
Maksim Kabakou - Fotolia
Attacks on Exim vulnerability continue one year later
Though the Exim mail transfer agent vulnerability was publicly disclosed in June 2019, a significant number of unpatched versions remain online and are at risk of attacks.
Despite multiple attacks against an Exim vulnerability that was publicly disclosed one year ago, hundreds of thousands of unpatched versions of the mail transfer agent remain.
Since that time, there have been a number of reports of exploitations and attacks using the vulnerability, most recently by Russian advanced persistent threat group Sandworm.
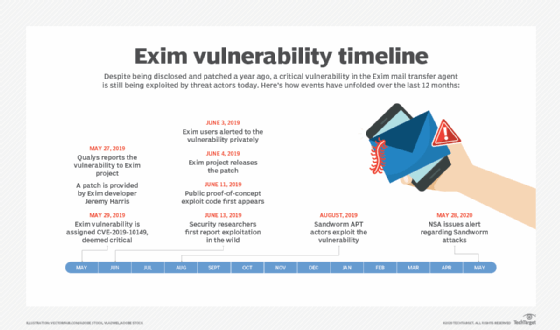
In a cybersecurity advisory released on May 28, the NSA revealed that the same Russian military hacking group that interfered in the 2016 presidential election had been exploiting the Exim vulnerability, also known as CVE-2019-10149, since at least August of 2019. "An unauthenticated remote attacker can use this vulnerability to send a specially crafted email to execute commands with root privileges, allowing the attacker to install programs, modify data and create new accounts," the NSA wrote in the advisory.
A commonly used open source program, Exim is essentially an email server designed to transfer messages. According to Rapid7 chief data scientist Bob Rudis, it's a simple but strong program that is typically deployed one of two ways: by getting Exim binaries and running them on a system, or by vendors including the code in appliance software.
Twenty-five years after its initial release, the Exim mail transfer agent is still quite popular. According to a 2019 study on mail servers from consulting firm E-Soft, Exim was found in more than 57% of the 1,775,165 servers queried.
"It gained a lot of popularity because of how small, easy and quick it is to use, set up and install," Rudis said. "But Exim has had a really sordid history with regards to security, so I am curious why any vendor would use it as a basis for any appliance out there. It's had multiple remote code [execution] vulnerabilities in the not-so-distant past, so I don't understand why people are using it at all."
Exim exploitation
One such RCE vulnerability is CVE-2019-10149; cloud security vendor Qualys disclosed the critical vulnerability to the Exim team and the Linux distros group on May 27 last year. It was then publicly disclosed in early June, and patches were made available.
However, threat actors were able to exploit the vulnerability just four days or so after disclosure due to a rich set of information about the Exim vulnerability and proof-of-concept code that was publicly available on GitHub, said Tenable research engineer Satnam Narang.
"As part and parcel of vulnerability disclosures, when you publish proof of concepts it's pretty likely an attacker will take advantage of that and target systems that are still online and still unpatched," Narang said.
Qualys senior director of product management Jimmy Graham said that while Exim versions 4.92 and later addresses the vulnerability, a large number of systems are still exposed to the flaw.
"Theoretically all vulnerable versions should be patched, but I wouldn't say I am surprised there are still unpatched versions," Graham said. "I know a lot of organizations struggle with visibility into vulnerabilities as well as the ability to patch these systems, so to me, it shows there's a lack of good asset management and vulnerability assessment. I'm assuming if these vulnerabilities were known to organizations, they'd have patched them by now."
Rudis said unpatched versions can be attributed to two problems: a lack of awareness of the vulnerability and a lack of communication. When vendors ship Exim as part of their appliances, they don't always inform users that Exim is running inside the product.
"If people are running Exim on their own, we can measure that when we're scanning, but these other appliance vendors are putting Exim in their appliances and you can't tell that it's necessarily running because they sort of mask it. So it's running on a lot of places on the internet that you wouldn't' expect," Rudis said. "Security is causing some of its own problems right now. Users don't know the appliance software is running Exim and may not be on top of updating. Mail just seems to be something no one seems to care about it until it's too late."
In addition, Narang said the fact that Exim is open source likely increased the volume of organizations running the MTA -- whether they know it or not.
"That's why we [Tenable] saw, when we initially published our blog [last year], about 4 million systems online that were accessible via Shodan. If it was closed source and you had to pay to use, you'd see less of a user base," Narang said.
Following the NSA alert, Tenable found close to half a million systems online that hadn't patched the Exim vulnerability, Narang said. He also noted that despite CVE-2019-10149 affecting versions 4.87-4.91 of Exim, the NSA advised upgrading to version 4.93 of the software because of other serious vulnerabilities that were discovered last year.
Additional security vendors have reported varying numbers of vulnerable systems.
In a blog post on Monday, threat intelligence vendor RiskIQ observed more than 900,000 vulnerable Exim instances as of May 1. "The vulnerabilities leveraged impact Exim Internet Mailer Version 4.87 to 4.92.," RiskIQ wrote in the blog.
In an email to SearchSecurity, BitSight senior security researcher Luis Grangeia said they've observed 250,000 systems that are potentially vulnerable.
Mail, in general, seems to be a great target for hackers to do what they want right now, says Rudis. "There are all kinds of email servers susceptible to something because people just don't patch. However, this happened to be one where there were enough targets that the NSA felt it was worth talking about."
Rudis said Exim comes up on Rapid7's vulnerability feed about every two months.
"After a while you have to think, there are this many problems and they're fixing this many problems this close together, you'd think people would stop running it," Rudis said.





