
Maksim Kabakou - Fotolia
Zero-day flaw in Sophos XG Firewall exploited in attacks
Sophos released an emergency patch over the weekend for its XG firewalls after threat actors exploited a zero-day SQL vulnerability in the products to steal customer data.
Sophos issued an emergency patch Saturday to fix a zero-day vulnerability that was exploited in the wild.
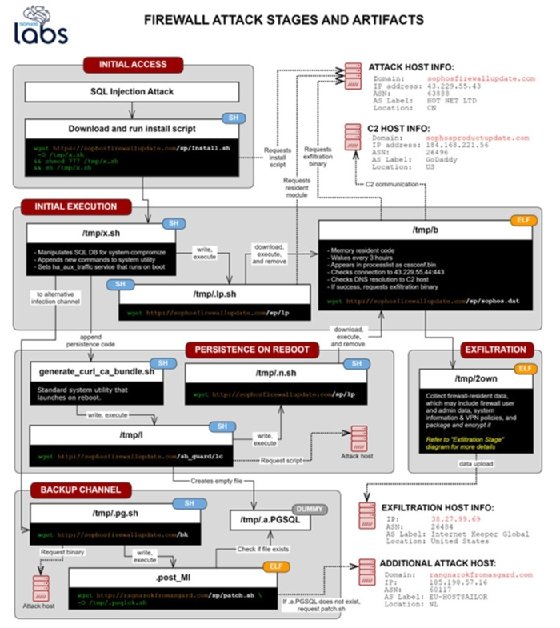
Threat actors had abused a previously-unknown SQL injection vulnerability in the Sophos XG Firewall product, which allowed remote code execution. In a detailed report of the attack published Sunday, Sophos said the attack involved "significant orchestration" by unidentified adversaries that was designed to deliver a new, customized Trojan the vendor dubbed "Asnarök," after a malicious domain -- ragnarokfromasgard.com -- used in the attack.
According to Sophos, the attack began on April 22; approximately four hours after the attack began, the vendor received a report about a suspicious field value visible in the Sophos XG Firewall management interface (Sophos did not disclose where the initial report originated). Sophos' internal security team began investigating the incident and quickly blocked suspicious domains that were discovered in the initial forensic review.
The attack on the XG firewall involved "a chain of Linux shell scripts" that eventually downloaded the Asnarök Trojan, which was developed specifically for the firewall operating system, according to Sophos. The attack chain began with an injected command from a remote server hosting the malicious domain sophosfirewallupdate.com; other malicious domains and IP addresses, including sophosproductupdate.com, were used to download additional malware installers and modules and exfiltrate data.
"This attack targeted Sophos products and apparently was intended to steal sensitive information from the firewall," Sophos wrote in the incident report.
Sophos said analysis of the malware showed it was only capable of stealing only firewall resident information, which may have included the product's license and serial number; firewall users' names, usernames and encrypted passwords; the salted hash of the administrator account's password; email addresses of user accounts and the administrator that were stored on the device; user IDs permitted to use the firewall for SSL VPN connections; and accounts approved to use the firewall for "clientless" VPN connections.
While the malware collected the firewall data, it's unclear whether the stolen data was actually transmitted to the attackers' command and control servers. "As of the date of publication, we have not discovered any evidence that the data collected had been successfully exfiltrated," Sophos said.
In a security advisory, Sophos said "multiple customers" were affected by the attack. The vendor released initial mitigations for the XG Firewall vulnerability the day after the attack was discovered and pushed out a hotfix on Saturday; the zero-day vulnerability was assigned a number, CVE-2020-12271.
Sophos published instructions on how to apply the hotfix for customers that do not have automatic updates enabled for their firewalls.
Sophos received praise from members of the infosec community for acting quickly and providing a detailed account of the attack and the remediation steps the vendor took. Kevin Beaumont, a security researcher with Microsoft's Threat Protection team, commended Sophos on Twitter for its "incredible openness."
However, other infosec experts were more critical of Sophos. For example, Matt Tait, an infosec expert who formerly served with the U.K.'s Government Communications Headquarters, questioned why the vendor had an undetected SQL injection vulnerability in its products; SQL injections are one of the most common security flaws in software and are considered relatively easy to detect and remediate.
It's unclear how many customers were affected by the Asnarök Trojan attack. A Sophos spokesperson responded to emails from SearchSecurity but did not provide any additional information about the scope of the attack.
On March 2, Thoma Bravo completed its acquisition of Sophos in a deal valued at nearly $4 billion. The acquisition, announced in October of last year, represents the latest in a long line of acquisitions by the private equity firm that includes Motus, Imperva, ConnectWise and others.







