromise their customers," he said.
Proofpoint's 'State of the Phish' report also confirmed that "many recent high-profile ransomware attacks appear to be secondary infections in organizations already compromised with other malware." Gretel Egan, security awareness and training strategist at Proofpoint, told SearchSecurity her company saw fewer ransomware payloads deliver directly via phishing emails; instead, threat actors gained access to networks with other types of malware and, after moving laterally through the environment, deployed their ransomware.
In some cases, additional malware was used for more than just the intrusion, accord to Sinitsyn. "Sometimes, threat actors introduce an additional feature into their Trojan that allows them to count the number of encrypted files and the total size of encrypted data per victim. In that case, the ransom will be calculated automatically based on these numbers," he said.
Other factors were apparently involved in how threat actors came up with specific ransom demands. For example, Kaspersky's report found the average ransom ranged from "$5,000 to $5,000,000, with the numbers varying greatly, as the funds extorted from small town districts were sometimes 20 times smaller than those extorted from city halls in big municipalities."
Ransomware response
According to Proofpoint's 'State of the Phish', 51% of U.S. organizations surveyed opted to pay threat actors after being hit with a successful ransomware attack. But many major cities and large municipalities have pledged not to pay threat actors in such attacks.
According to Kaspersky's report, "the cybersecurity budgeting of municipalities is often more focused on insurance and emergency response than on proactive defense measures."
With all the benefits of cyber insurance, there are downfalls as well.
"The insured organization may choose to invest less into their network defenses, security audit and employee training, which might increase the probability of a security breach," Sinitsyn said. "Secondly, in case of a ransomware infection, the insurance company may be forced to pay the ransom to the threat actors, which promotes this type of malicious activity."
Mandy Stanton, a cybersecurity, privacy and data protection attorney with law firm Mitchell Williams, said state, city and local governments should heed 2019's wake-up call. "It's definitely time to make a strategic change and prioritize cybersecurity."
Stanton said her clients often seek advice in anticipation of a ransomware attack, and she preaches preparation.
"Attackers know cities are often a compartmentalized organization, so a proactive security strategy should include enterprise-wide stakeholders that represent all the common points of entry for an attacker," she said. "Cities' public-sector bureaucracy, multiple departments and different policies and technology platforms cause a fractured organizational structure and lead to slower deployment of security measures, making it easy for attackers to take advantage of them. If a city determines to work with outside partners in a crisis event, then it needs to start building those relationships now."






